Preface: The period from January 1, 2001 to December 31, 2100 is called the 21st century. Furthermore, our technologies world has demand for virtual technology concept. For example, virtual machine, virtual reality,..etc. Have you been think that you can do a virtual journey. See whether what is the gap in between reality and imagination?
Background: The first version of the Journey to the center of the Earth was published in 25th November 1864 by Jules Verne from France. Jules Gabriel Verne (Jules Gabriel Verne) is a French novelist, poet and playwright. The first industrial revolution started in the 1760s and lasted from the 1830s to the 1840s. Perhaps this revolution trigger his thinking or he has experience for close encounter of the 3rd kind?
Behind the Belief: Lizard People
According to the lizard people theory, bloodthirsty reptilian aliens first arrived on earth in ancient times. Since then, these beings have been merging with humans through the manipulation of DNA, as well as interbreeding with the human population. Conspiracy theories believing that unknown civilization including lizard people are living in the center of earth. Mixed humans (Lizard people) are not only discussed in ancient European culture. The similar of record also appearing in China. The classic Chinese book “Shan Hai Jing” 《山海經》 depicts similar types of mixed humans. However, according to general view point, the “Shan Hai Jing” 《山海經》 is a compilation of mythical geography and beasts. But I don’t think so. You can go through below details (URL and references) see whether any change to your judgement?
Reference 1: American scholar Dr. Henriette Mertz (1898-1985) studied the “Shan Hai Jing” 《山海經》. She published a book to prove that there is a description of American geography in the “Shan Hai Jing”. According to the record of Dongshan Jing《東山經》 descriptions , where the sun rises east of the sea in China. She identified the Rocky Mountains in the central and western United States,the Sierra Nevada mountains,the Cascade Mountains,the Pacific coast of the coastal mountains explicitly similar to the “Dongshan Jing” Records. For instance, four mountain structure, peaks, rivers, flora and fauna, mountain-to-Mountain distance is exactly consistent with the “Dongshan Jing” includes records the four mountain systems, peaks, rivers, flora and fauna, mountain to mountain distance.
Reference 2: During World War II, Dr Mertz worked as a code-breaker for the U.S. government’s cryptography department.
How does planet form?
Here is the simplified answer:
- Earth formed when gravity pulled swirling gas and dust in to become the third planet from the Sun.
- The formation process of planets in the solar system is likely to be irrelevant to violent collisions, explosions and the like. It may be a slow combination of ice and gravel floating in space.
Recently the scientist of NASA found that the exact way to form a planet may be by a slow combination of ice and gravel floating in space. Instead of something to do with explosion. So called “Big Bang”.
Remark: The Big Bang theory is a cosmological model of the observable universe from the earliest known periods through its subsequent large-scale evolution.
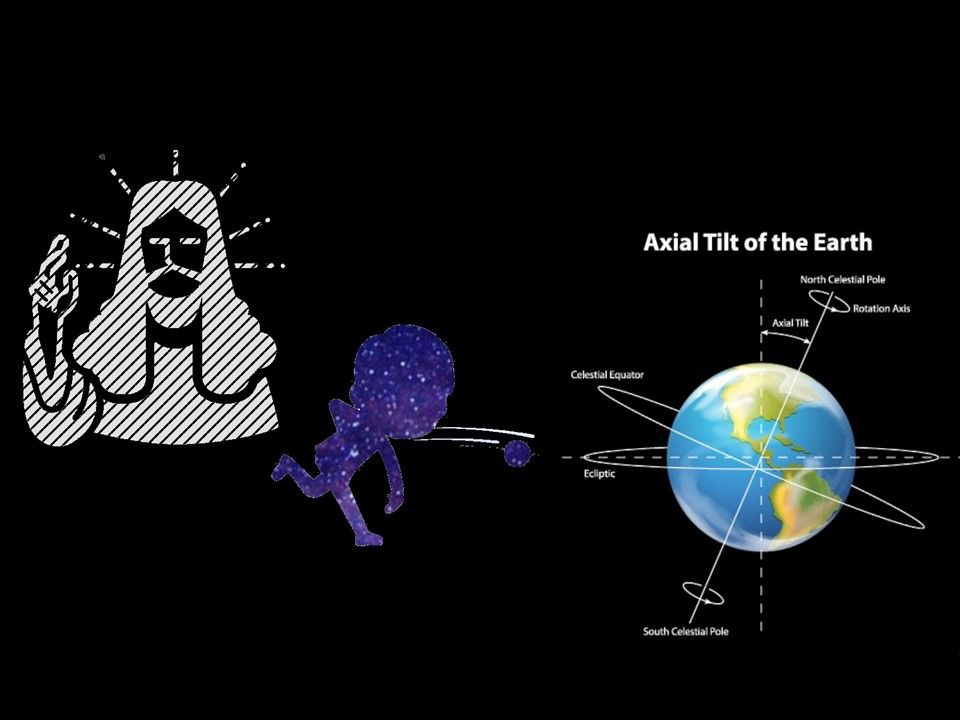
Even though how to form. Since the planet is a circle shape (ball). This shape is difficult to define a central axis. Whereby, in what way to find out the central axis? Perhaps we can use this example. Axis rotation is the difference between the direction the ball is rotating and the direction that it is moving down the lane. The axis of rotation is determined by the horizontal angle of your fingers (how far around the side of the ball your fingers are) as you release the ball. That is the tilt of planet will be depends on the throw angle when it created.
“The process of forming planets has a bunch of stages, and the last stage is what’s called the ‘giant impact’ phase,” said Professor Doug Hamilton. Infographic below for reference:
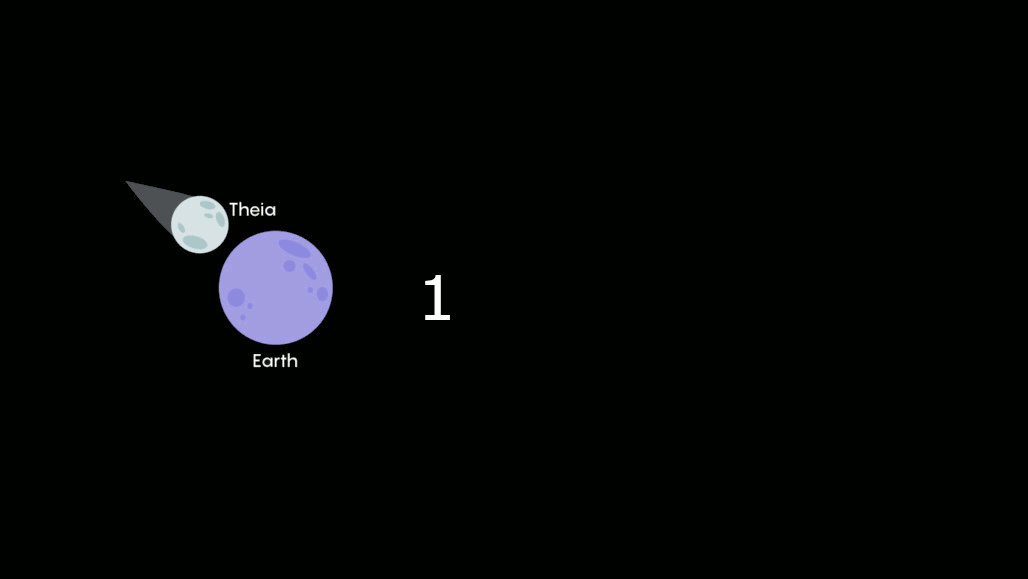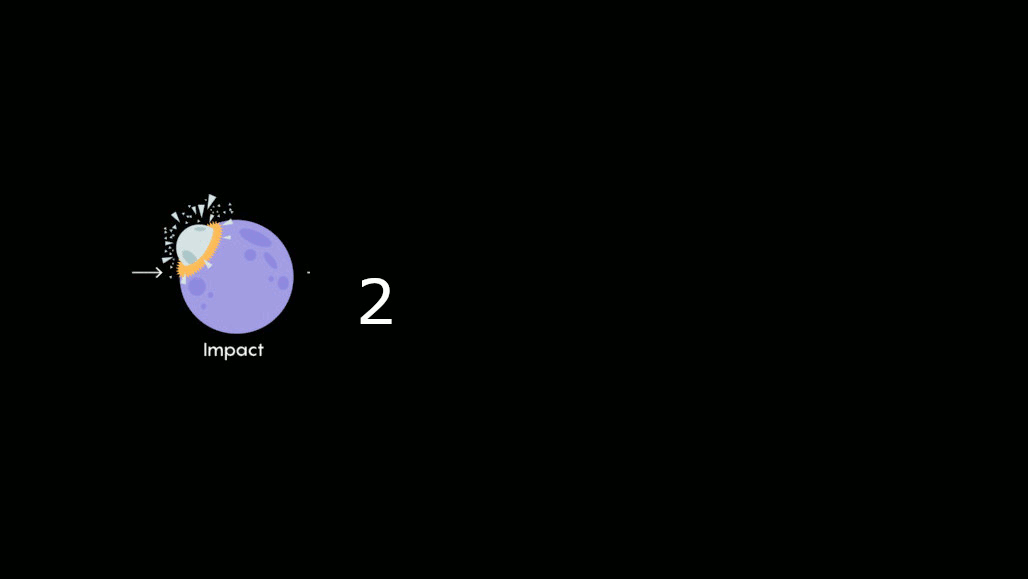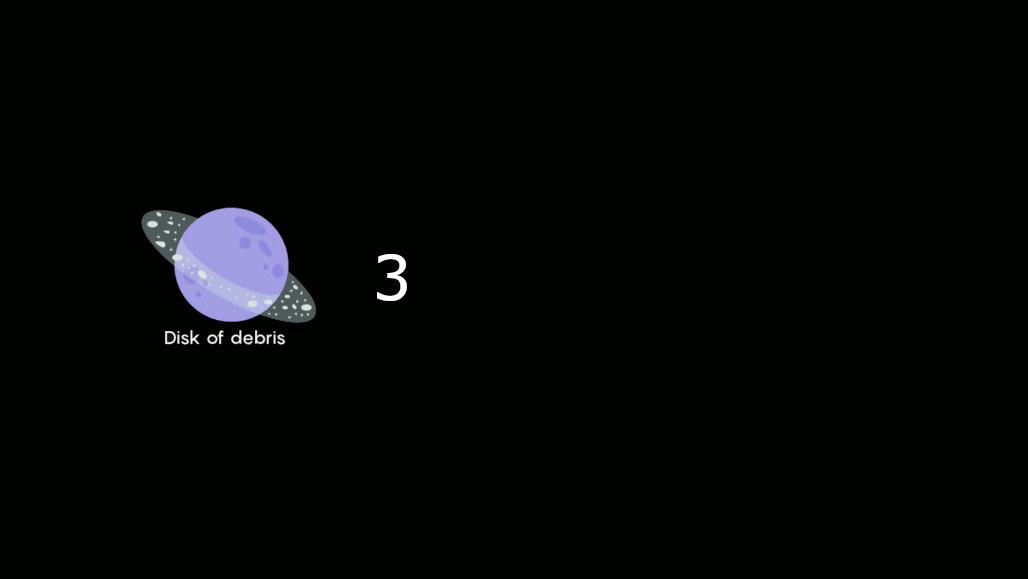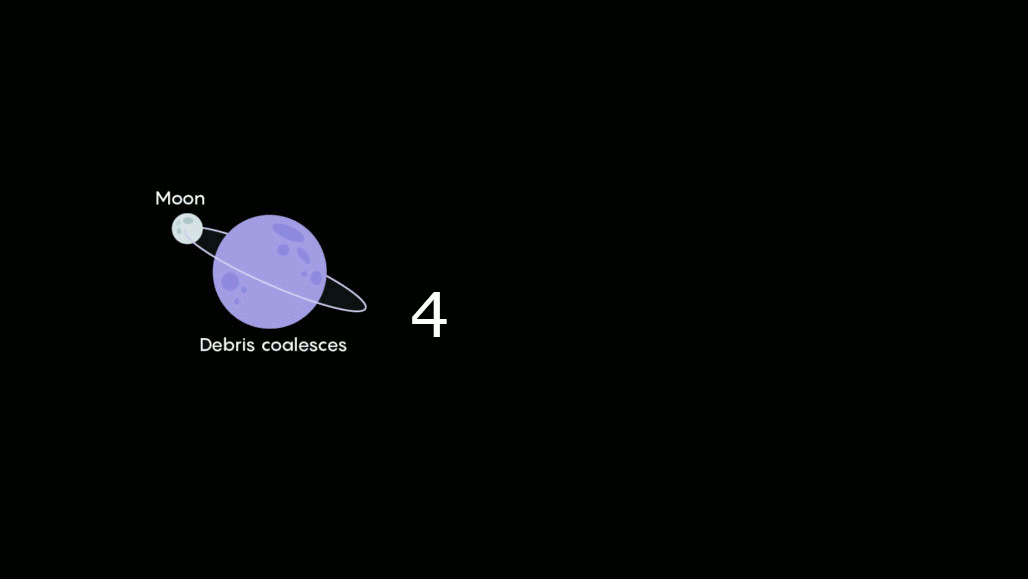
No matter in which way, there is a lot of explosion happens in universe. The powerful shock wave generated during astral explosion or else. Which cause the astral receiving this powerful energy. If a planet located in is located at Lagrange point. Even this force cannot pull the planet to other location. However it will let the astral spinning. Furthermore the universe is in vacuum state. Maintaining rotation at constant speed in a vacuum does not require any further input of energy.
As a matter of fact, you may seen there is a quite a lot of coincident happens in this astral forming. And therefore a lot of people including myself has queries that whether it is a artificial creation instead of forming by nature.
There is magma in the core of the earth, is it the driving force that causes the earth to rotate?
The solid core of the earth rotates only once every 120 years or so. No one knows the real reason for the reversal. The original energy that caused the rotation of the Earth when the earth was formed. As far as we know, at least two ways found by scientist that what is the possibilities to form our earth (see below).
Why is the core of planets hot?
There are three main sources of heat in the planet:
- Heat from when the planet formed and accreted, which has not yet been lost;
- Frictional heating, caused by denser core material sinking to the center of the planet; and
- Heat from the decay of radioactive elements.
Why is the Earth tilted at 23.4 or 23.5 degrees? The angle varies a little over time, but the gravitational pull of the moon prevents it from shifting by more than a degree or so. This tilt is what gives us seasons. The axial tilt impact seasons, weather, even human life.
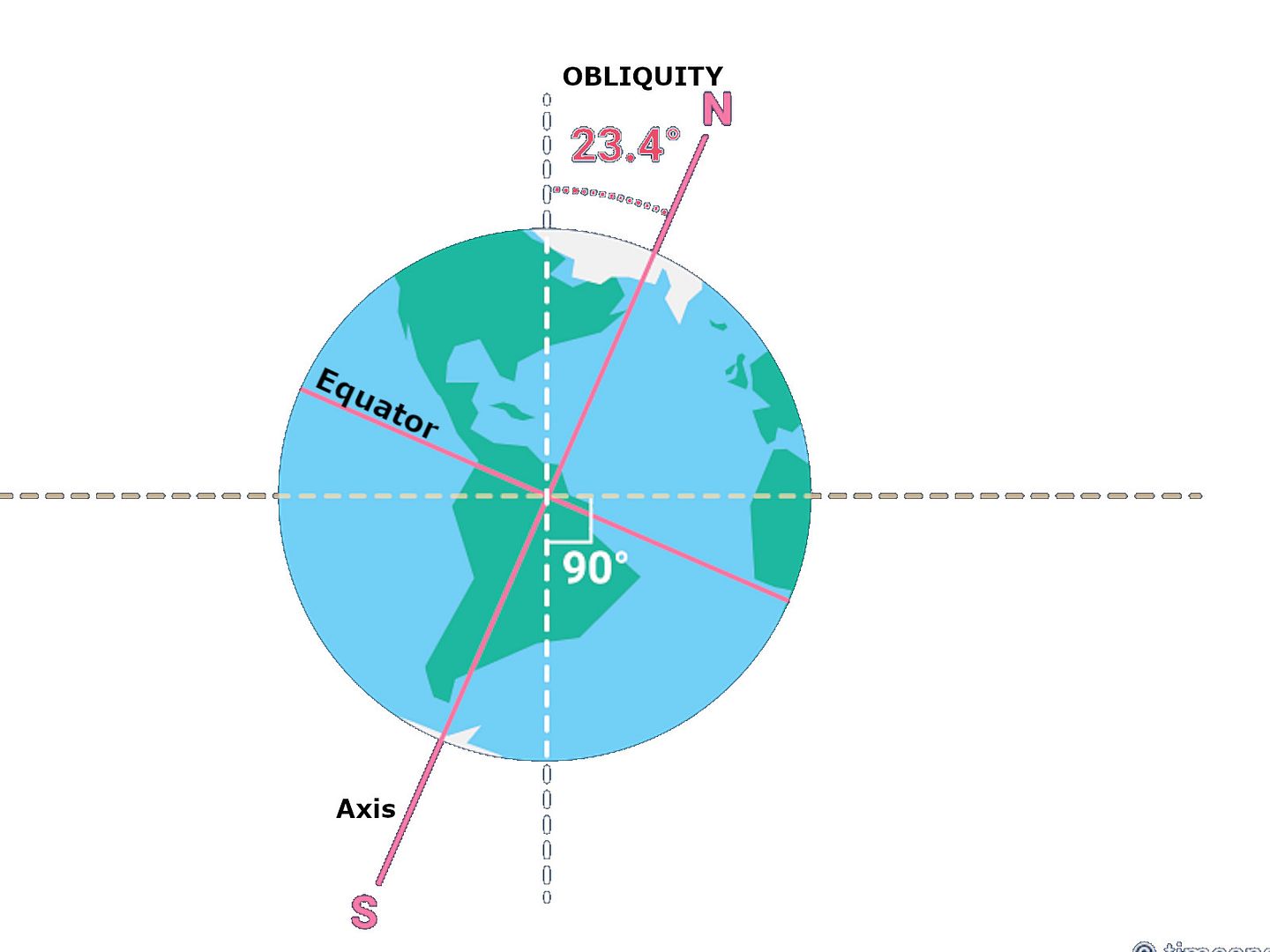
What causes the moon to rotate? The easy answer is that the moon’s orbit around Earth is tilted, by five degrees, to the plane of Earth’s orbit around the sun.

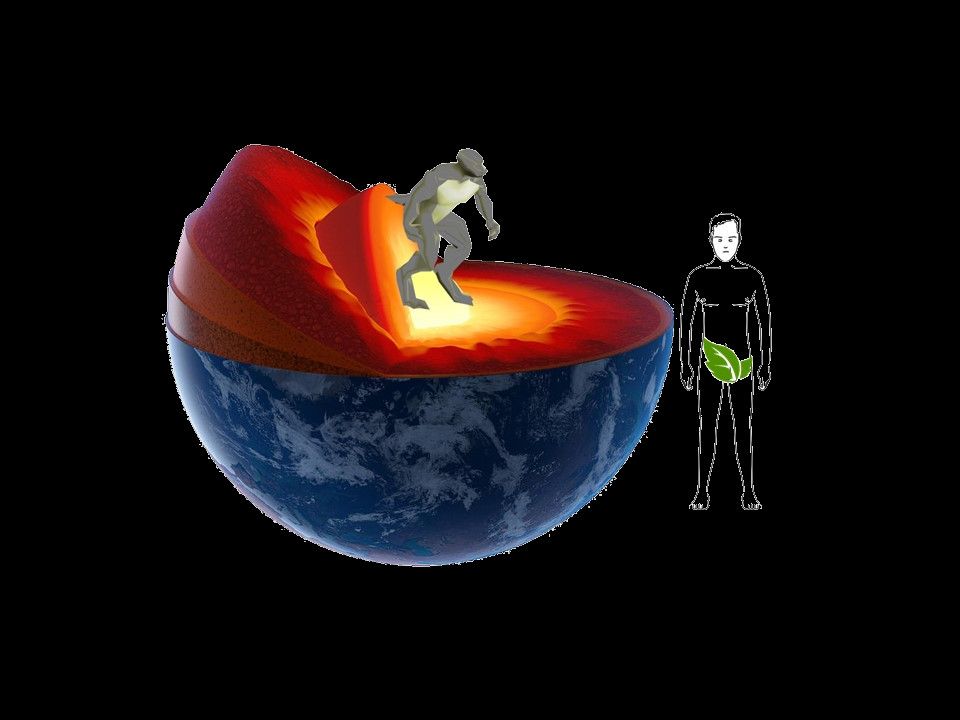
Closer look inside our earth
Gold is one of the ingredient in our earth. Pure gold is on demand item since ancient time. We can seen many things in ancient age also made by Gold. People known Gold is an expensive ingredient when mankind founded alchemy technology in ancient age. There are also unproven records of cuneiform writing in ancient Sumerian clay tablets, and advanced and unknown civilization also came to the earth to mine gold. Current scientific theories estimate that there is enough gold in the core to cover the surface of the earth with a 4 meter thick layer of pure gold. But this area cannot be mined. Therefore, the remaining gold component that can be mined is located on the earth’s crust.
According to data from the US Geological Survey (2020), underground gold reserves are currently estimated to be about 50,000 tons. Approximately 20% is still to be mined.
The density of the core is measured using several techniques including seismic geophysics. Seismic waves are measured from earthquakes all over the world.
What Is Earth’s Core Made of?

Earth’s inner core is solid iron, its outer core is liquid iron mixed with other components, and its mantle is dense rock.
Quote: We can’t put a thermometer in the Earth’s core, so the only solution is to simulate the same crushing pressure in the laboratory, said Lidunka Vočadlo (University College London, UK)
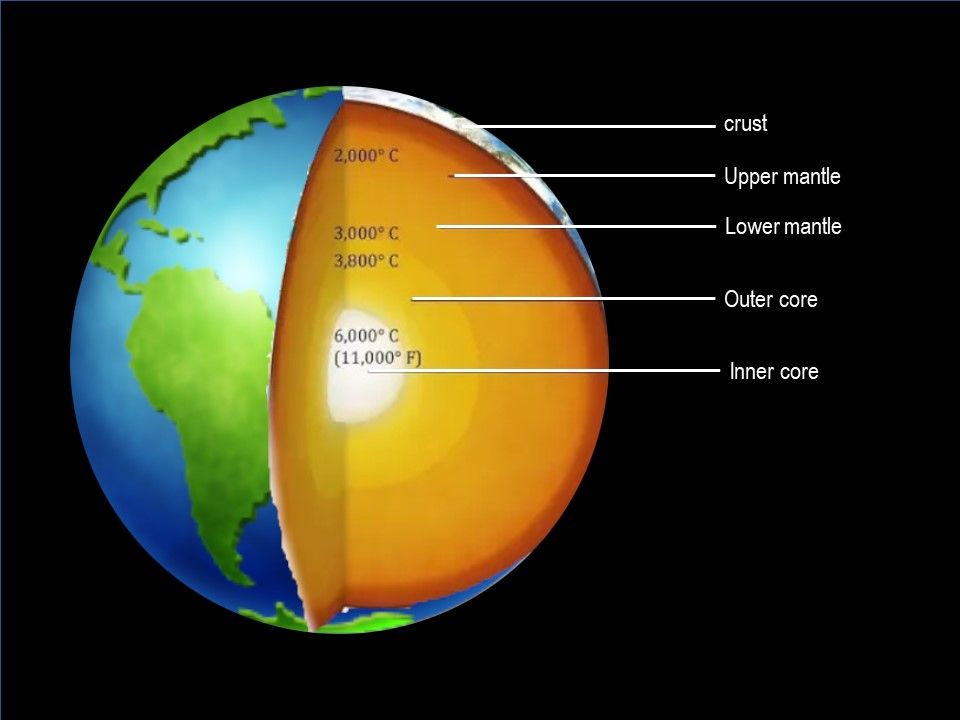
In 2013, a French research team created the best simulation conditions. They inserted pure iron into an environment where the pressure was slightly more than half the pressure of the core, which is said to be the temperature of the core. At the core temperature, the melting point of pure iron is about 6230°C. The presence of other substances causes the melting point to drop, about 6000°C, while it is still very hot, comparable to the temperature of the sun’s surface.
The Earth’s core is mainly composed of iron. It is believed that about 80% of the composition of the Earth’s core is iron, although the exact value has yet to be determined. The Iron must have been affected by gravity and settled towards the Earth’s core. Most of the rest of the Earth is made up of a rock material called”silicate”, and the molten iron must find a way to pass through these rocks to reach the core. A lot of unknown information waiting for scientist to figure out. Because we still rely on drilling methods and simulated predetermined environments.
Should the journey continue?
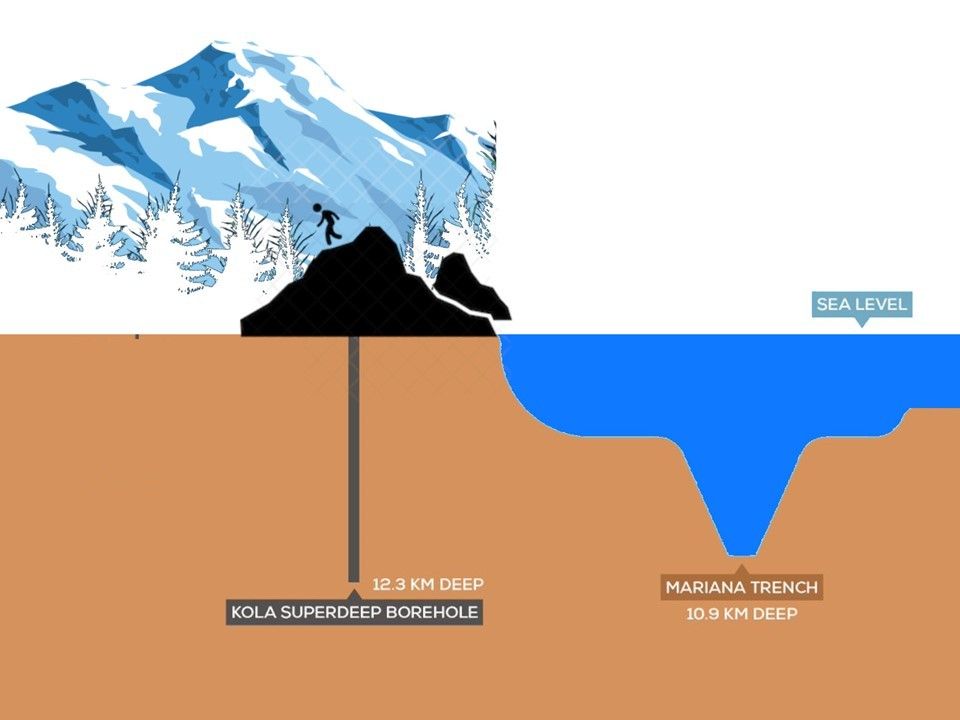
The deepest hole drilled by human being on Earth and deepest artificial point on Earth. It was created the world record by Russia Kola superdeep borehole. (40,230ft-deep (12.2km)). The drilling was stopped in 1992, when the temperature reached 180C (356F). Perhaps this is a prelude and waiting for human being to explore.
The scientific world has unlimited information waiting for human being to explore. Scientific goals allow us to understand the origin of everything in the world. I hereby to thanks for our digital world especially search engine and unlimited information on internet world. Our journey stop here.
End of this article. Thank you for your reading.
28th Jan 2021 (Moon Phase Tonight: Full Moon)
.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)