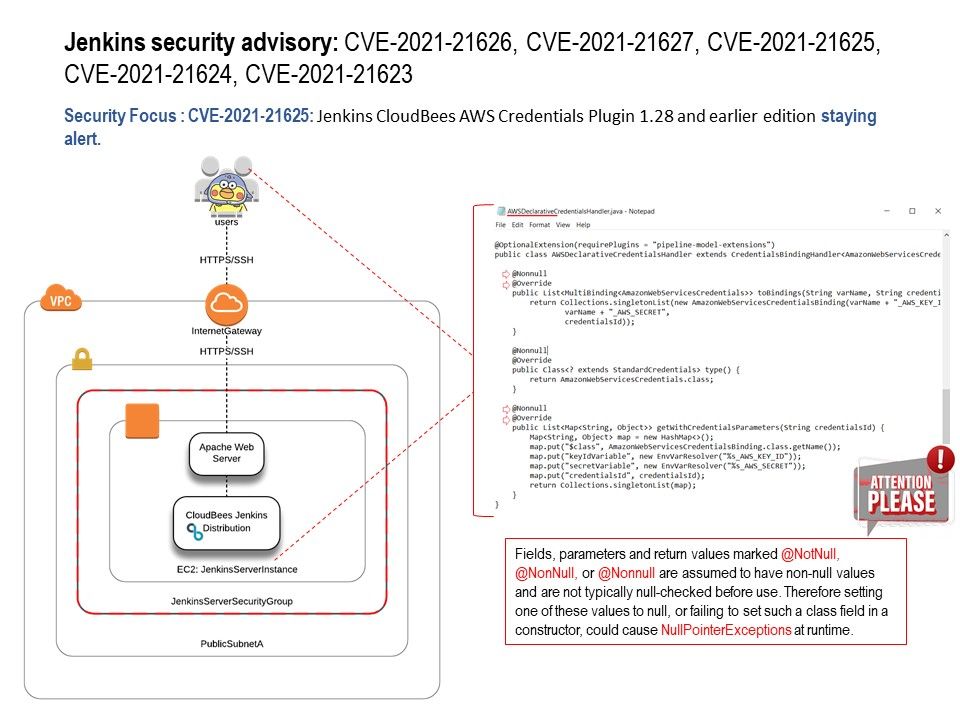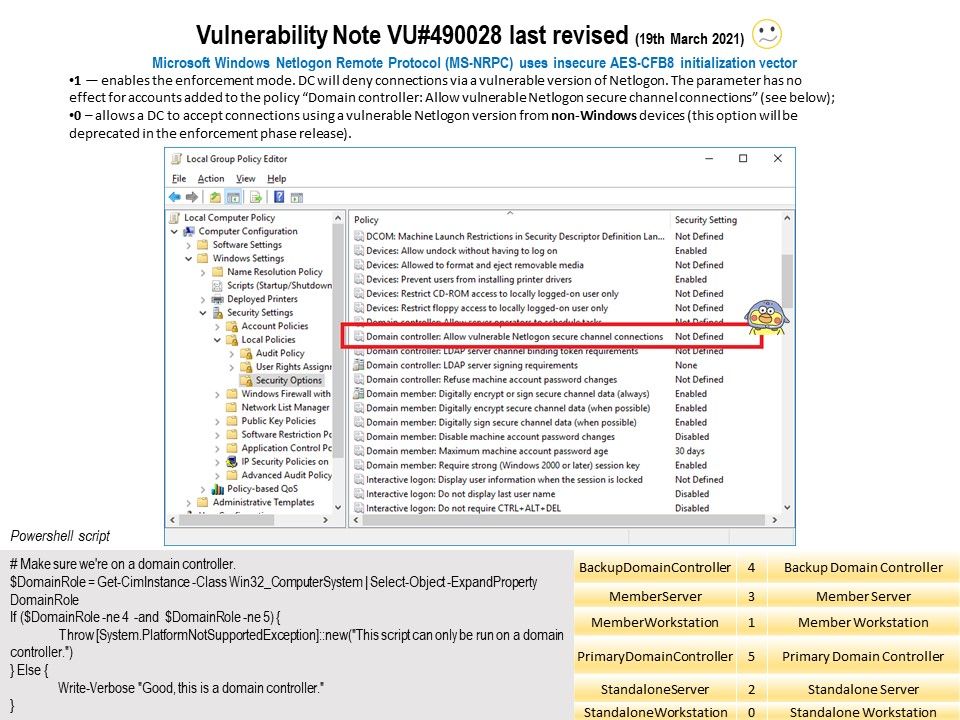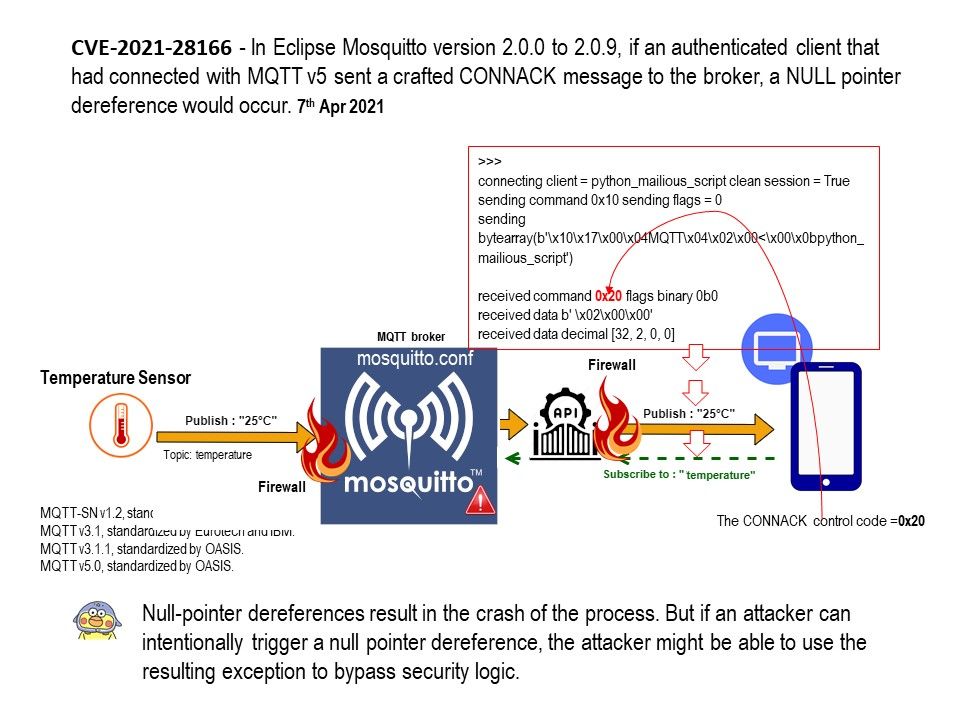
Preface: The two main changes to the CONNACK message between MQTTv3.1.1 and MQTTv5 are the enhanced reason codes and the properties field.
Background: MQTT is an OASIS standard messaging protocol for the Internet of Things (IoT). It is designed as an extremely lightweight publish/subscribe messaging transport that is ideal for connecting remote devices with a small code footprint and minimal network bandwidth. Furthermore, the MQTT CONNECT and response messages (CONNACK) have been greatly enhanced in MQTTv5 with the addition of the properties field. The properties field allows for a large increase in the information that can be exchanged between client and server on connection establishment compared to MQTT v3.1.1.
Vulnerability details: In Eclipse Mosquitto version 2.0.0 to 2.0.9, if an authenticated client that had connected with MQTT v5 sent a crafted CONNACK message to the broker, a NULL pointer dereference would occur. Null-pointer dereferences result in the crash of the process. But if an attacker can intentionally trigger a null pointer dereference, the attacker might be able to use the resulting exception to bypass security logic.
Official announcement: Please refer to link – https://bugs.eclipse.org/bugs/show_bug.cgi?id=572608
.jpg?width=1920&height=1080&fit=bounds)
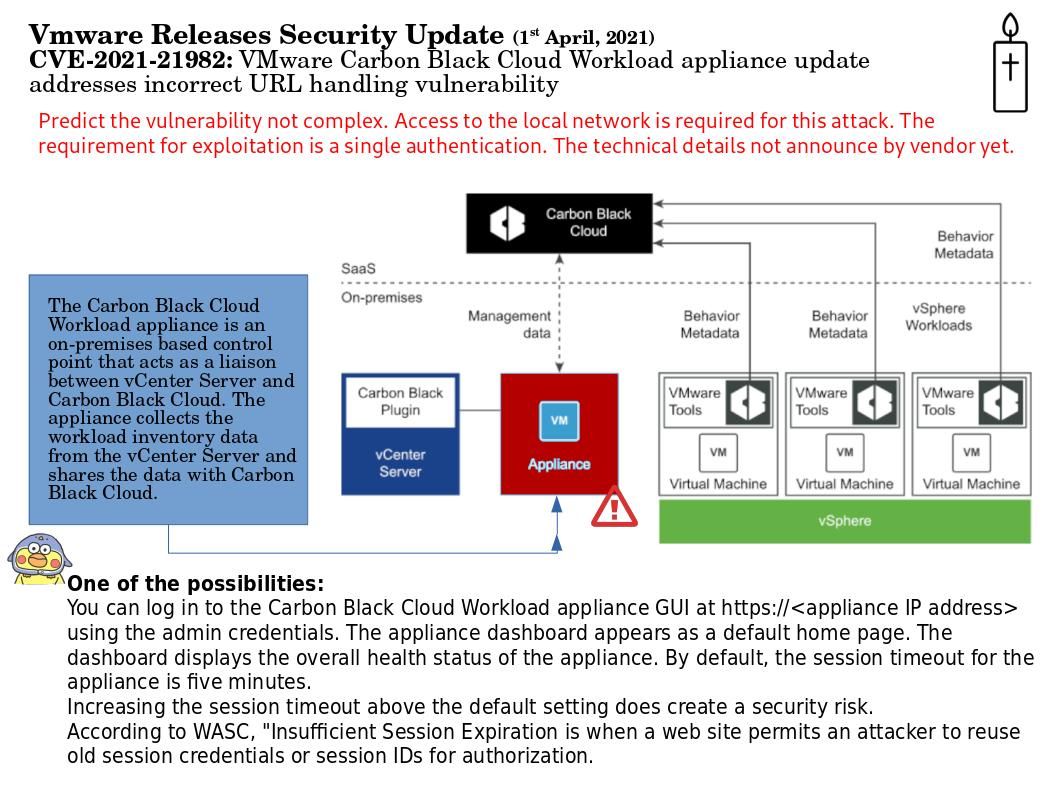
.jpg?width=1920&height=1080&fit=bounds)