Preface: What’s required to create good machine learning systems?
-Data preparation capabilities.
-Algorithms – basic and advanced.
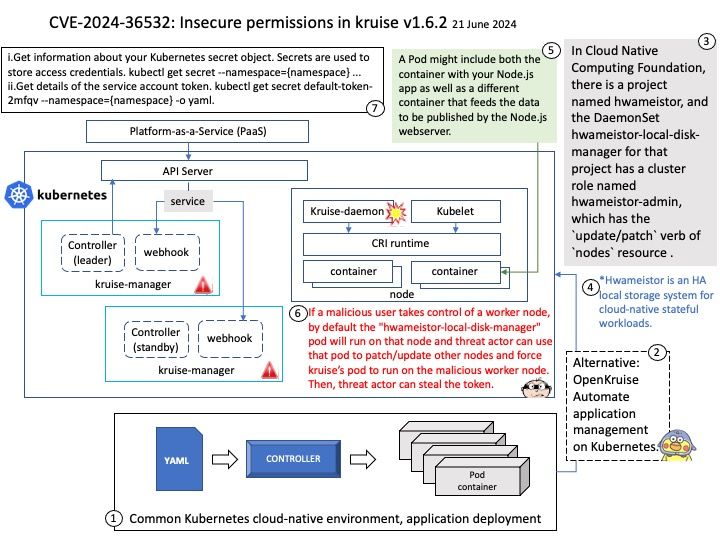
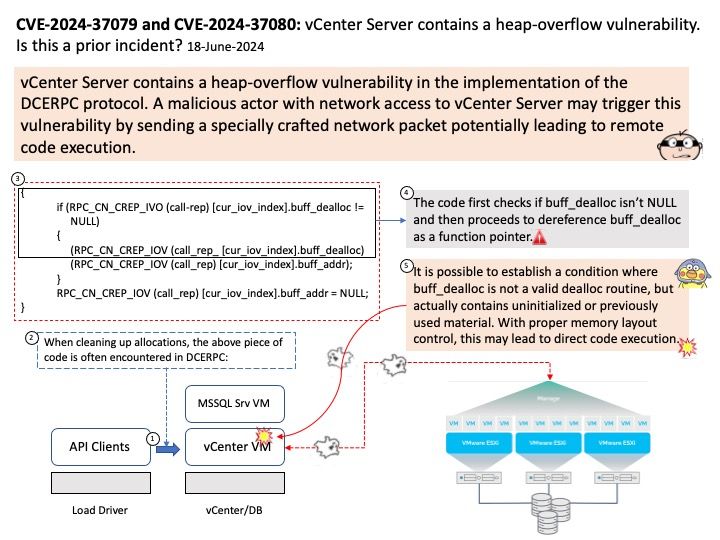
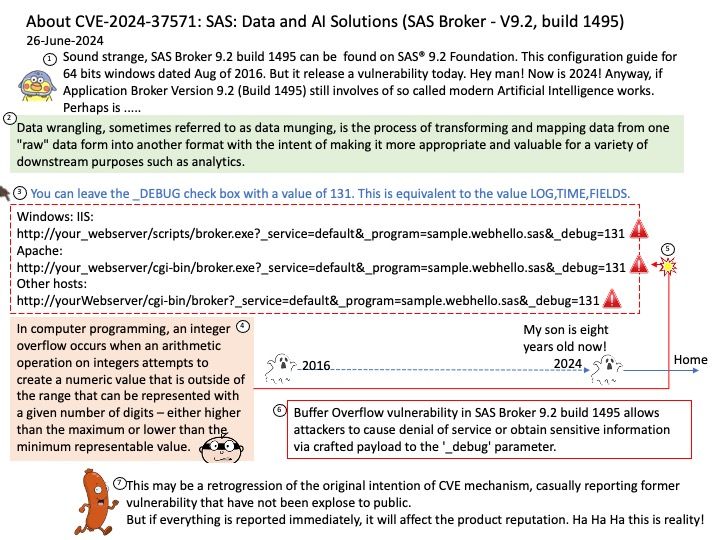
-Automation and iterative processes.
-Scalability.
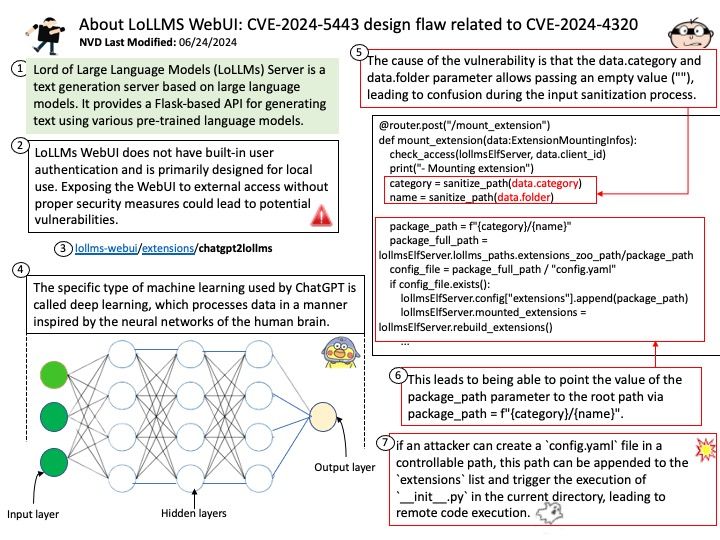
-Ensemble modeling.
Did you know?
-In machine learning, a target is called a label.
-In statistics, a target is called a dependent variable.
-A variable in statistics is called a feature in machine learning.
-A transformation in statistics is called feature creation in machine learning.
Background: SAS offers many different solutions to use machine learning to model and predict your data. Machine learning is in high demand. Whether you are a citizen data scientist who wants to work interactively or you are a hands-on data scientist who wants to code. Migration of your BI/DI environment from SAS 9.2 to SAS 9.3 and the installation of SAS Visual Analytics (SAS 9.4).
You have access to the latest analytic techniques with SAS® Visual Data Mining and Machine Learning on SAS® Viya.
What is the difference between SAS 9.4 and SAS Viya?
SAS® 9.4 and SAS® Viya® Functional Comparison – Perhaps the most significant core platform functional difference between SAS 9.4 and SAS Viya is in the way that each one handles distributed processing. SAS Viya leverages the CAS server, and SAS 9.4 uses SAS® LASR™, SAS® HighPerformance Analytics (HPA) and SAS® Grid Manager.
Vulnerability details: Buffer Overflow vulnerability in SAS Broker 9.2 build 1495 allows attackers to cause denial of service or obtain sensitive information via crafted payload to the ‘_debug’ parameter.
Official announcement: For detail, please refer to link –