Preface:
The art of driving a car in a race comes from the ability to maximize the performance of the car. Everything you do on a track takes skill when you are reaching the limits of performance. This concept also suitable on computer design.
Japan supercomputer rating:
Fujitsu ranks supercomputers seventh in the world.
Cores: 391,680
Memory: 417,792 GB
Processor: Xeon Gold 6148 20C 2.4GHz
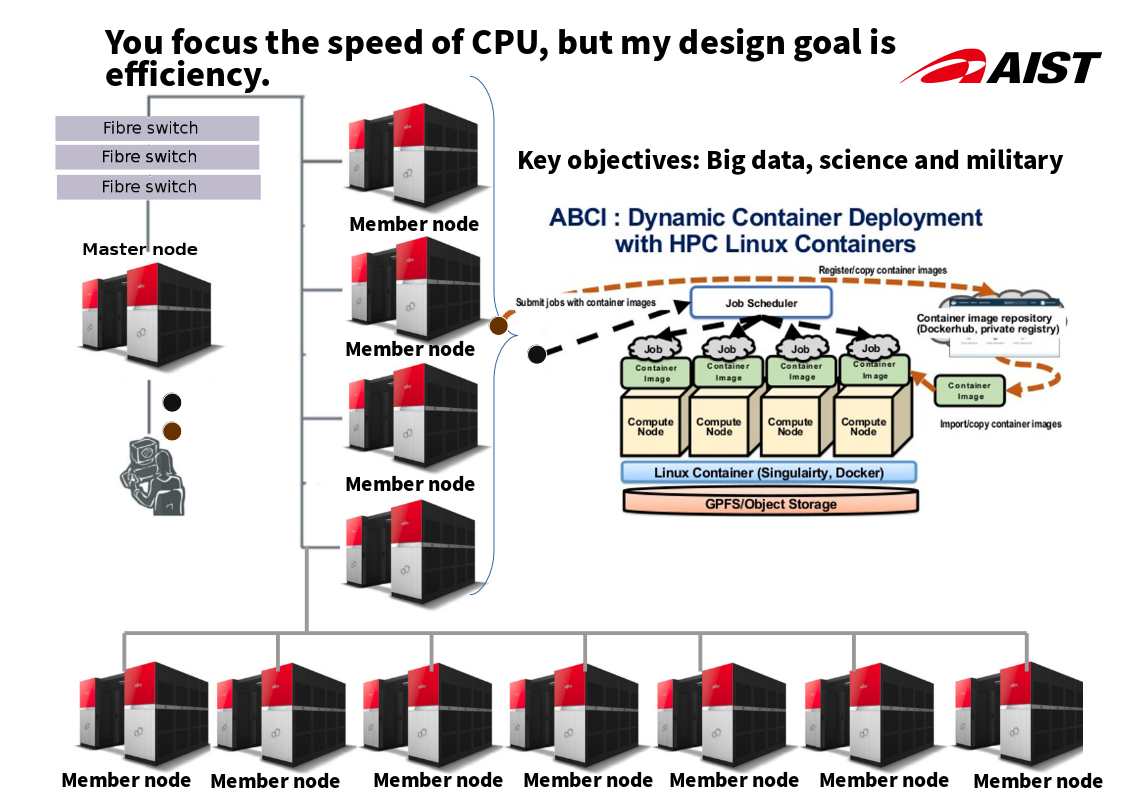
Historical background:
The traditional supercomputer architecture contains HIGH SPEED VECTOR PROCESSORS, crossbar switch, LPARs architecture. Since CPU speed is most important element on calculation. Meanwhile LPARs design can let system allocate the function feature and requirements.
Remark: Logical partitions (LPARs) are, in practice, equivalent to separate mainframes.
Synopsis:
But the military, scientific and public safety requirements of the world in today more demanding. The traditional Supercomputer LPARs design still have space for improvement. And therefore Linux high performance cluster and docker infrastructure become a key components. It boostup the system efficiency. Even though Fujitsu ranks supercomputers seventh in the world. But it maximum the efficiency.