Preface: Coding is the process of translating and writing codes from one language to another support operating system platform.
What is Flatpak?
If Linux user found that the new application not available in the App Stores. He can do the installation via the DEB or RPM packages. Some of them are available via PPAs (for Debian based distributions) and if nothing, one can build from the source code. Flatpak provide a 3rd way.
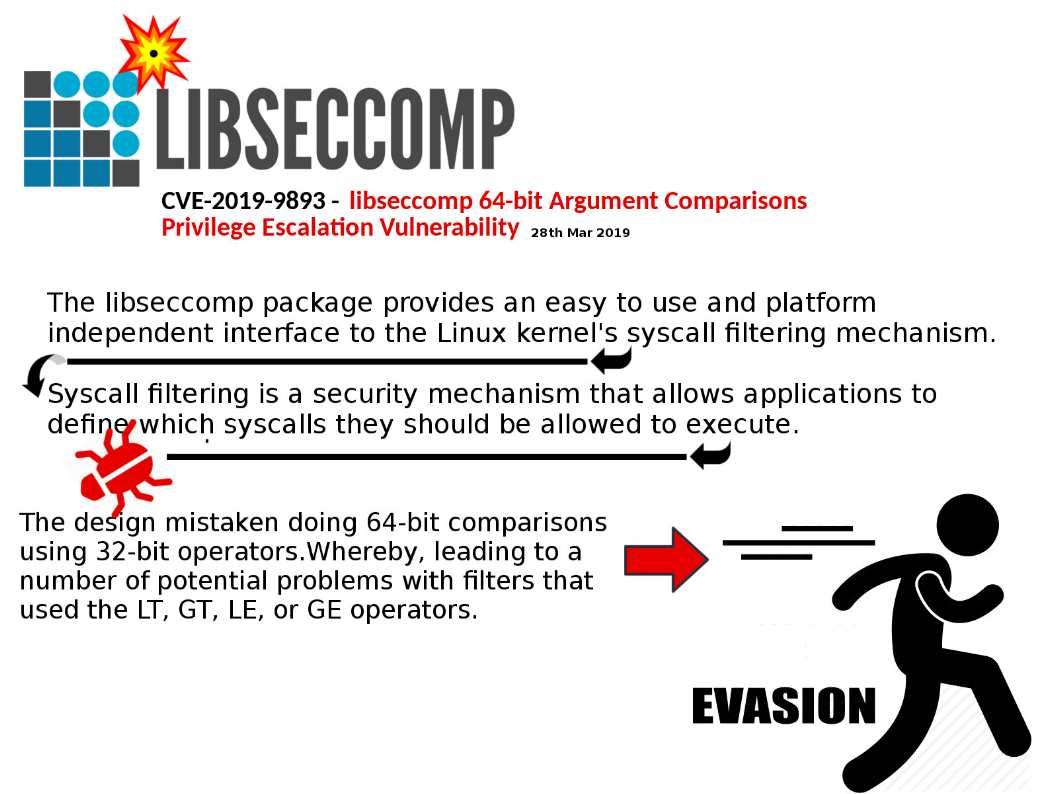
Vulnerability Details: The vulnerability exists because the affected software does not use the seccomp filter to prevent sandbox applications from using TIOCSTI IOCTL.
Reason:
The snapd default seccomp filter for strict mode snaps blocks the use of the ioctl() system call when used with TIOCSTI as the second argument to the system call. But it didn’t! The fact is that restriction could be circumvented on 64 bit architectures because it performs a 64-bit comparison,but the system call is defined with a 32-bit command argument in the kernel.
Similar design flaw discovered in libseccomp package!
Remedy: https://github.com/flatpak/flatpak/releases
Observation: Similar design flaw might found soon in other software.