Preface: The Linux framebuffer and a GPU’s memory serve different purposes in the context of graphics processing. The Linux framebuffer is a simple, low-level graphics interface that allows applications to draw graphics directly to the screen.
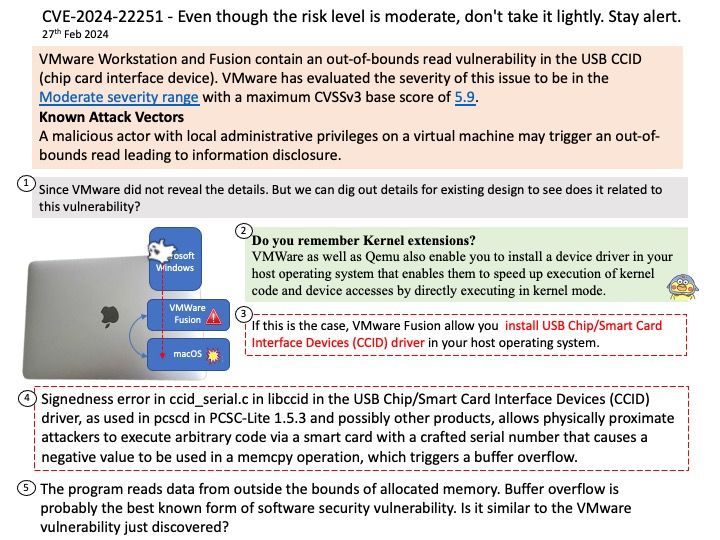
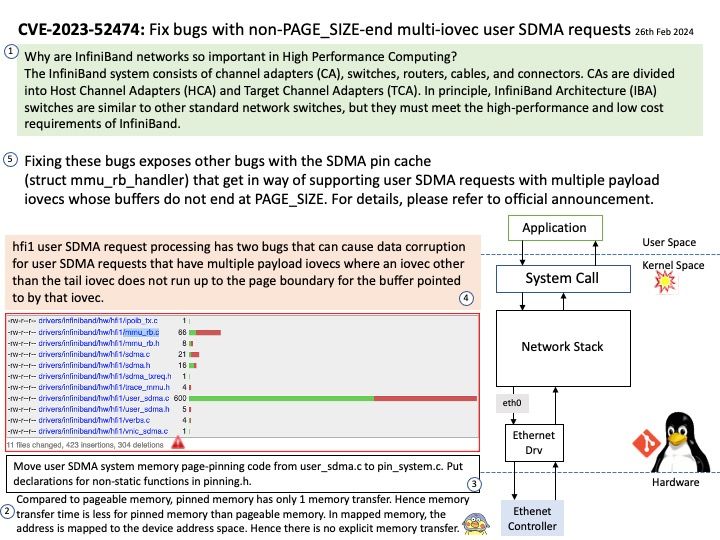
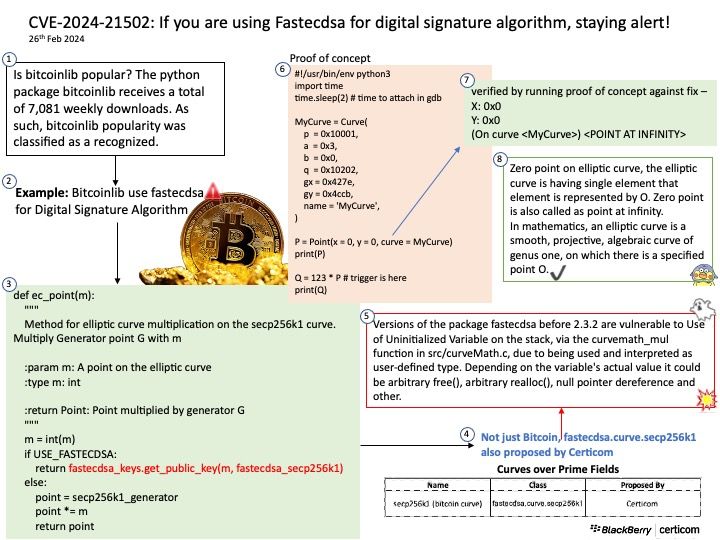
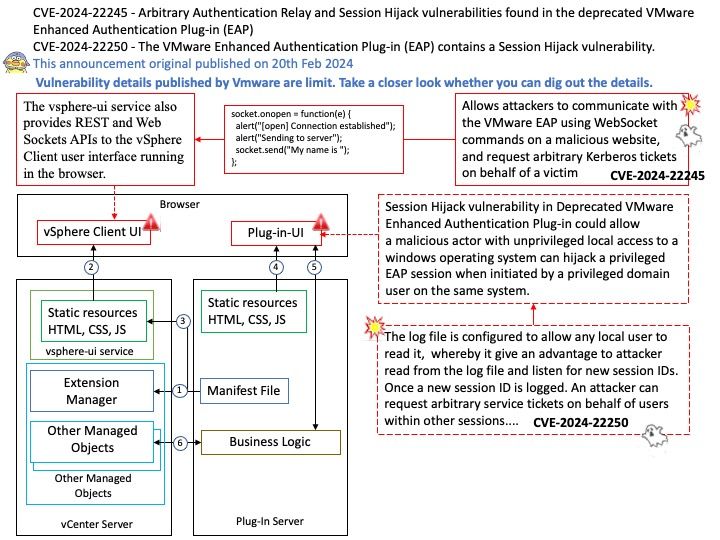
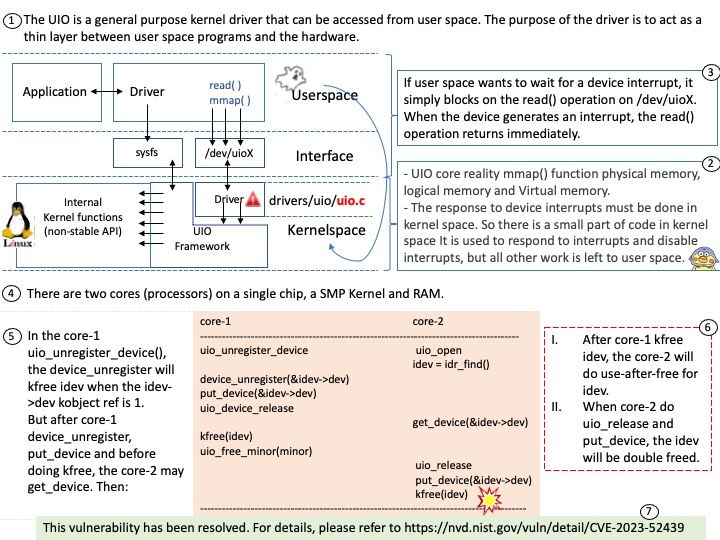
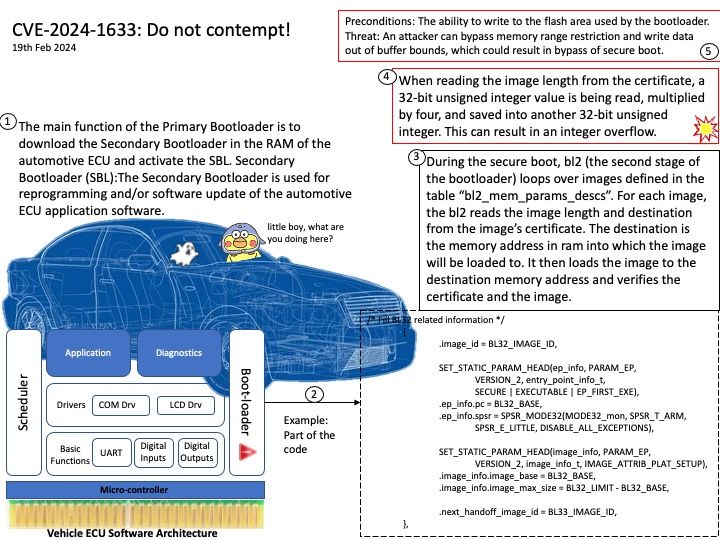
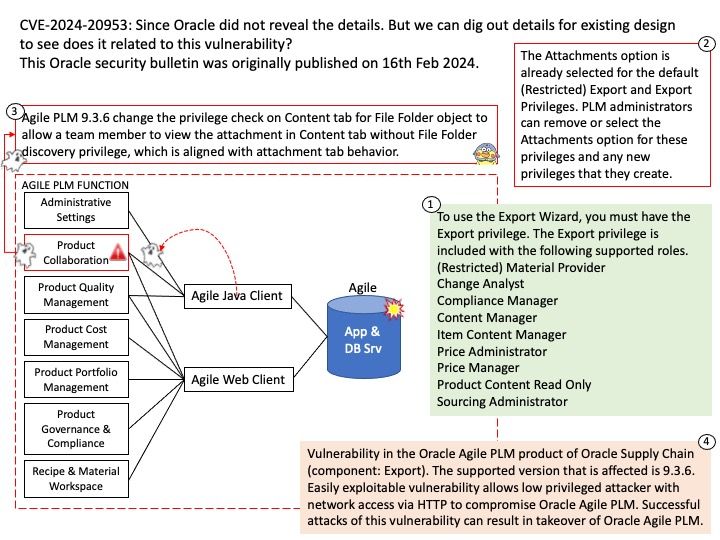
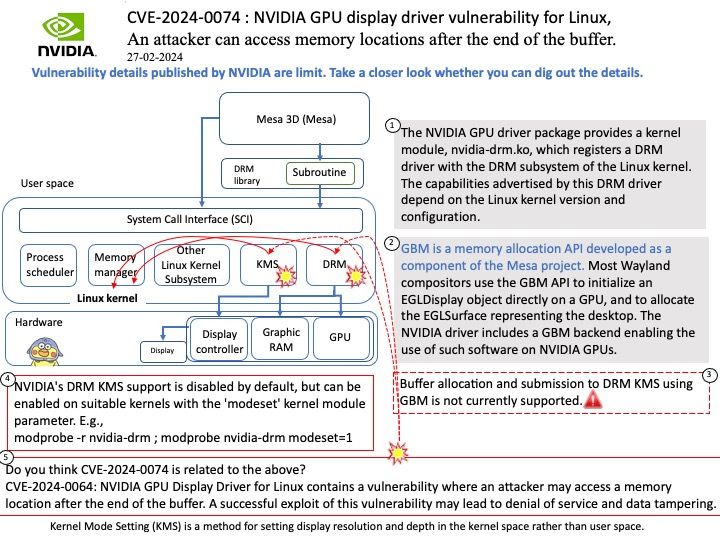
Background: The DRM/KMS framework is dedicated to the management of the display, graphic and composition subsystems. With the help of other Linux multimedia frameworks and applications, the DRM/KMS framework is typically used: to compose animated contents taking advantages of the hardware acceleration.
Remark: Kernel Mode Setting (KMS) is a method for setting display resolution and depth in the kernel space rather than user space.
Vulnerability details: NVIDIA GPU Display Driver for Linux contains a vulnerability where an attacker may access a memory location after the end of the buffer. A successful exploit of this vulnerability may lead to denial of service and data tampering.
Official announcement: Please refer to the official announcement for details – https://nvidia.custhelp.com/app/answers/detail/a_id/5520