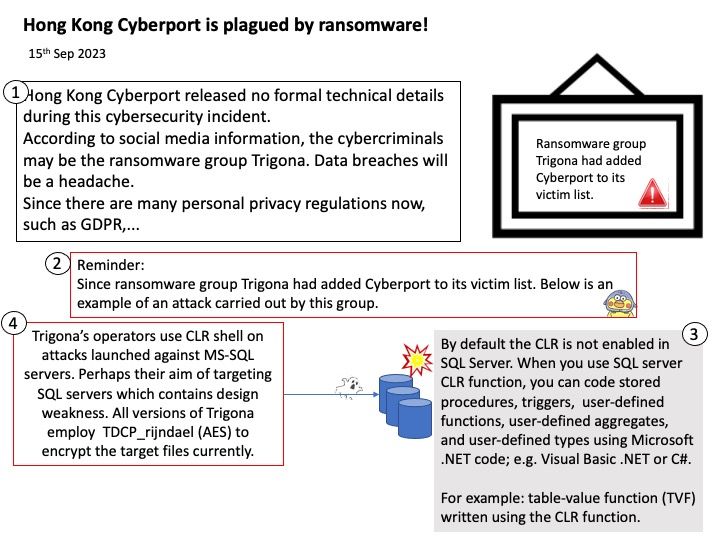
Preface: On 13th Sep 2023, There is another new development in the cyberport hacker incident, said wepro180[.]com. The 400GB of stolen data was disclosed on the dark web on Tuesday (12/9), including employee salaries, applicant resumes, credit card information and other sensitive documents. Cyberport said it has directly contacted those who may be affected.
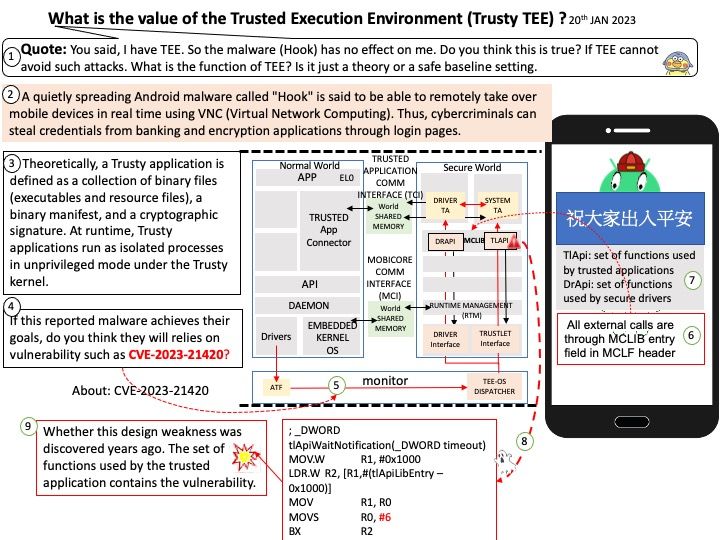
Think about it after you know it
About the Computer Functional Footprint – Business users are storing some data in SharePoint lists. Perhaps enterprise firm operation management need to do report and analytic. So, it is common to select popular solution. ETL processes extract data from different sources, transforms it, and loads it into data warehouse (MSSQL).
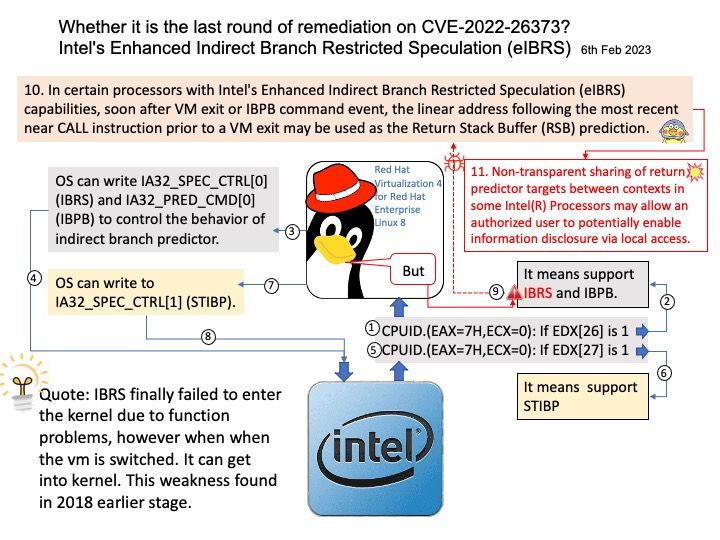
By default the CLR is not enabled in SQL Server. When you use SQL server CLR function, you can code stored procedures, triggers, user-defined functions, user-defined aggregates, and user-defined types using Microsoft .NET code; e.g. Visual Basic .NET or C#.
For example: table-value function (TVF) written using the CLR function.
The rise of the ransomware power
In April 2023, Trigona began targeting compromised MSSQL servers by stealing credentials through brute-force methods, according to observations by cybersecurity experts. But the group began operating actively on the Internet around late October 2022.
Trigona’s operators use CLR shell on attacks launched against MS-SQL servers. Perhaps their aim of targeting SQL servers which contains design weakness. All versions of Trigona employ TDCP_rijndael (AES) to encrypt the target files currently.
My comment: Any software and hardware design is to help people improve operating efficiency. In theory we all know about protection, defense and mitigation. However, when dealing with today’s demanding business world and multi-solution environments. Talk about cybersecurity should be accompanied by practical support. However, the market is highly competitive and the establishment of any new project will bring the burden of network security. Sometimes it’s a trade-off on the part of the business owner or management team.