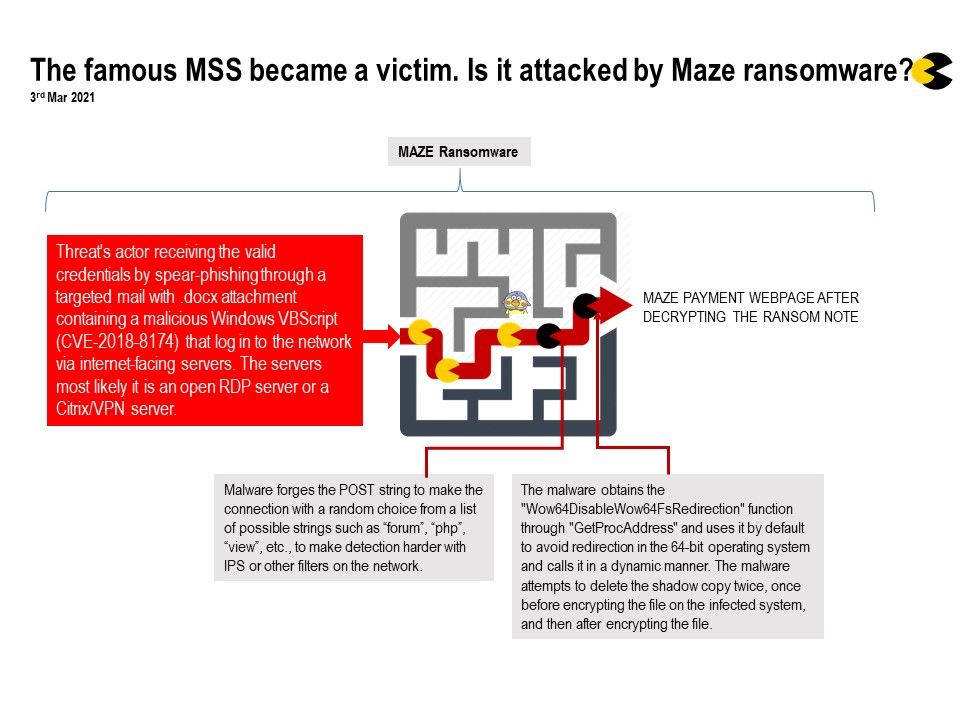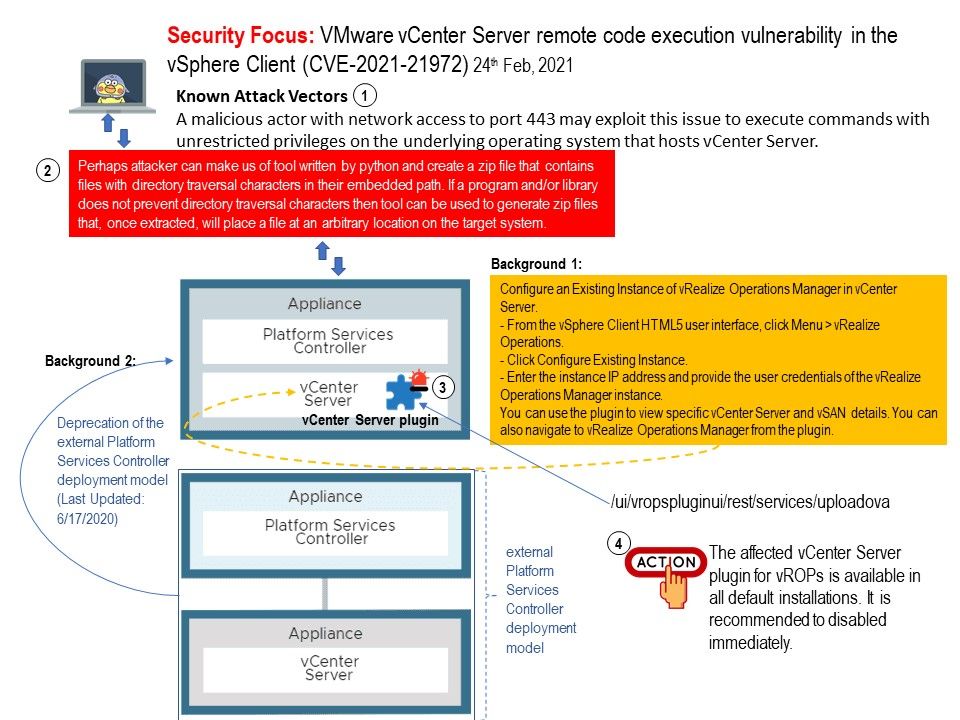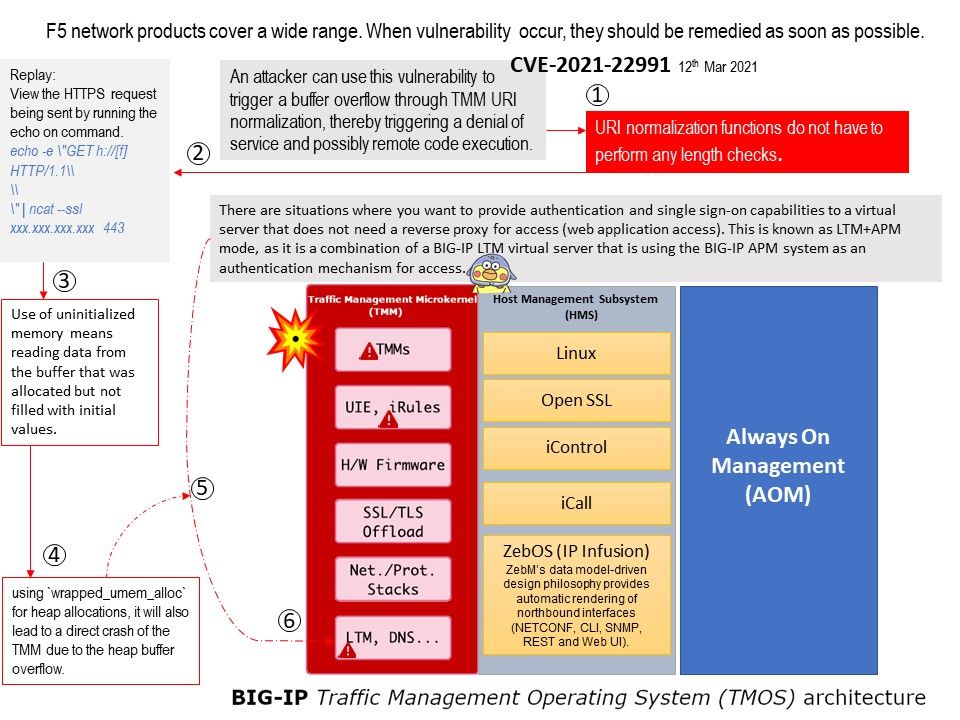
Preface: F5 network products are commonly deployed in data center and on-premises Internet facing infrastructure.
Background: F5 Network’s Traffic Management Operating System (TMOS) is not a separate operating system. It is the software foundation for all of F5’s network or traffic (not data) products including both physical or virtual platform. TMM is the core component of TMOS as it handles all network activities and communicates directly with the network switch hardware (or vNICs for VE (Virtual Edition)). TMM also controls communications to and from the HMS. Local Traffic Manager (LTM) and other modules run within the TMM.
Vulnerability details: Vulnerability found allow attacker use of uninitialized memory. Uninitialized memory means reading data from the buffer that was allocated but not filled with initial values. It means that the data are starting to be used before they are initialized. Finally using `wrapped_umem_alloc` for heap allocations, it will also lead to a direct crash of the TMM due to the heap buffer overflow.
Official announcement: https://support.f5.com/csp/article/K56715231


.jpg?width=1920&height=1080&fit=bounds)