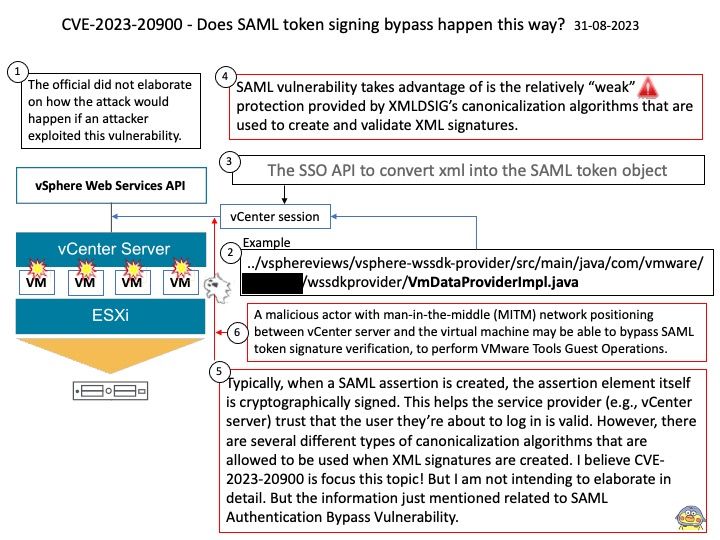
Preface: The easier way to get the SAML token is directly through the UserSession you can access in your Java plugin. UserSession has a samlTokenXml field. Then you can use the SSO API to convert that xml into the SAML token object.
Background: VMware Tools is a set of services and modules that enable several features in VMware products for better management of guests operating systems. For example:
– Pass messages from the host operating system to the guest operating system.
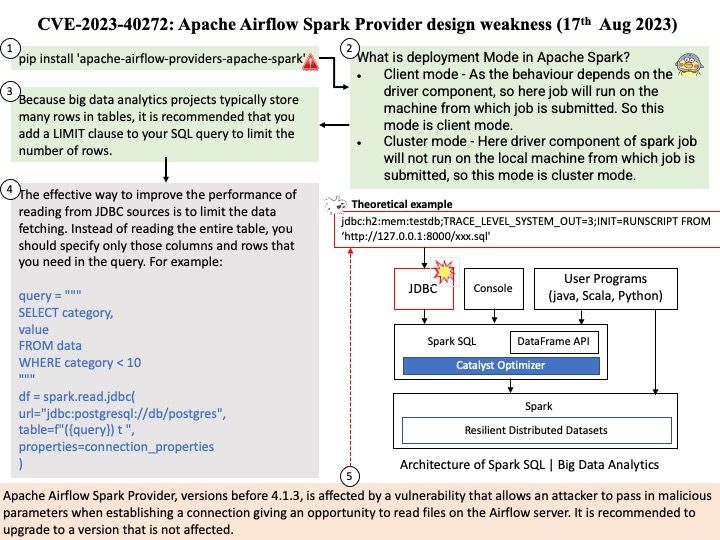
– Customize guest operating systems as a part of the vCenter Server and other VMware products.
– Run scripts that help automate guest operating system operations. The scripts run when the power state of the virtual machine changes.
– Synchronize the time in the guest operating system with the time on the host operating system
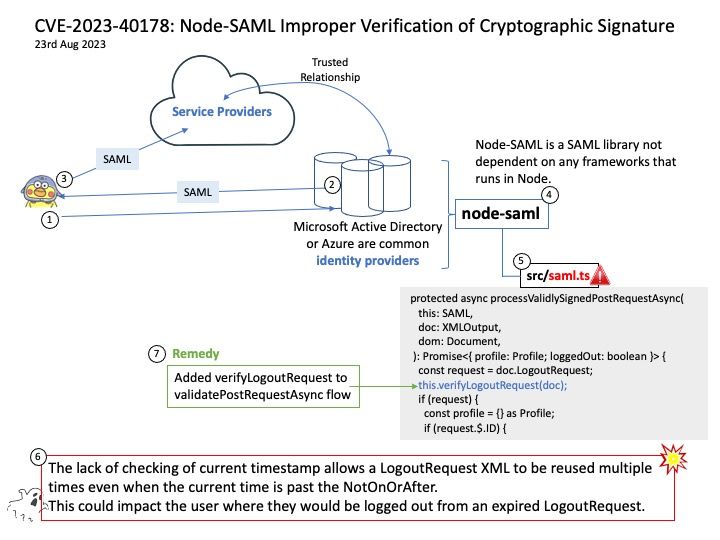
Vulnerability details: CVE-2023-20900 VMware Tools contains a SAML token signature bypass vulnerability. A malicious actor with man-in-the-middle (MITM) network positioning between vCenter server and the virtual machine may be able to bypass SAML token signature verification, to perform VMware Tools Guest Operations.
Official announcement: For details, please refer to the link – https://www.vmware.com/security/advisories/VMSA-2023-0019.html