Preface: About 20 years ago, people know java is unsafe. Perhaps of technology trend, so whatever the design appyling java language. The flexibility and easy to use will let people contempt about awareness of cyber security. While Java is considered relatively safe because it is a server side language, there are still multiple ways to attack and access secure code you’d like to remain private.
Background: The Spring Framework is an application framework and inversion of control container for the Java platform. The framework’s core features can be used by any Java application, but there are extensions for building web applications on top of the Java EE platform.
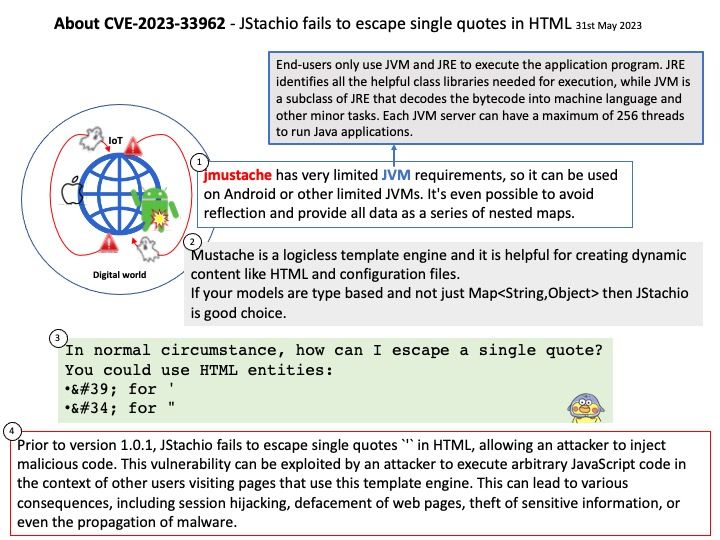
Mustache is a logicless template engine and it is helpful for creating dynamic content like HTML and configuration files.
If your models are type based and not just Map then JStachio is good choice.
Ref:End-users only use JVM and JRE to execute the application program. JRE identifies all the helpful class libraries needed for execution, while JVM is a subclass of JRE that decodes the bytecode into machine language and other minor tasks. Each JVM server can have a maximum of 256 threads to run Java applications.
Vulnerability details: Prior to version 1.0.1, JStachio fails to escape single quotes ' in HTML, allowing an attacker to inject malicious code. This vulnerability can be exploited by an attacker to execute arbitrary JavaScript code in the context of other users visiting pages that use this template engine. This can lead to various consequences, including session hijacking, defacement of web pages, theft of sensitive information, or even the propagation of malware.
Solution: Version 1.0.1 contains a patch for this issue.
Workaround: To mitigate this vulnerability, the template engine should properly escape special characters, including single quotes. Common practice is to escape ' as '. As a workaround, users can avoid this issue by using only double quotes " for HTML attributes.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-33962