Preface: Enable/Disable AMD virtualization in BIOS
- Open BIOS menu.
- Go to Advanced- > IOMMU and enable/disable AMD IOMMU. B. AMD SVM.
- Go to Advanced -> SVM Mode and enable/disable AMD SVM.
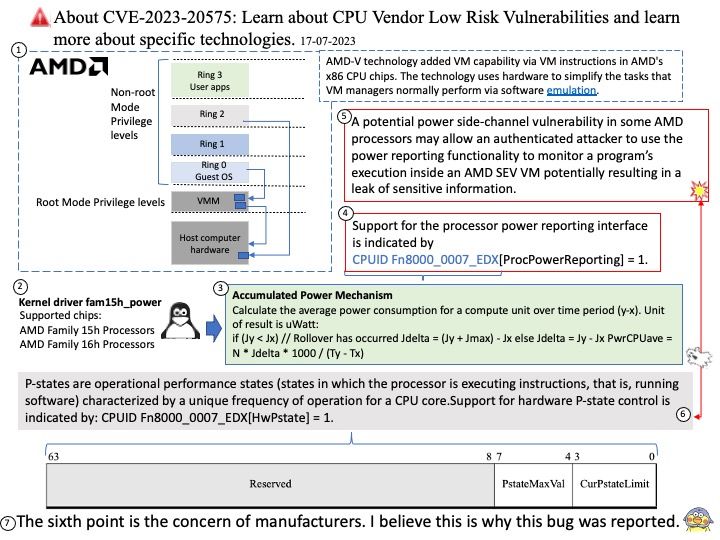
Background: AMD-V technology added VM capability via VM instructions in AMD’s x86 CPU chips. The technology uses hardware to simplify the tasks that VM managers normally perform via software emulation.
Prior to starting an encrypted VM, software must enable MemEncryptionModEn through MSR C001_0010 (SYSCFG). SEV may then be enabled on a specific virtual machine during the VMRUN instruction if the hypervisor sets the SEV enable (bit 1) in VMCB offset 090h.
Vulnerability details: A potential power side-channel vulnerability in some AMD processors may allow an authenticated attacker to use the power reporting functionality to monitor a program’s execution inside an AMD SEV VM potentially resulting in a leak of sensitive information.
This attack exploit by attacker does not seem to be a particularly novel attack as it uses the same technique as the Platypus attack from 2020. One difference from the Platypus attack is this reported attack is used against an AMD SEV virtual machine.
2022-10-27 CVE assigned
2023-07-11 +257 days Released to public
Official announcement: For details, please refer to the links:
https://nvd.nist.gov/vuln/detail/CVE-2023-20575
https://www.amd.com/en/resources/product-security/bulletin/amd-sb-3004.html