Preface: The x86-64-AMD Ryzen Zen 2 CPU is a microprocessor architecture developed by AMD. It is based on the Zen microarchitecture, which was first introduced in 2017. The Zen 2 architecture features a number of improvements over the previous generation, including higher performance, lower power consumption, and support for new features such as PCIe 4.0 and DDR5 memory. It is commonly used in desktops, laptops, and servers.
AMD is still releasing Zen2 CPUs in 2022, its AM4 shifting to the mainstream, and Zen4 occupies the high-end space.
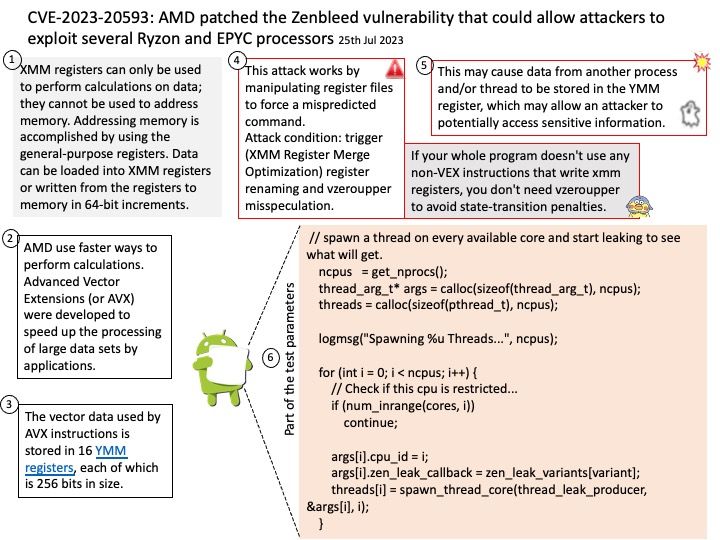
Background: Zen 2 microarchitecture – The EPYC 7742 Rome processor has a base CPU clock of 2.25 GHz and a maximum boost clock of 3.4 GHz. There are eight processor dies (CCDs) with a total of 64 cores per socket.
Vulnerability details: Under specific microarchitectural circumstances, a register in “Zen 2” CPUs may not be written to 0 correctly. This may cause data from another process and/or thread to be stored in the YMM register, which may allow an attacker to potentially access sensitive information.
Ref: AVX uses sixteen YMM registers to perform a single instruction on multiple pieces of data (see SIMD). Each YMM register can hold and do simultaneous operations (math) on: eight 32-bit single-precision floating point numbers or. four 64-bit double-precision floating point numbers.
Ref: If your whole program doesn’t use any non-VEX instructions that write xmm registers, you don’t need vzeroupper to avoid state-transition penalties.
Official announcement: For details, please refer to link – https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7008.html