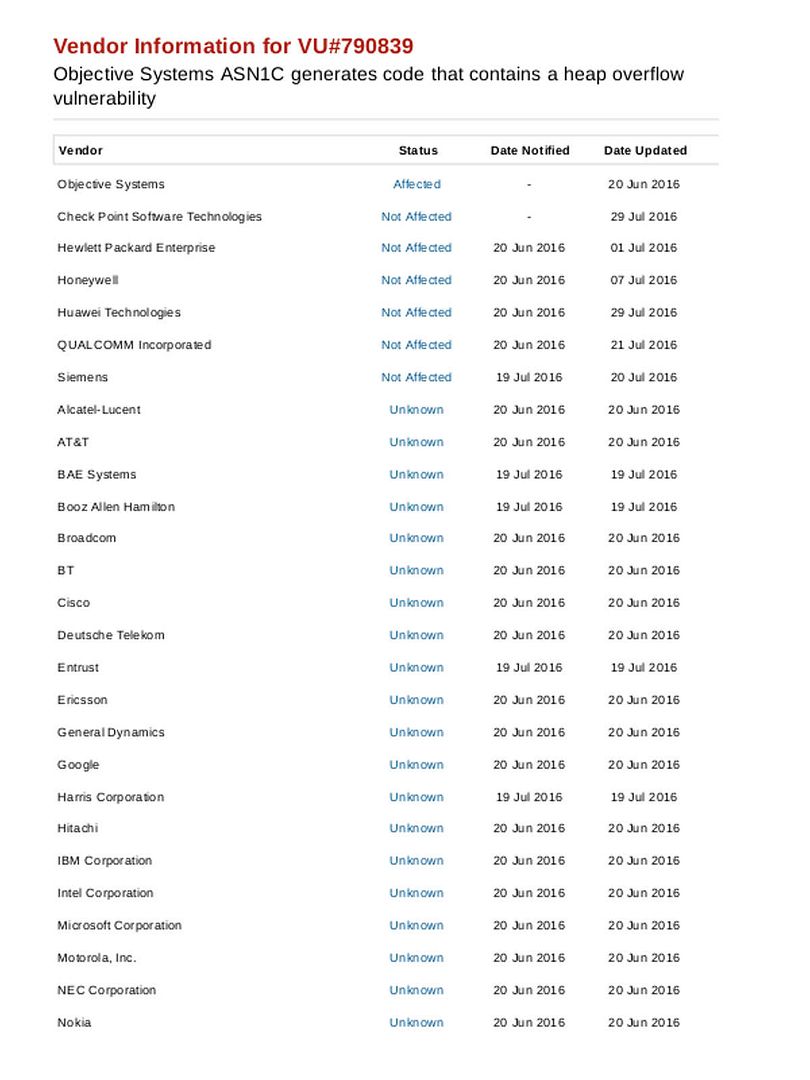
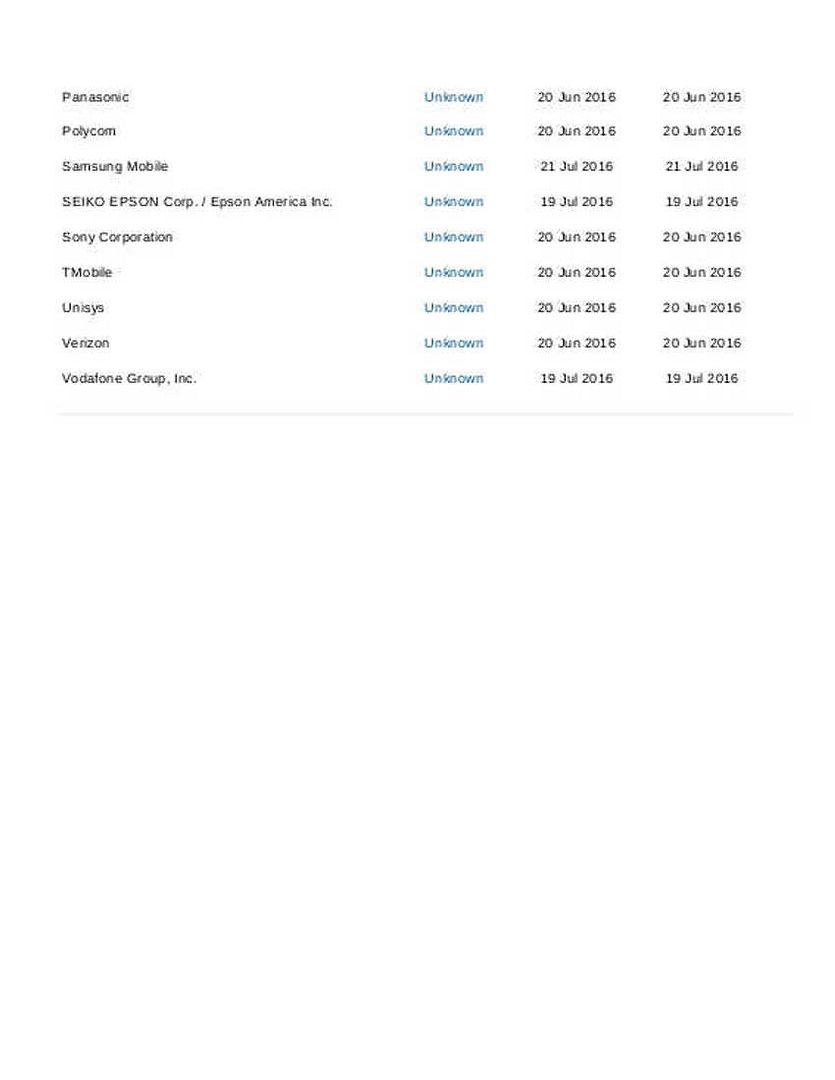
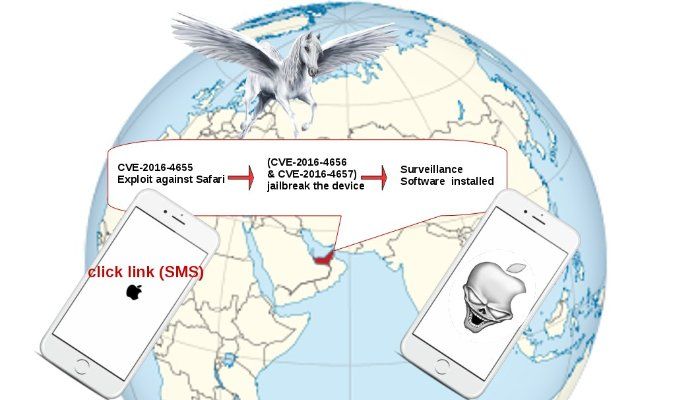
http://img.photobucket.com/albums/v704/chanpicco/chanpicco071/sat-China_zpsfc8frkuz.jpg
The important thing is to never stop questioning, said Dr. Einstein. View the breaking news today.China has launched the world’s first quantum communications satellite into orbit. Watch TV News program noticed that a group of scientist find a way apply the quantum physics to traditional cryptography replacing RSA cryptosystem. The testing go to final stage in 2015. Competitions everywhere today including employees, business partners, countries. Life is not easy! World looks demanding now! Let’s review in short form in regards to RSA cryptosystem weakness.
RSA cryptosystem weakness:
- The RSA cryptosystem can be very weak if you do not choose your primes carefully.
- If the two corresponding ciphertexts are intercepted.
- If you send the same message to more people with the same RSA encryption exponent e , then the plaintext can always be obtained easily from the intercepted ciphertexts.
Quantum Cryptography benefits:
- Quantum entanglement – particles can share the same quantum state irrespective of their spatial distance from each other. The entanglement state discard when parameters change.
- Quantum cryptography would be used in practice to produce one time pads that could be used to securely encrypt any message.
What is the key factors (built a quantum communications satellite):
Avoid eavesdropping – Being monitored
Cyber attack – Being attacked by hackers
Questioning about unknown factors?
In what Layer of the Earth’s Atmosphere install this satellite?
Answer: Exosphere – up to 10,000 km above the Earth
http://img.photobucket.com/albums/v704/chanpicco/chanpicco070/orbit-v4_zpsgkk97mbq.gif
Is there any external interfere to this layer? For instance, SUNSPOT & X-rays?
It was protected by atmosphere. Atoms are no longer gravitationally bound to the Earth and get knocked away by solar wind. As such, without interference caused by Sunspot suspend the network communications. (Remark: Satellite interfere by sunspot periodically. The result is that the satellite will lost electronic communications in short period of time.)
Does it compatible with mobile phone?
Yes, it is compatible with 4G mobile network and provides hack proof communication channel. I believed that it achieves independence from the use of fixed line or existing mobile networks through super fast Ka-band satellite backhaul.
The objective is that avoid eavesdropping on mobile phone. For instance, NSA tapped Angela Merkel’s mobile phone. The scandal expose to public in 2014.
Germany opens inquiry into claims NSA tapped Angela Merkel’s phone
https://www.theguardian.com/world/2014/jun/04/germany-inquiry-nsa-tapping-angela-merkel-phone
Interim summary:
The space of technology development is to infinite. But like Dr Einstein said, the important thing is to never stop questioning.
http://img.photobucket.com/albums/v704/chanpicco/chanpicco070/questioning_zpsyrbxvutm.jpg