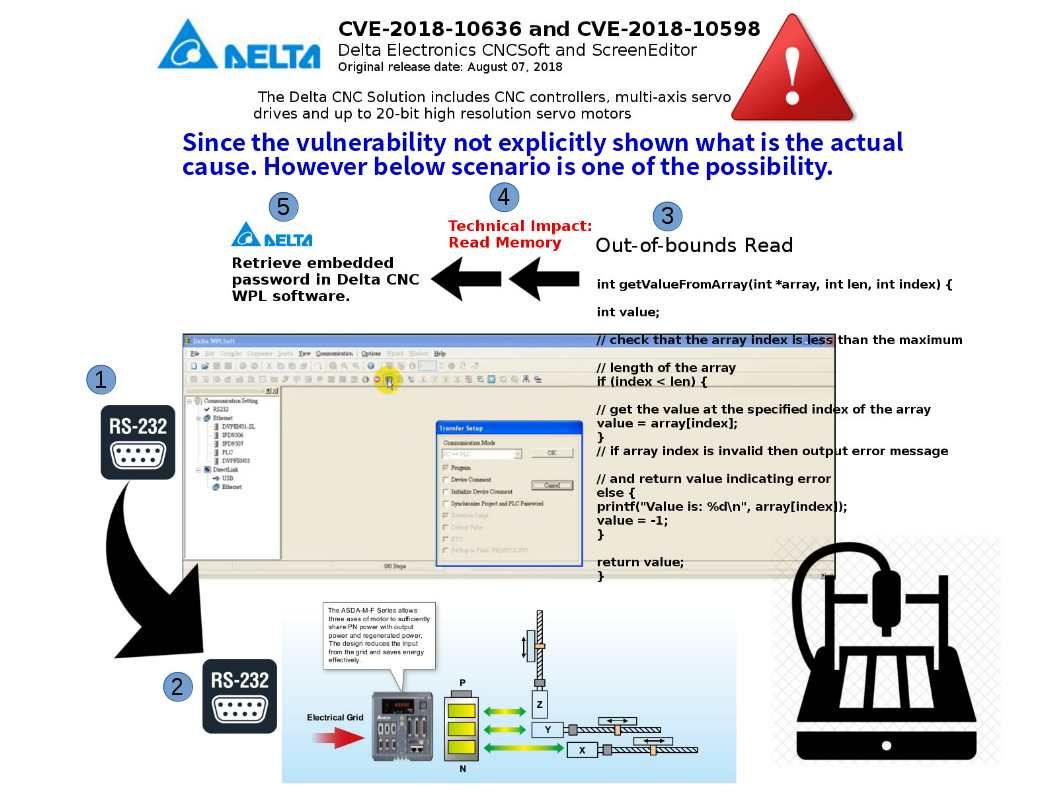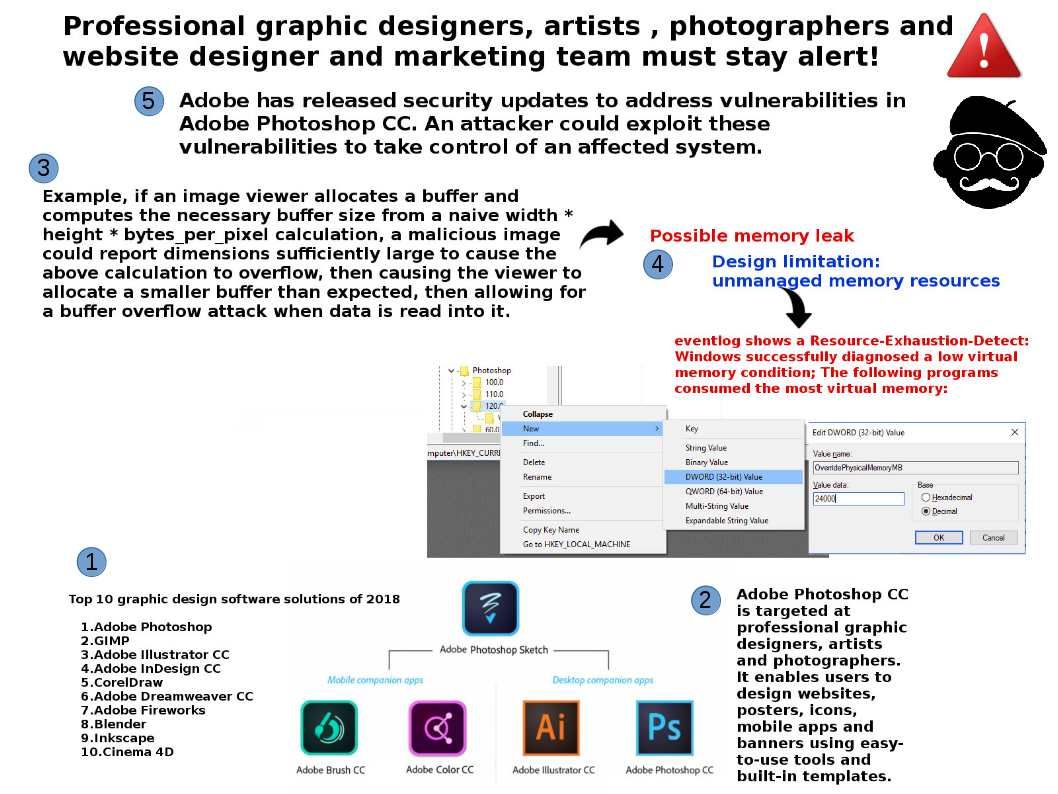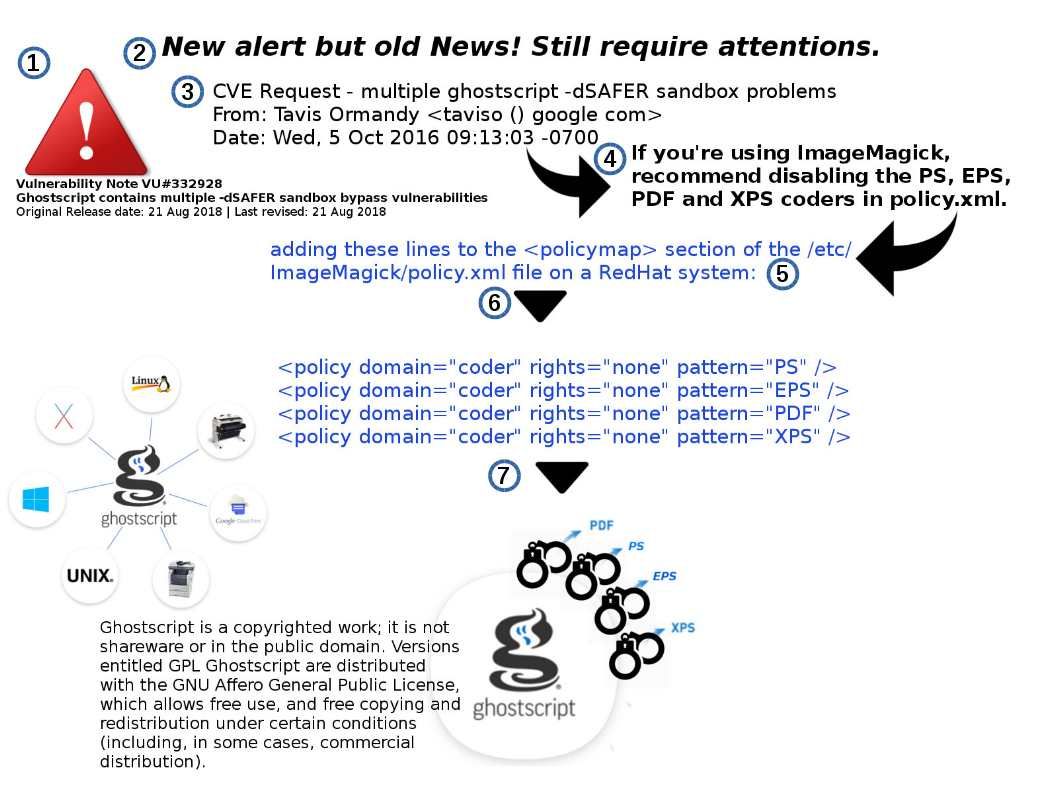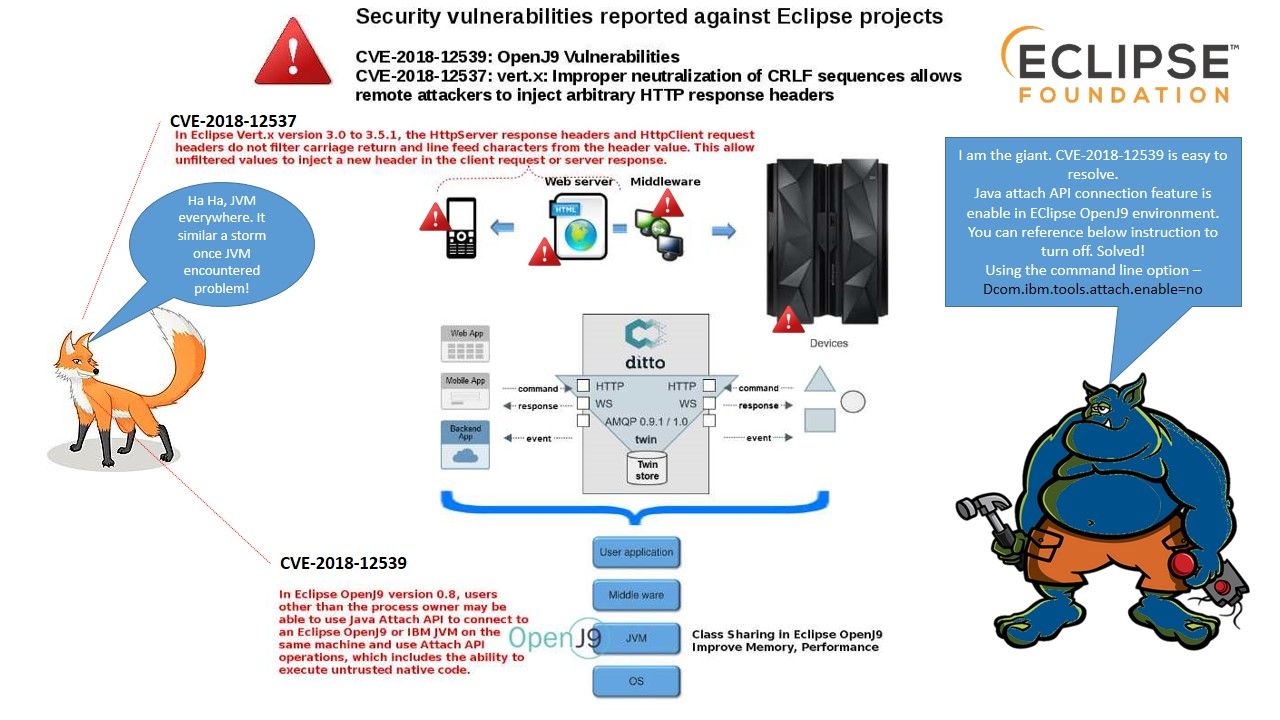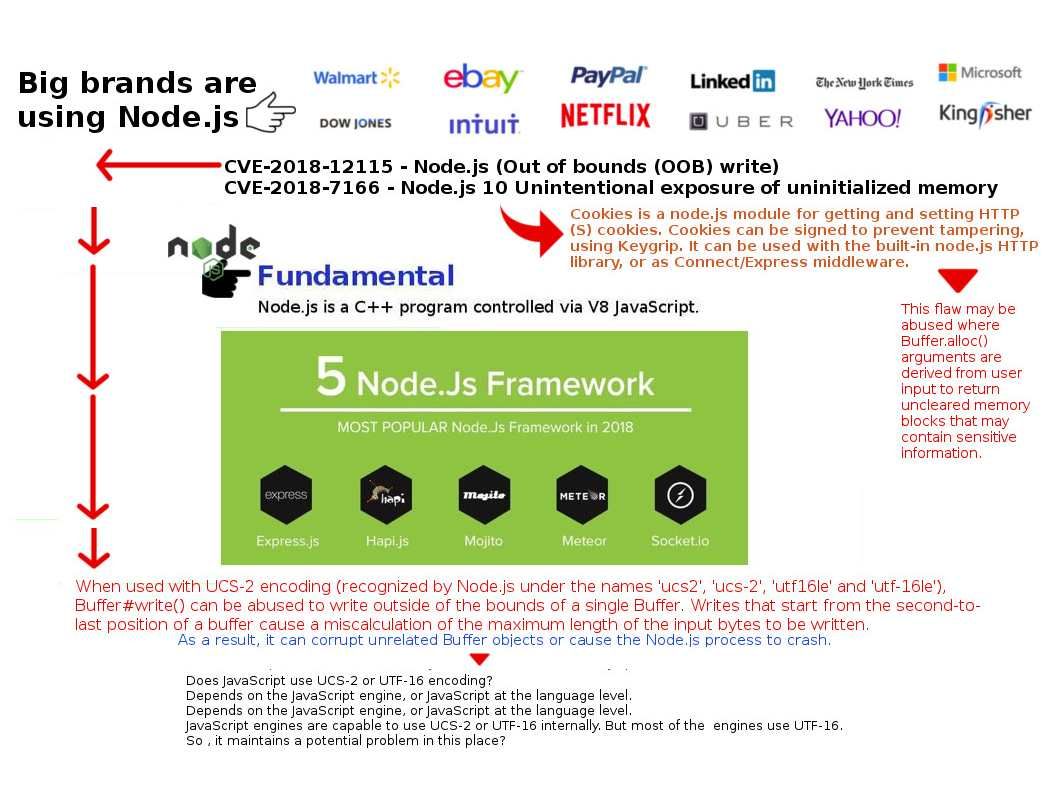
Retropective of the programming history, JavaScript was used primarily for client-side scripting, in which scripts written in JavaScript are embedded in a webpage’s HTML and run client-side by a JavaScript engine in the user’s web browser. Node js programming technique lets developers use JavaScript to write command line tools thus transfer script programming function to server-side. It let the programming scripts execute on server-side to produce dynamic web page content before the page is sent to the user’s web browser. As a result, it provides equivalent asynchronous I/O functionality (also non-sequential I/O). Asynchronous is a form of input/output processing that permits other processing to continue before the transmission has finished. But node js itself is difficult ro avoid traditional design bottleneck. For instance memory leakage issues. Found 2 issue on node js this month. However similar Buffer ucs2 and utf16le encoding issue found on 2012. For instance memory leakage issues. Found 2 issue on node js this month. However such similar Buffer ucs2 and utf16le encoding issue was found on 2012.
Official details shown below URL: https://nodejs.org/en/blog/vulnerability/august-2018-security-releases/