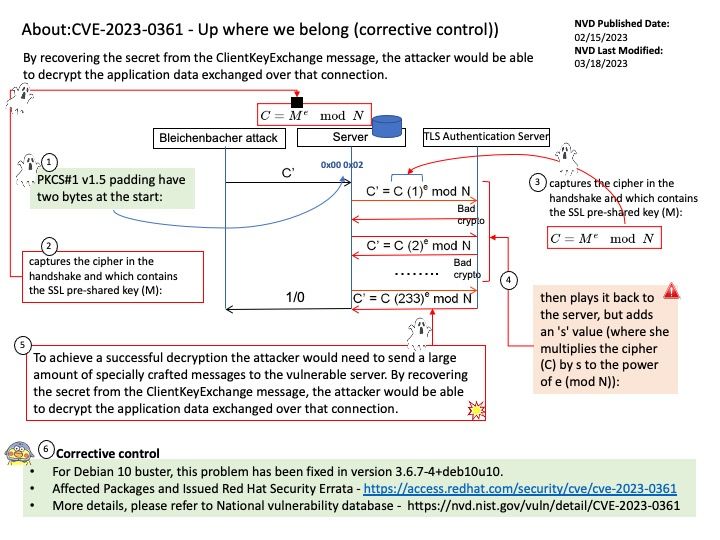
Preface: The Android operating system is mainly based on Linux, and its kernel is written in C language. Some modifications may have been done using the C++ language.
Background:
Get Group State – Different software uses different way (see below):
- only need to input the queried union information unionID
- need unionID and zoneID; query information about the state of the union binding the group Return information and result:
static void GetGroupState (String unionID, String zoneID = “”, String extraJson = “”) ;
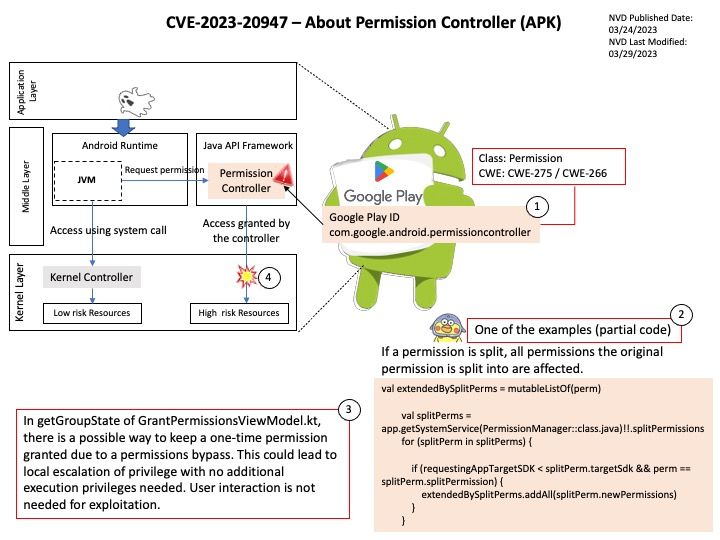
Vulnerability details: In getGroupState of GrantPermissionsViewModel.kt, there is a possible way to keep a one-time permission granted due to a permissions bypass. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.
If a permission is split, all permissions the original permission is split into are affected.
For <= N_MR1 apps all permissions of the groups of the requested permissions are affected
Affected Products: AndroidVersions: Android-12 Android-12L Android-13Android
Official announcement: For details, see the link – https://nvd.nist.gov/vuln/detail/CVE-2023-20947