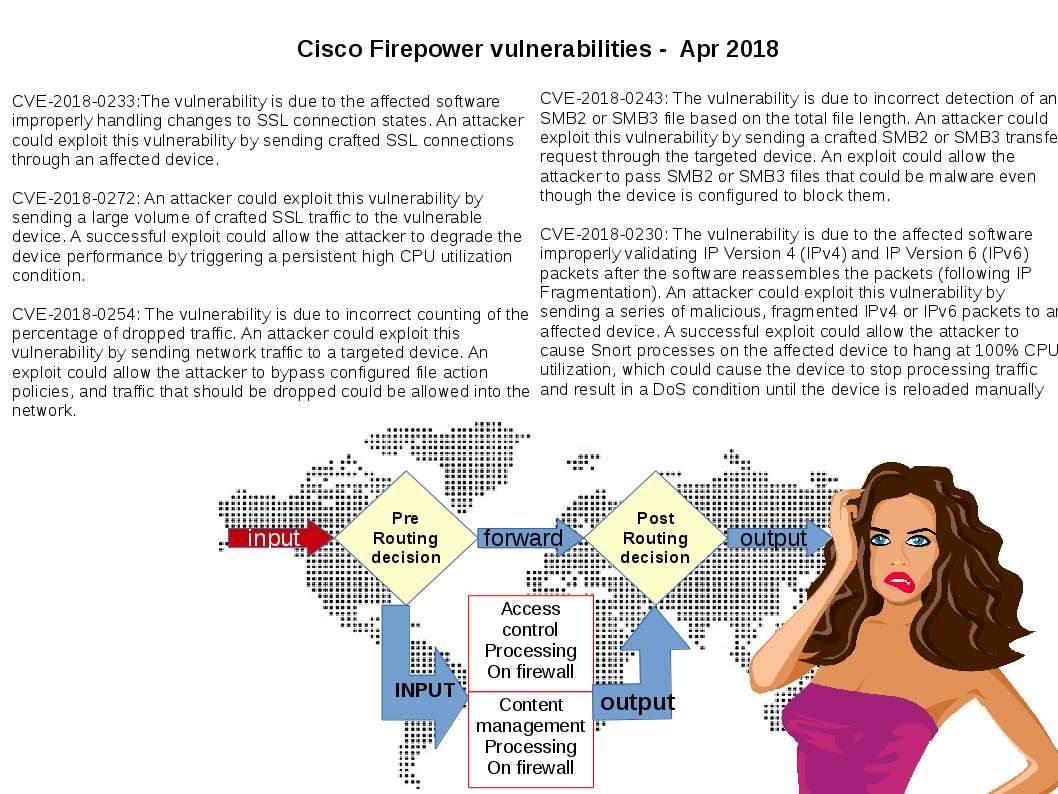
Preface:
PHP is a widely-used open source general-purpose scripting language that is especially suited for web development and can be embedded into HTML.
Security concern by security experts
The security issues are typically exposed when PHP code makes use of system-level calls.
Found critical security problem today! – Original release date: April 27, 2018
The Multi-State Information Sharing & Analysis Center (MS-ISAC) has released an advisory on multiple Hypertext Preprocessor (PHP) vulnerabilities. An attacker could exploit one of these vulnerabilities to take control of an affected system.
NCCIC encourages users and administrators to review MS-ISAC Advisory 2018-046 and the PHP Downloads page and apply the necessary updates.
See whether any short term remediation can take before upgrade?
1.Restrict PHP Information Leakage
expose_php=Off
2.Disable Remote Code Execution
Allow_url_fopen=Off
allow_url_include=Off
3.Not show errors to the visitors
(/etc/php.d/security.ini file)
log_errors=On
error_log=/var/log/httpd/php_scripts_error.log
4.Disable Dangerous PHP Functions (php.ini)
disable_functions =exec,passthru,
shell_exec,system,proc_open,popen,curl_exec,
curl_multi_exec,parse_ini_file,show_source
5.Upload Files (/etc/php.d/ directory)
file_uploads=Off
6.Control File System Access
always keep the open_basedir directive set to the /var/www/html directory.
open_basedir=”/var/www/html/”
7.Control the POST Size (/etc/php.d/security.ini)
post_max_size=1k
— End —