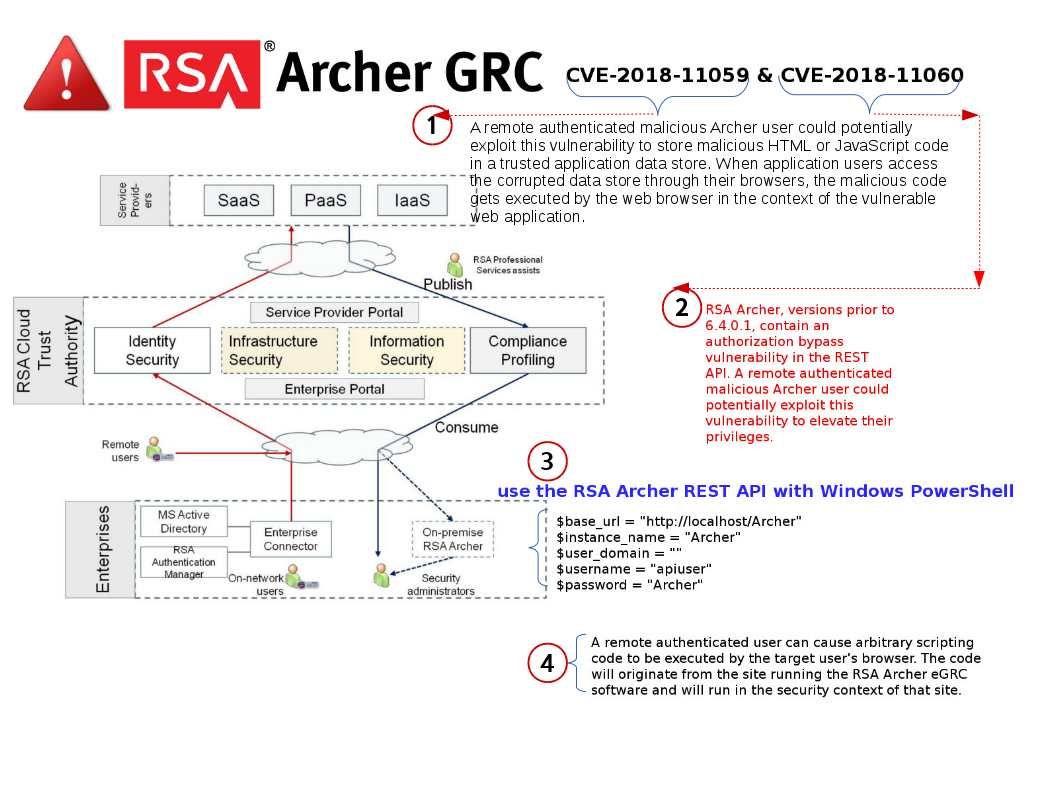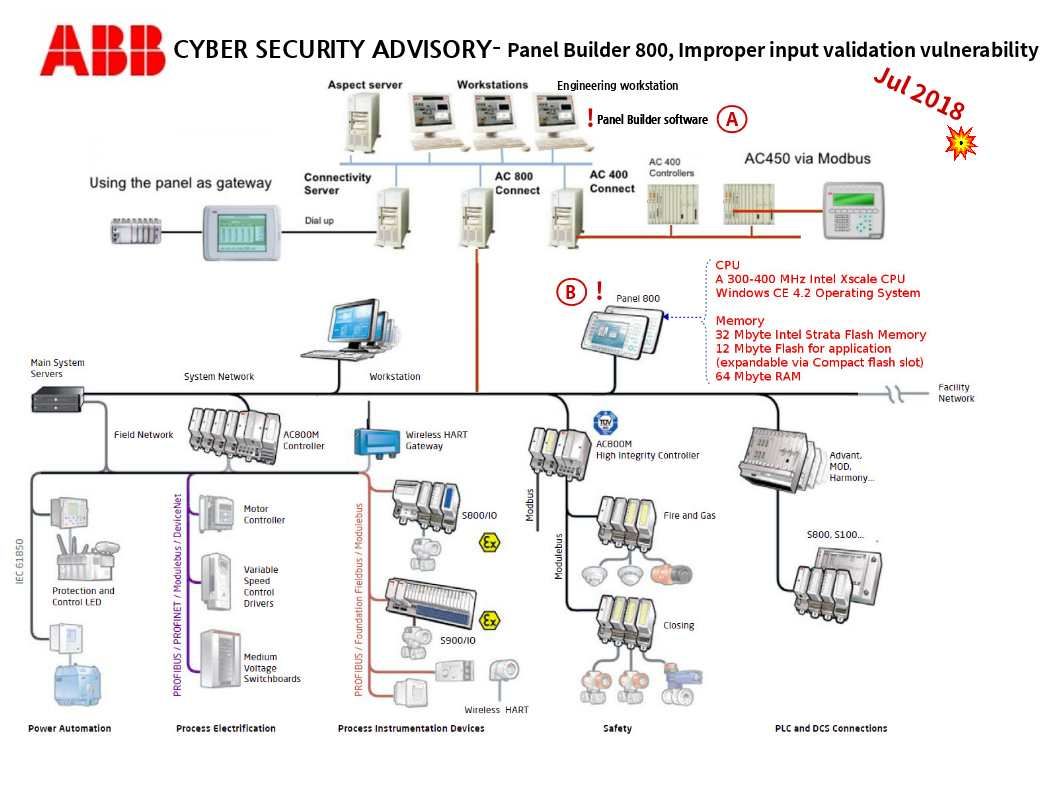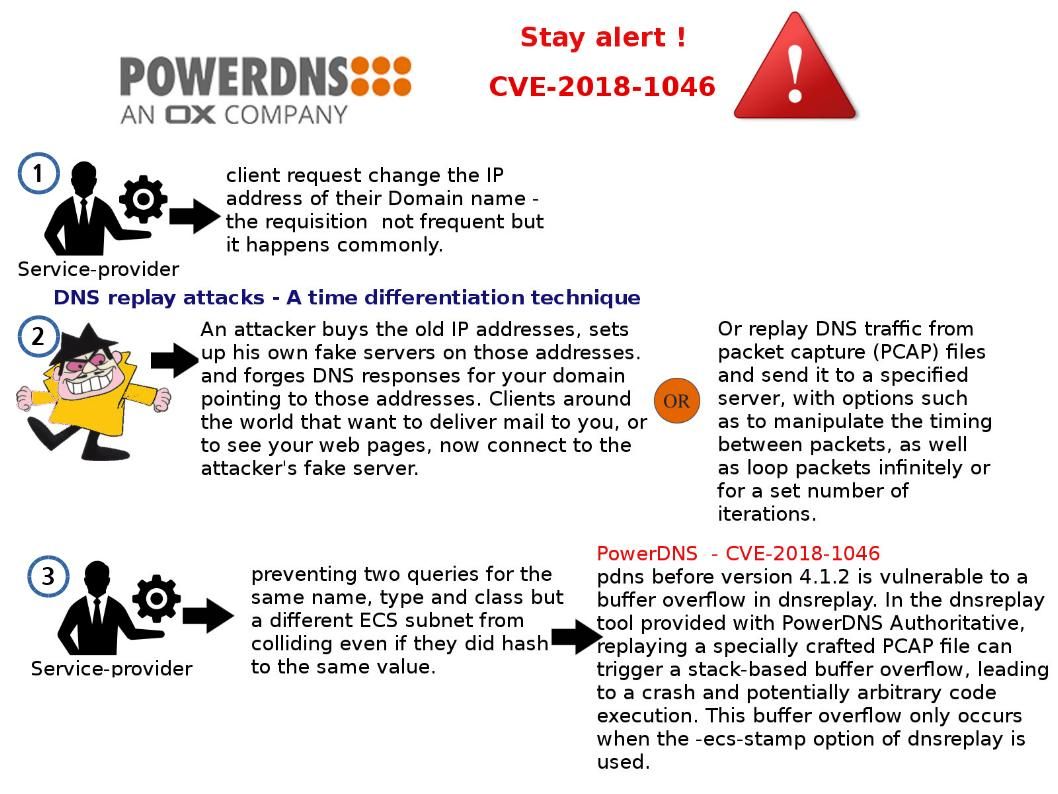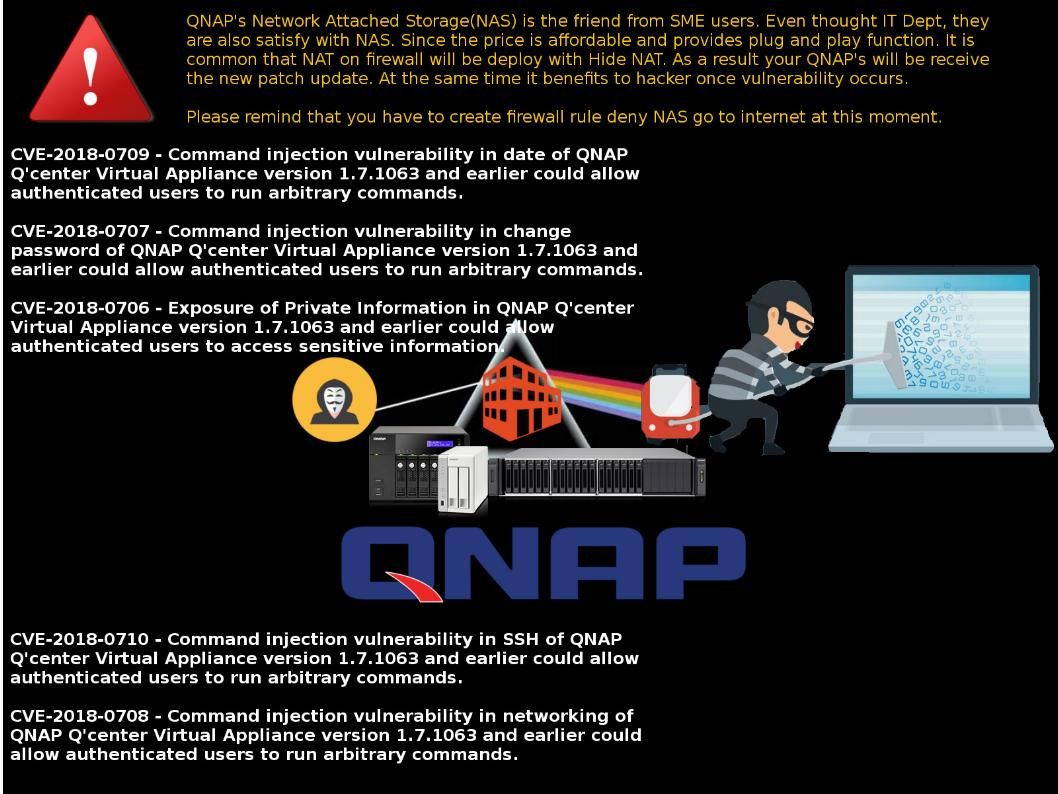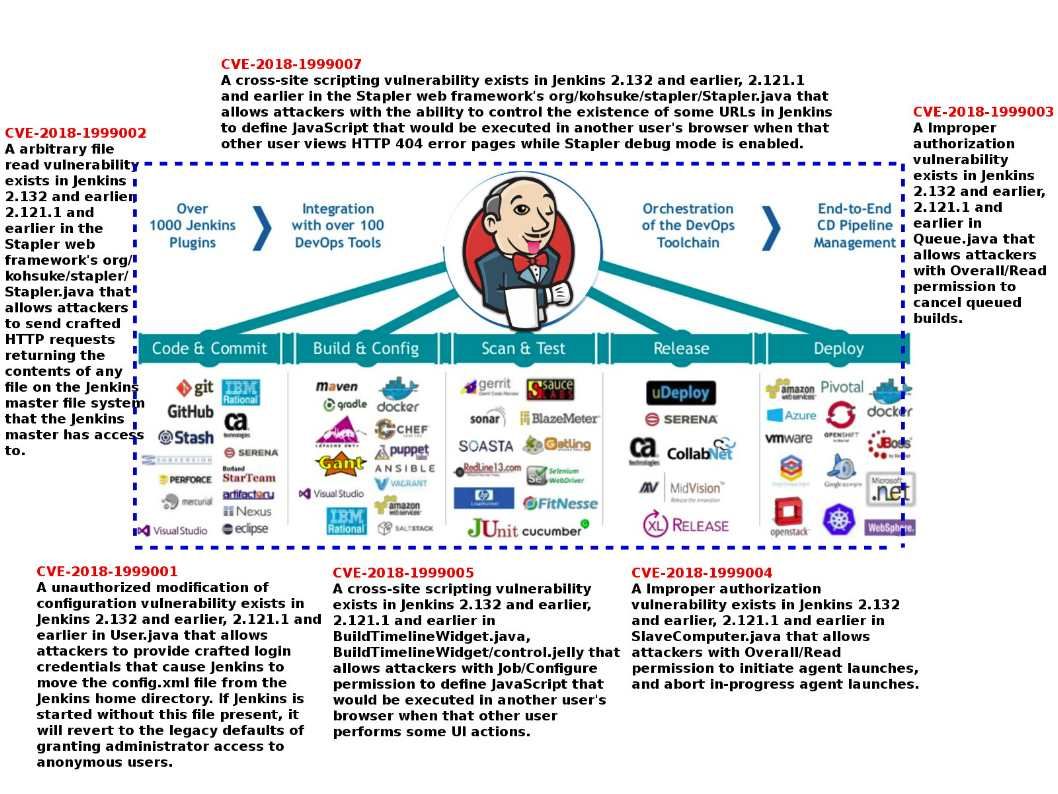
Jenkins is the leading open-source automation server. Built with Java, it provides over 1000 plugins to support automation. Is it a robot?
Basically, Jenkins is commonly used for building projects, running tests to detect bugs and other issues as soon as they are introduced, static code analysis and deployment.
For instance combining Jenkins and Docker together can bring improved speed and consistency to your automation tasks.
That is you can configure Jenkins to build Docker Images based on a Dockerfile. You can use Docker within a CI/CD pipeline, using Images as a build artefact that can be promoted to different environments and finally production. Usually, the freestyle automated job can create to accomplish a specific task in the CI pipeline, it can be compile the code, run integration tests or deploy application.
Remark:
A complete CI pipeline is made up of three major parts: Integration: Build code and run unit tests.
Delivery: Deploy your application to a staging or production environment.
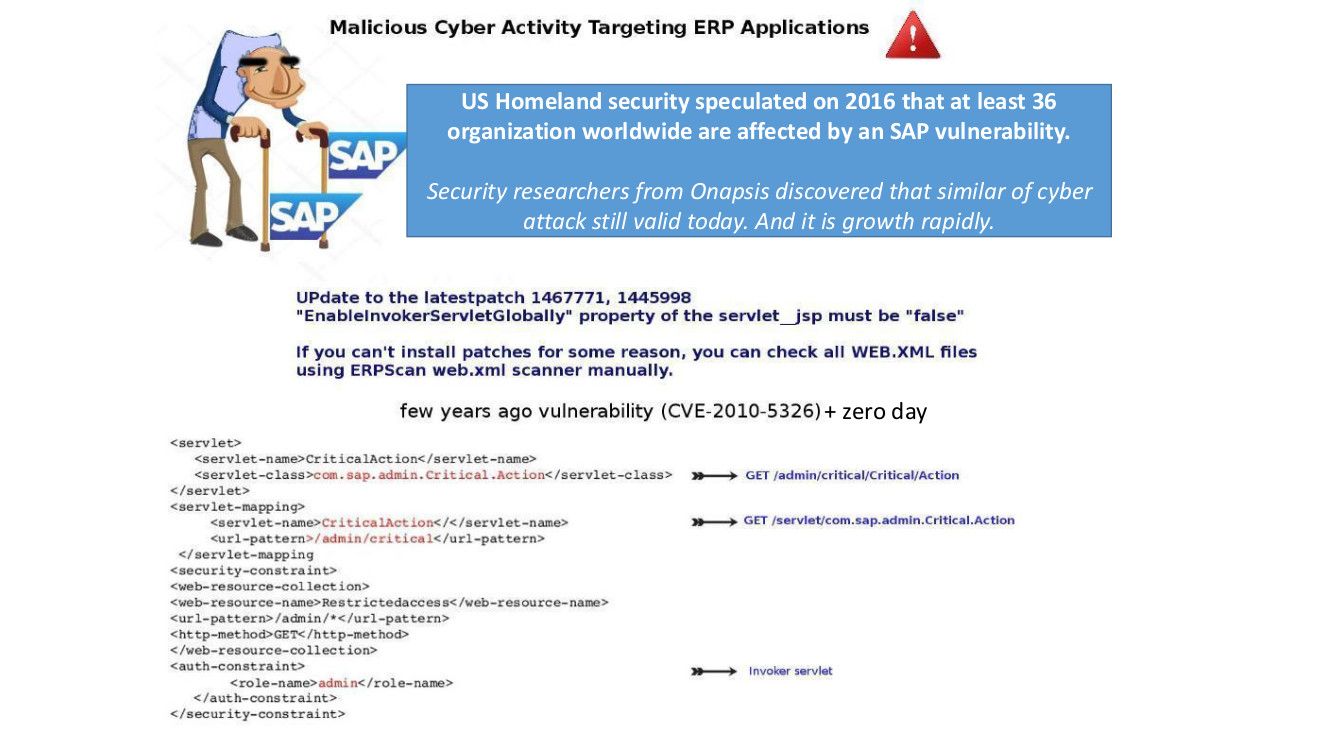
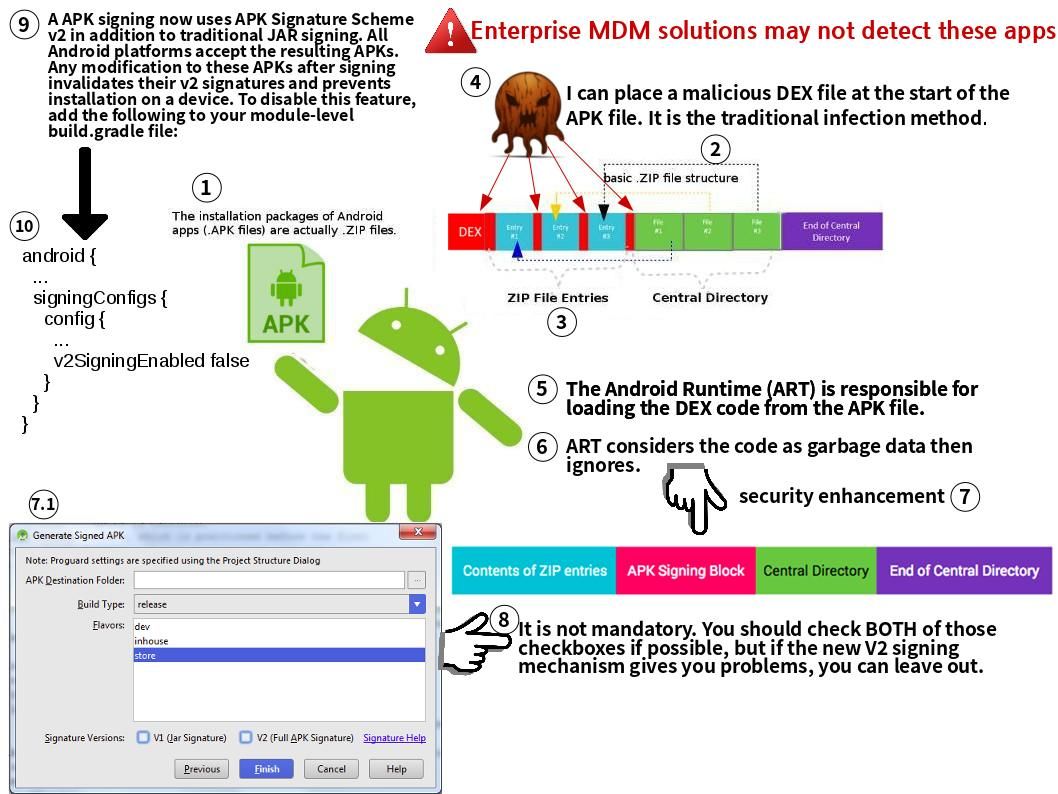
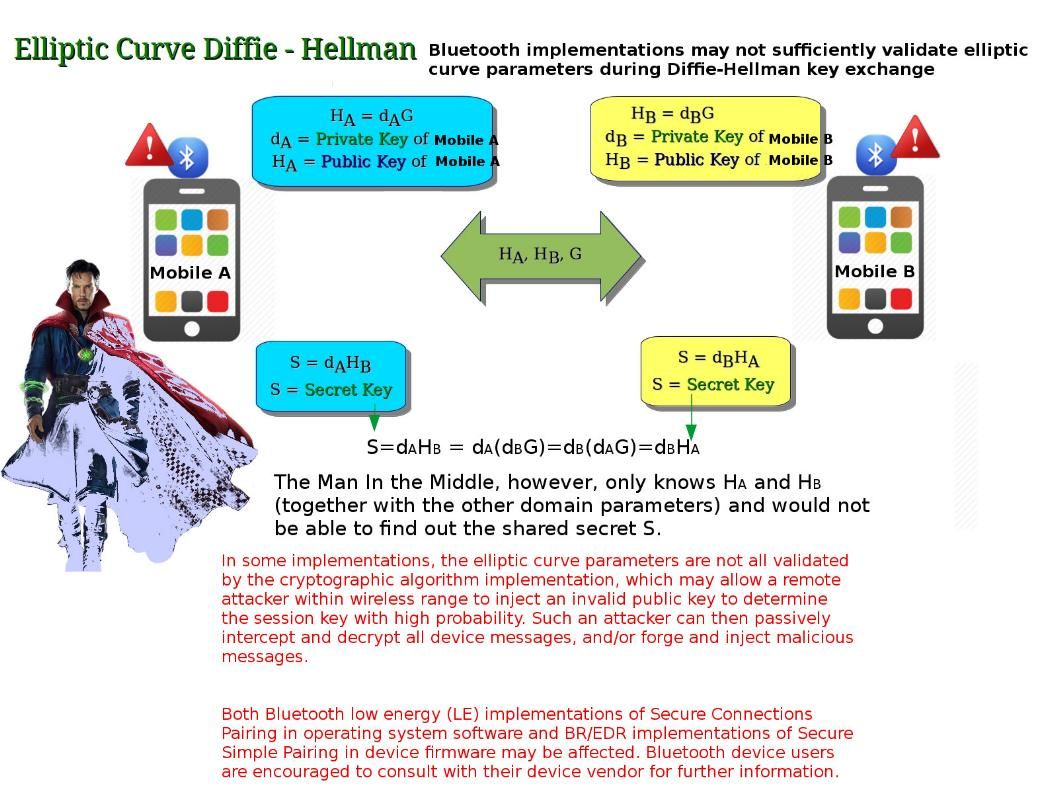
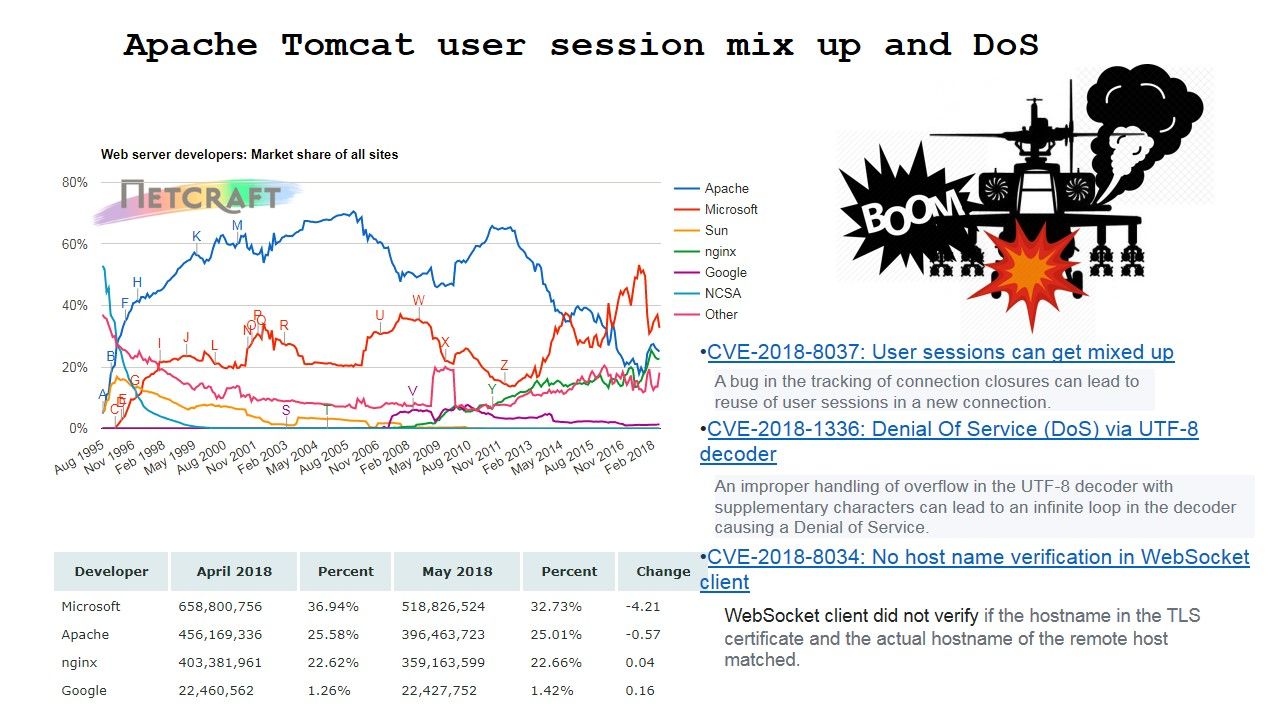
If Jenkins is sick (vulnerabilities) today? Any worries about that?
An official announment state the following: https://jenkins.io/security/advisory/2018-07-18/#SECURITY-390