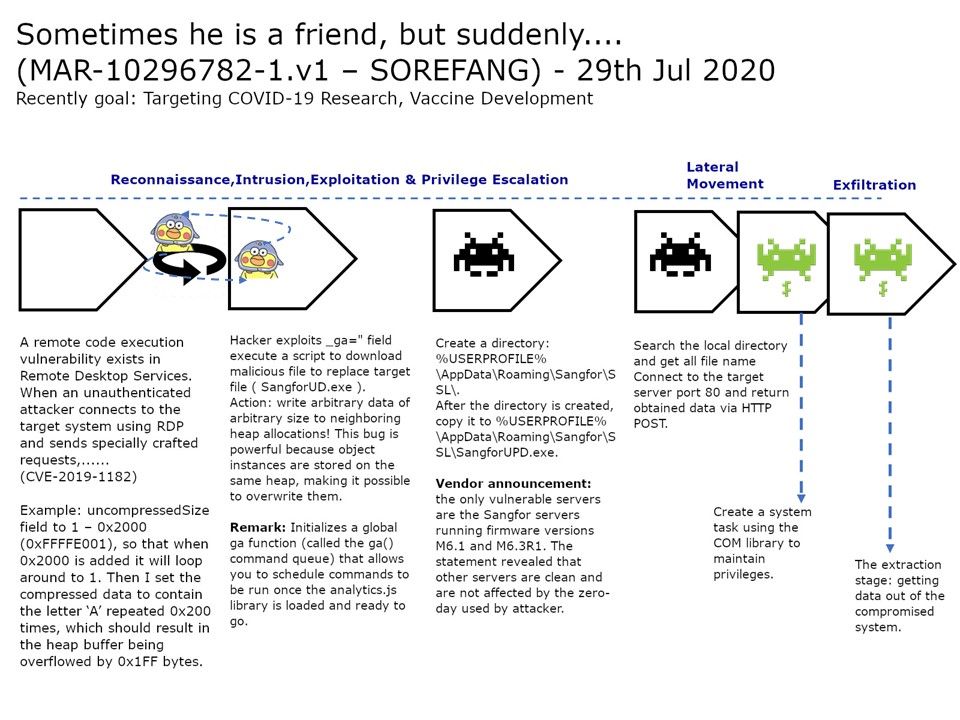
Preface: From some perspectives, the operating system and related components are designed to provide functionality. Therefore, network security does not involve its design scope. Even if network security has been included in their design. However, product technology changes with each passing day. Therefore, we often hear information about vulnerabilities.
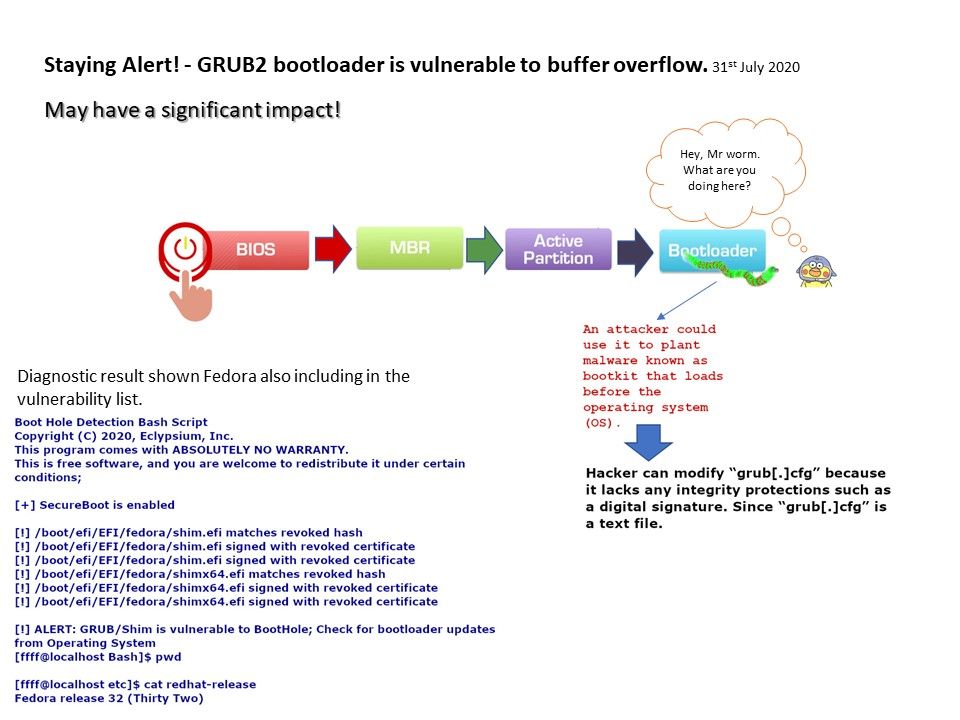
Why do I need a system bootloader?
The bootloader exists because there is no standardized protocol to load the first code, because it depends on the product design. Sometimes, the code can be loaded via a serial port, flash memory or even a hard disk. Locate it as a bootloader function.
Vulnerability details: The GRUB2 boot loader is vulnerable to buffer overflow, which results in arbitrary code execution during the boot process, even when Secure Boot is enabled.
An attacker could use it to plant malware known as bootkit that loads before the operating system (OS).
Hacker can modify “grub [.] cfg” because it lacks any integrity protections such as a digital signature. Since “grub [.] cfg” is a text file.
Official reference: GRUB2 bootloader is vulnerable to buffer overflow. Click on the URL for details – https://www.kb.cert.org/vuls/id/174059
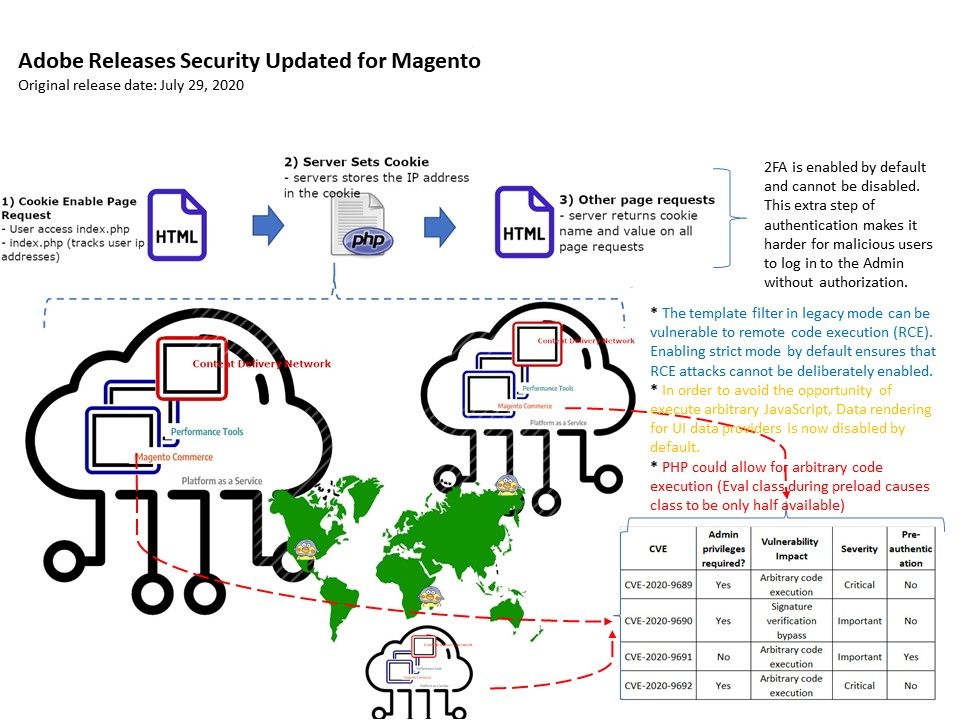
.jpg?width=1920&height=1080&fit=bounds)
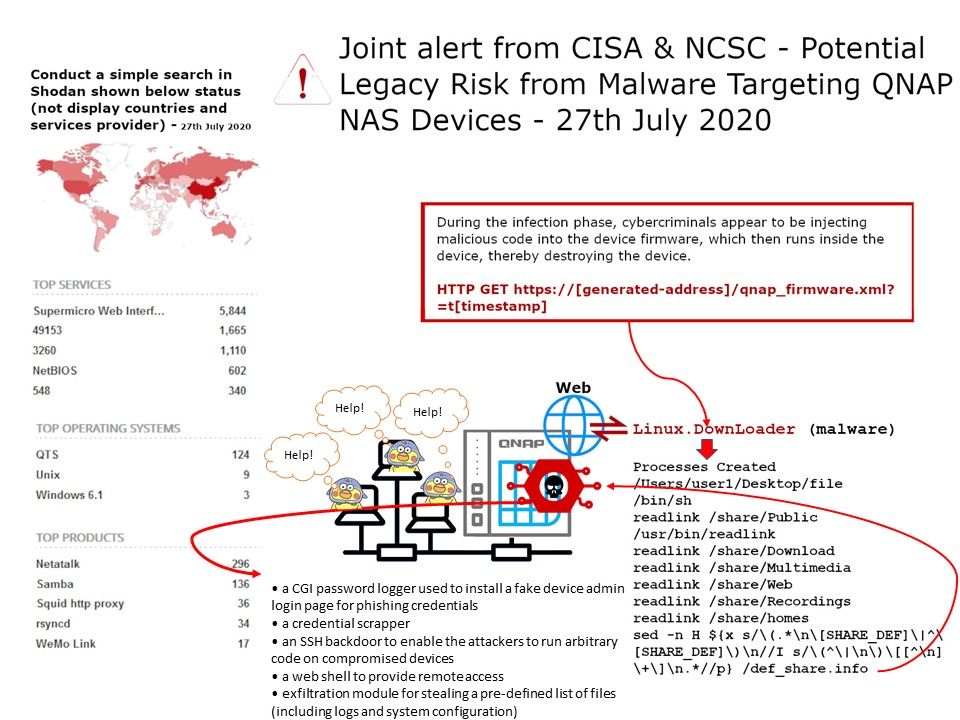
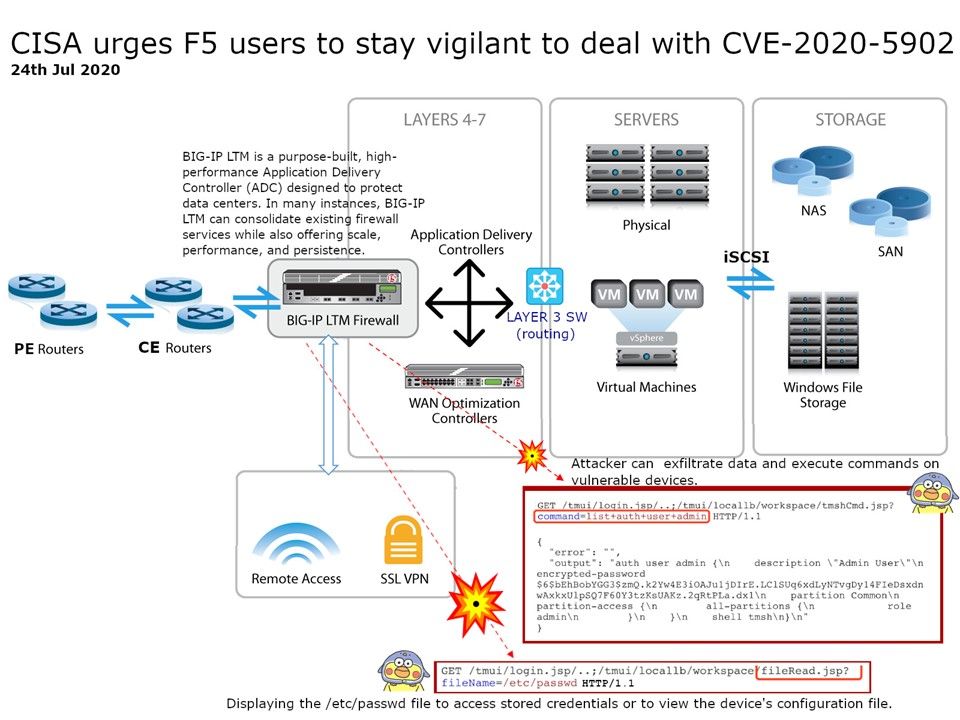
.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)
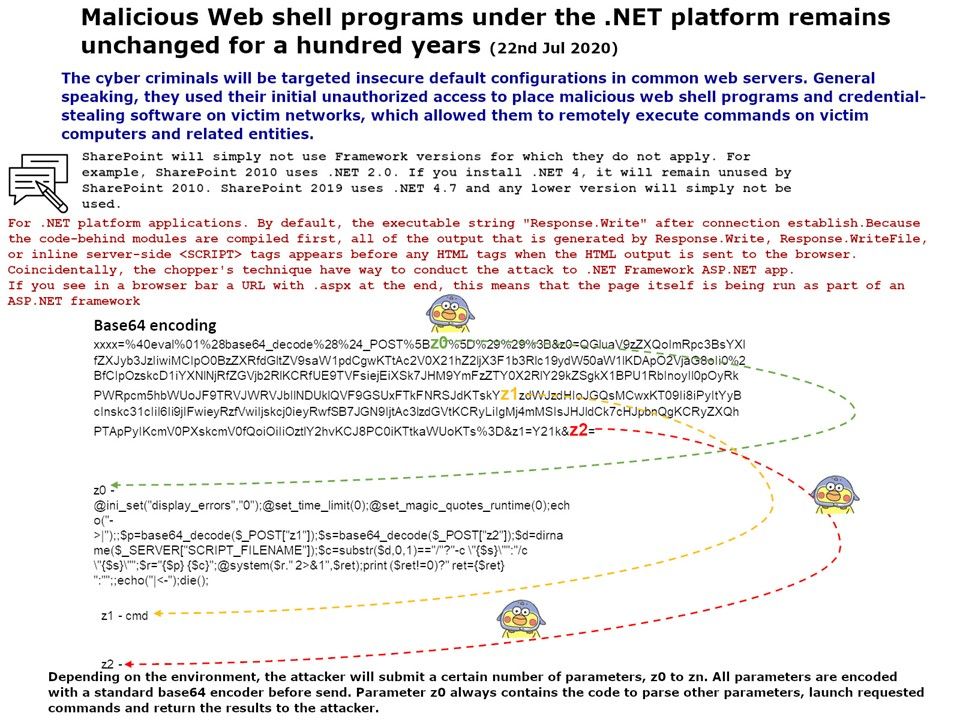
.jpg?width=1920&height=1080&fit=bounds)