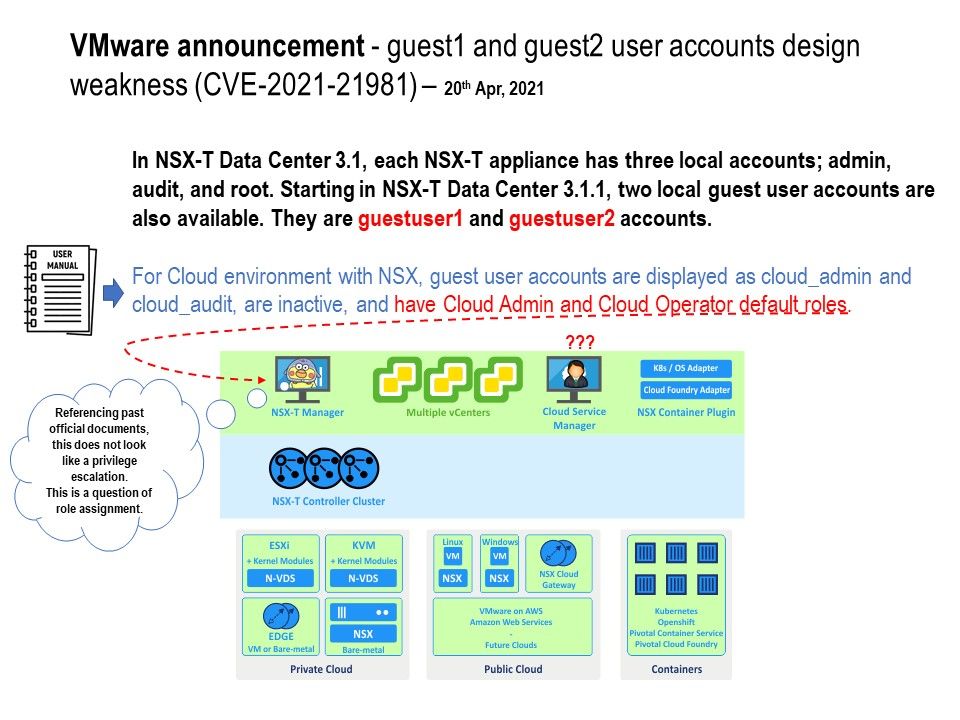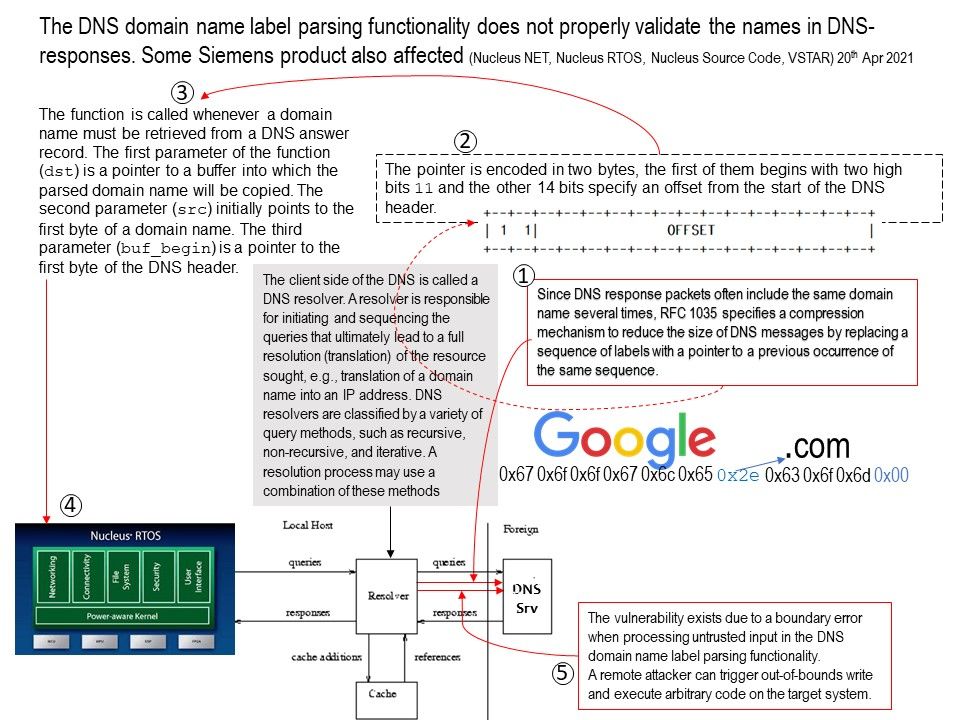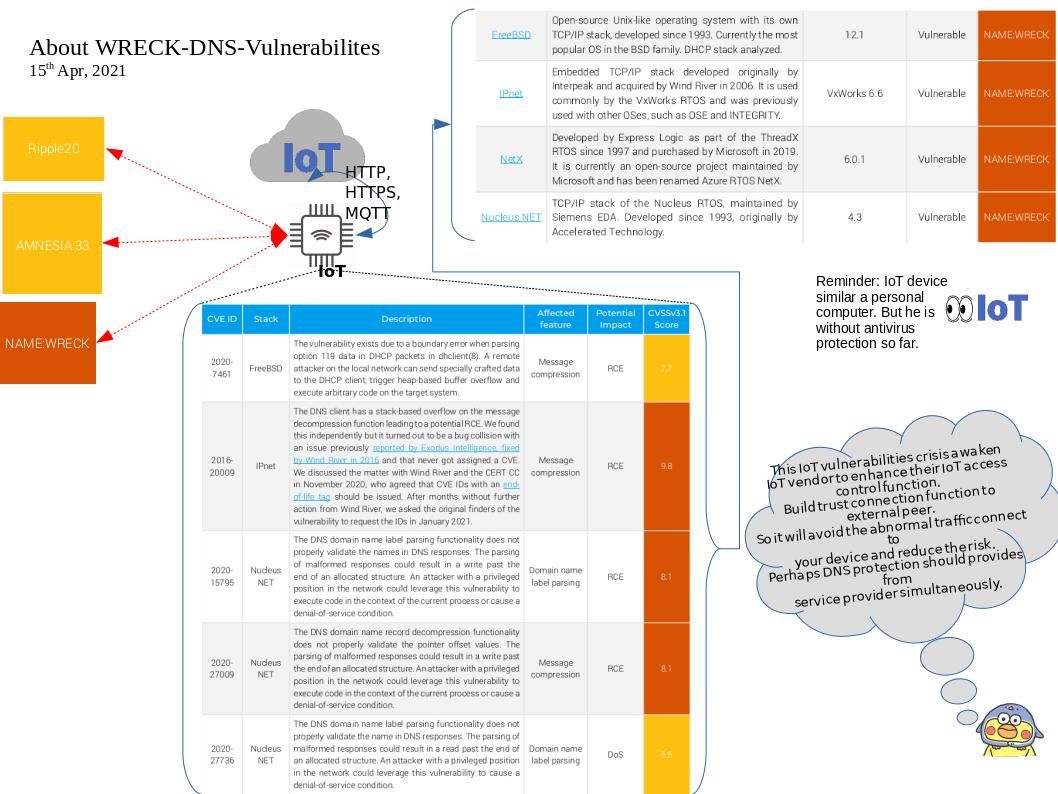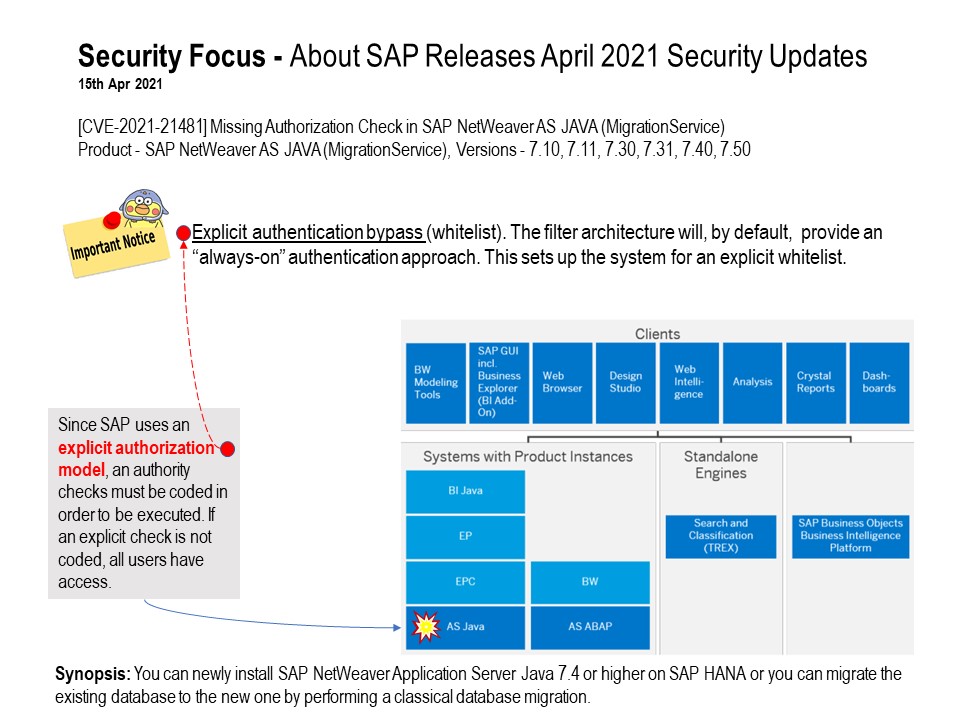
Preface: People say that when you walk through rough roads. A brand new road is waiting for you.
Synopsis: Due to the small size of IoT devices, the main component chips will include memory and storage. Even WiFi function. Technically, hardware resembles a car. Therefore, the software (OS) is equivalent a car driver. If the driver is healthy, the entire journey will become smoother. RTOS a key componet on IoT device platform. A reinvented RTOS for IoT needs to support industry-leading communications standards and protocols such as CAN, Bluetooth, Continua, ZigBee, Wi-Fi, and Ethernet, and deliver high-perfor- mance networking capabilities out of the box.
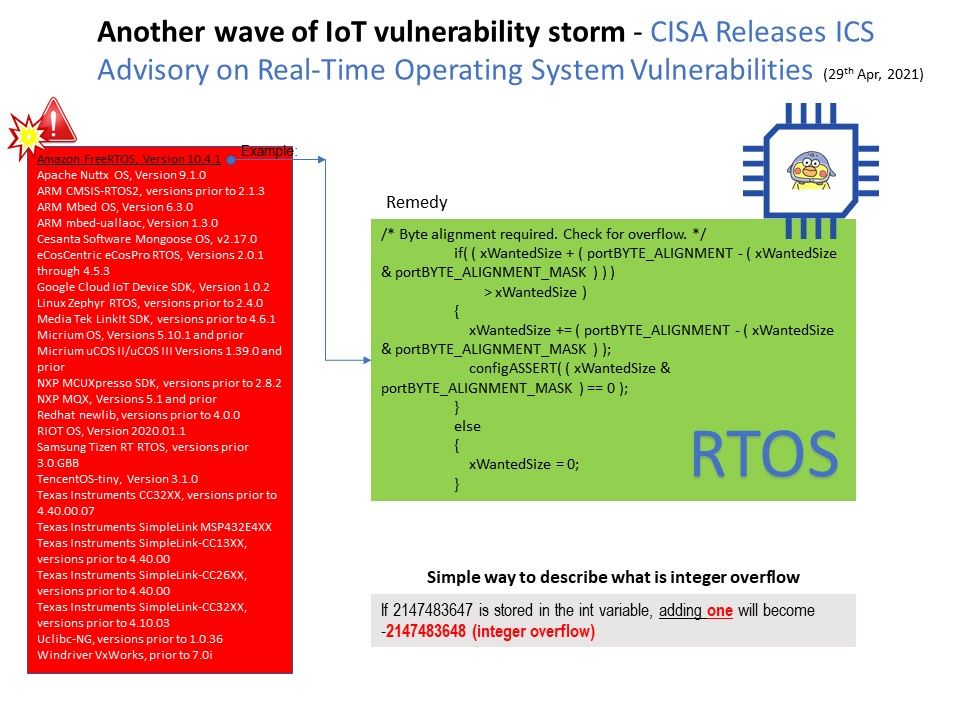
Security Focus: A simple way to describe what is integer overflow. If 2147483647 is stored in the int variable, adding one will become -2147483648. This is similar as integer overflow.
Status: Due to different RTOS platform encounter integer overflow vulnerability. Therefore CISA Releases ICS Advisory on Real-Time Operating System Vulnerabilities. An integer overflow with software programming mistake will amplifier the risk level. The worst case is let attacker conduct remote code execution.
Official announcement: Refer link – https://us-cert.cisa.gov/ics/advisories/icsa-21-119-04
.jpg)