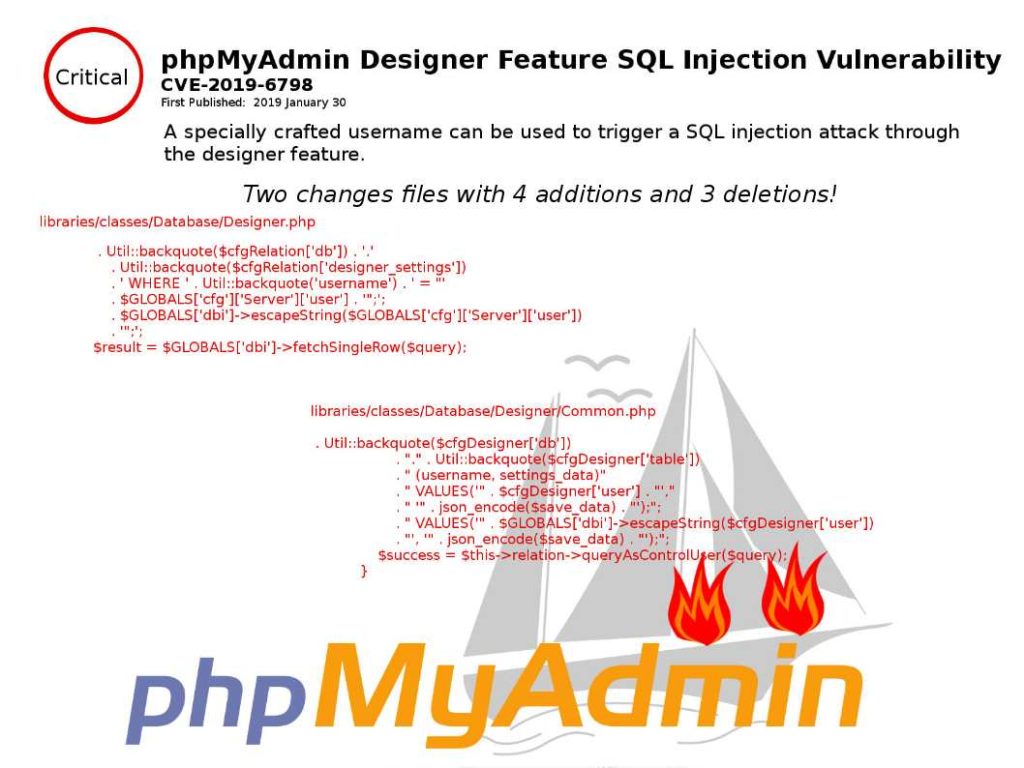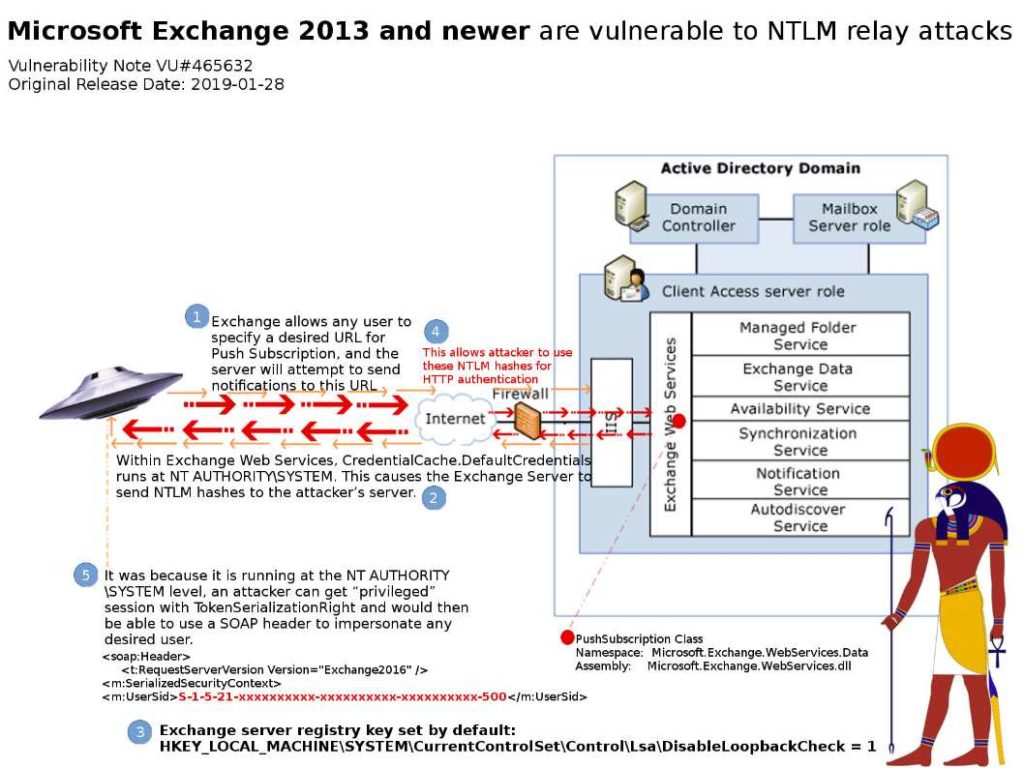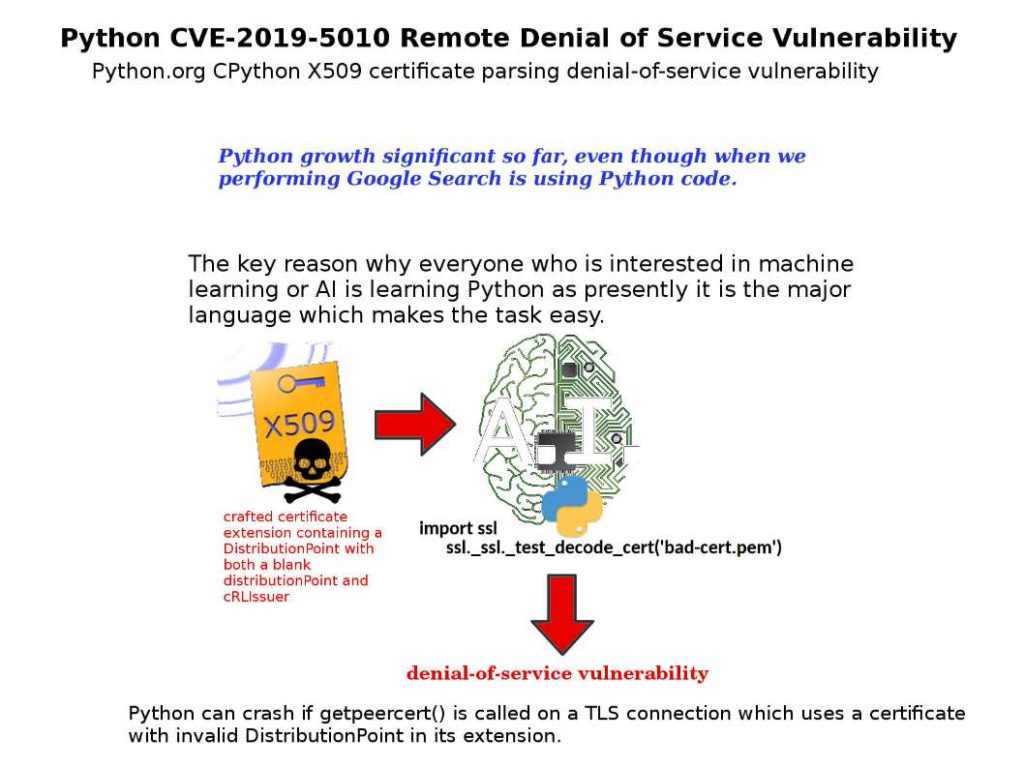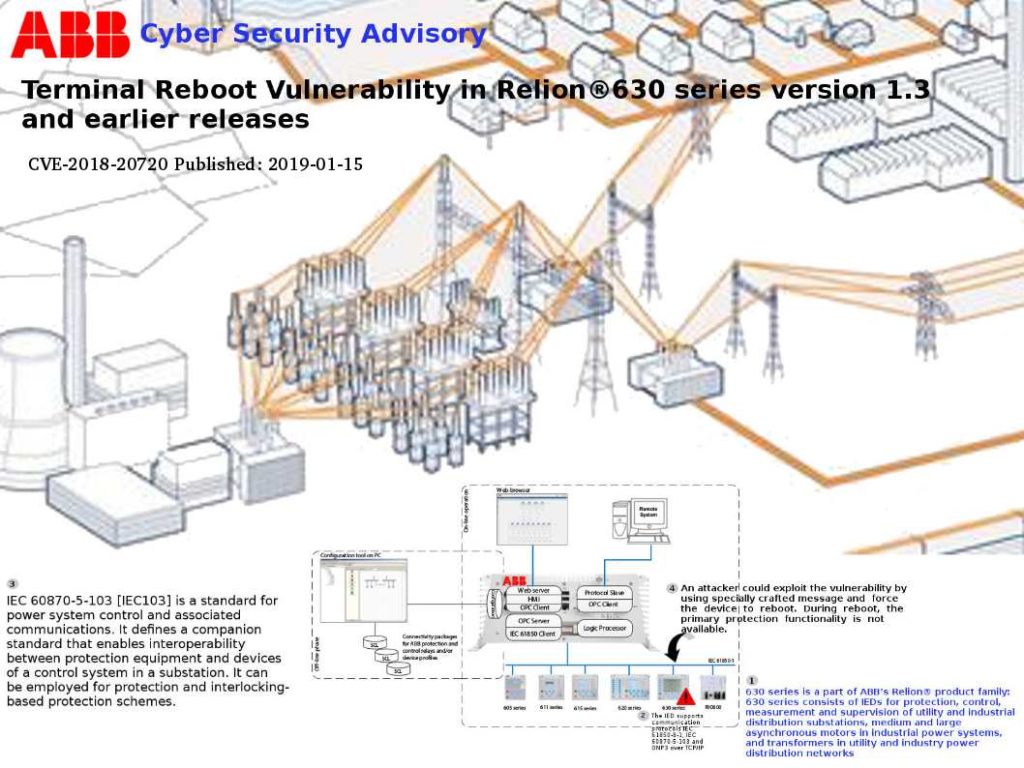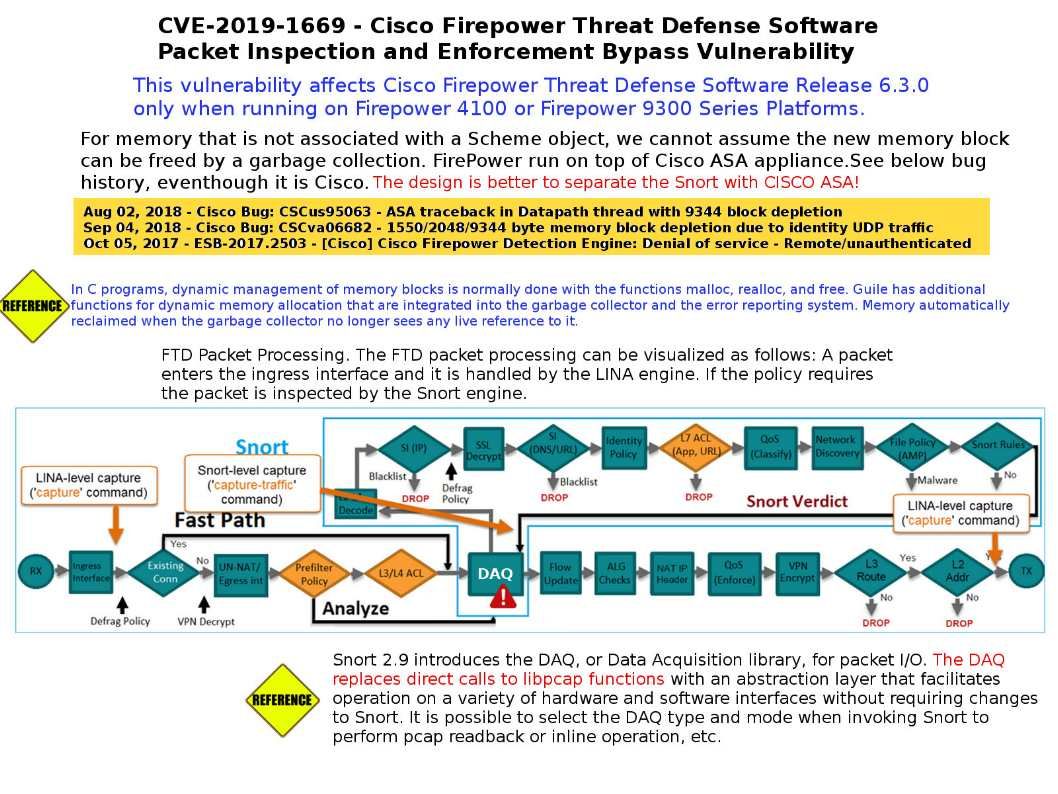
Preface: Dynamic memory automatically reclaimed when the garbage collector no longer sees any live reference to it.
Description: A vulnerability in the data acquisition (DAQ) component of Cisco Firepower Threat Defense (FTD) Software could allow an unauthenticated, remote attacker to bypass configured access control policies or cause a denial of service (DoS) condition.
Official announcement – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190123-firepowertds-bypass
My opinion: For memory that is not associated with a Scheme object, we cannot assume the new memory block can be freed by a garbage collection. FirePower run on top of Cisco ASA appliance.See below bug history, eventhough it is Cisco. The design is better to separate the Snort with CISCO ASA!