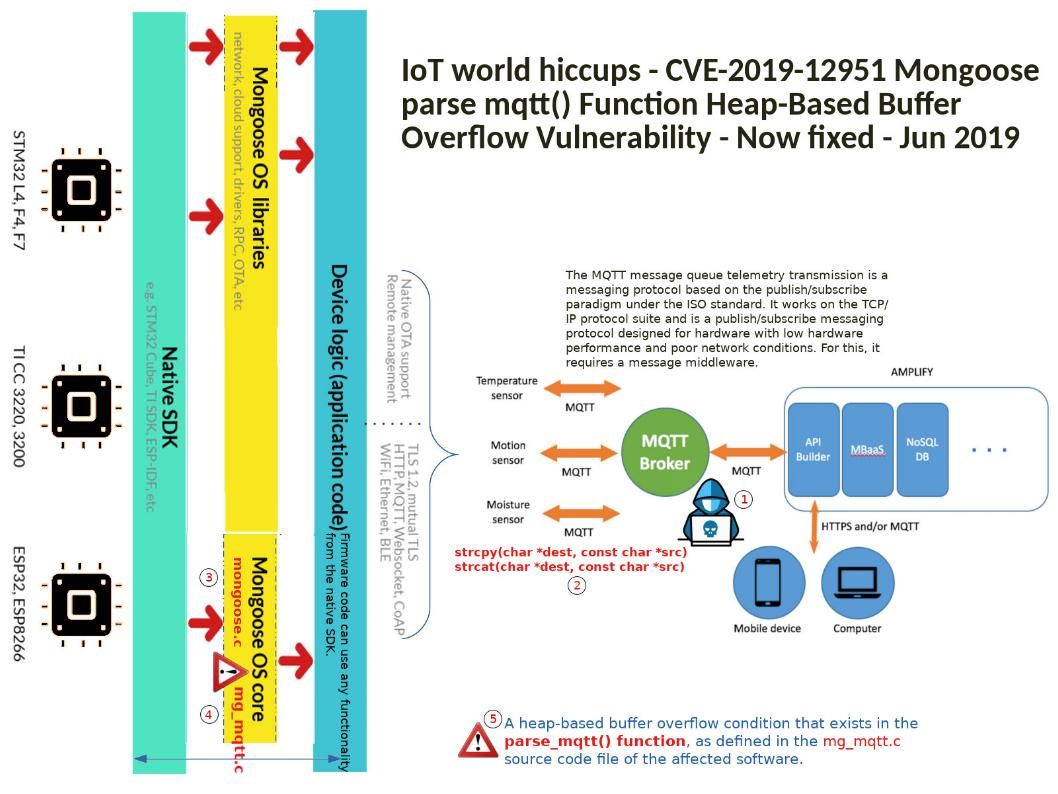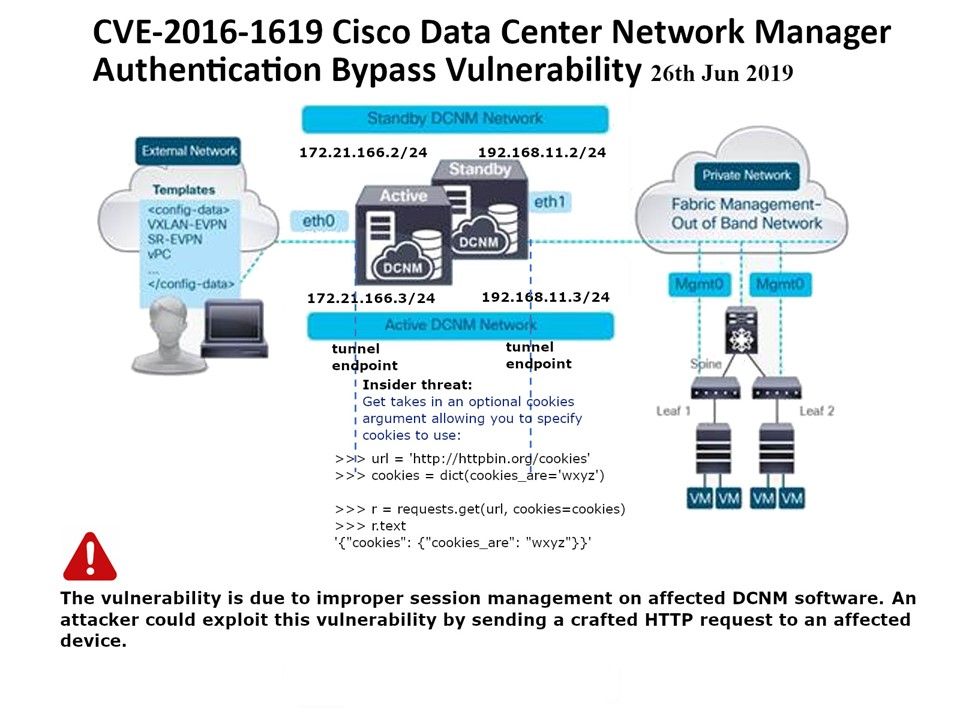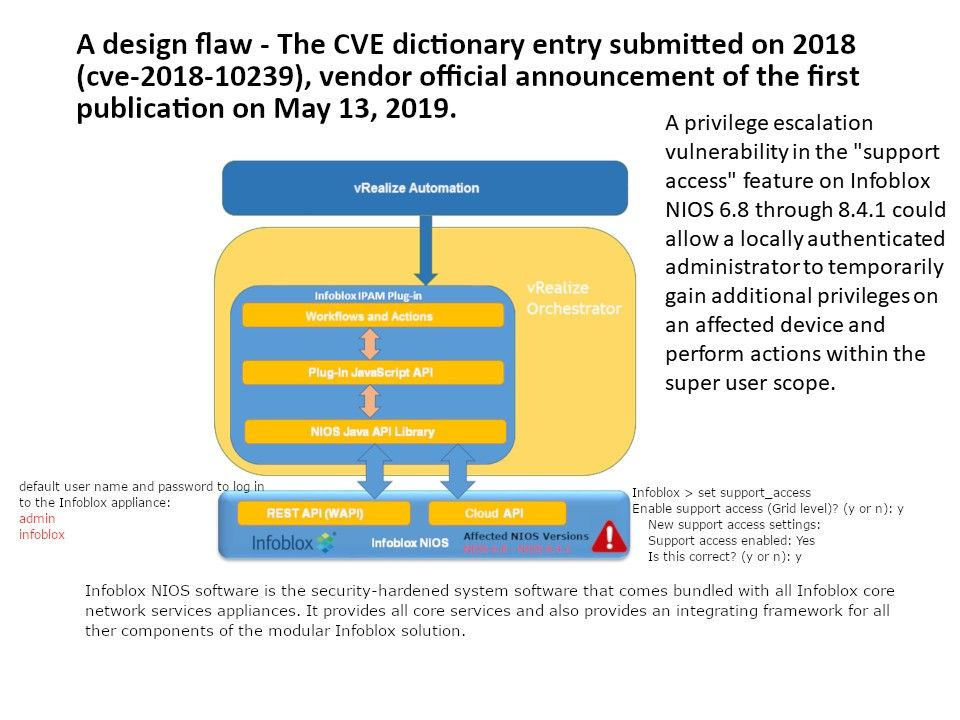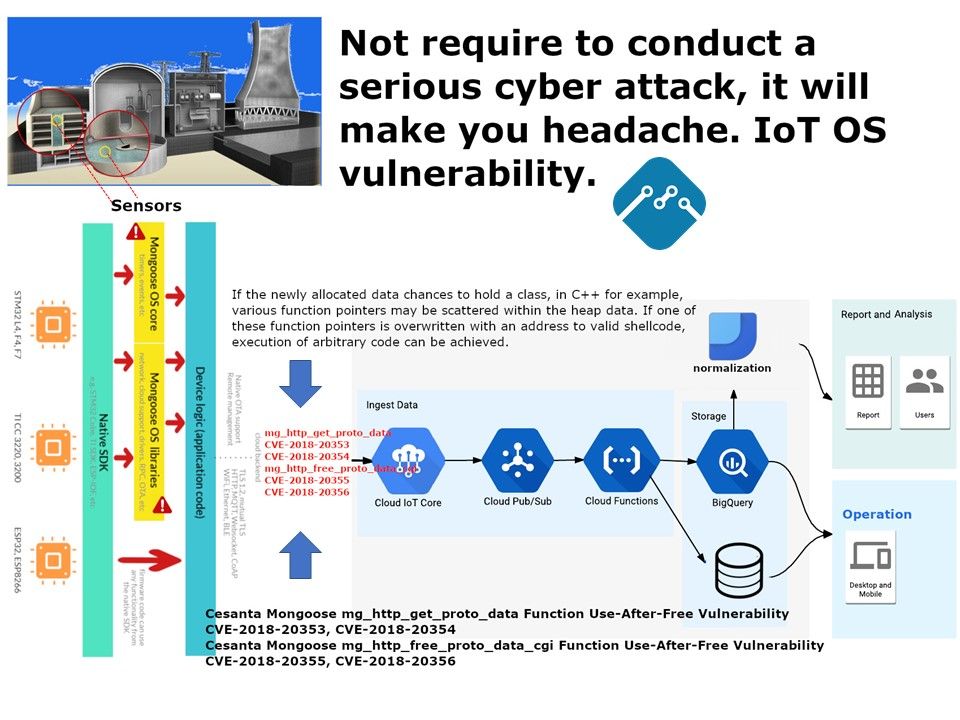
Preface: The NCSC is investigating current Ryuk ransomware campaigns targeting organisations globally, including in the UK. In some cases, Emotet and Trickbot infections have also been identified on networks targeted by Ryuk.
Technical details: Ryuk was first seen in August 2018. The Ryuk ransomware is often not observed until a period of time after the initial infection – ranging from days to months.Ryuk ransomware linked to Emotet and Trickbot banking trojans.
– The objective of Emotet conduct as a dropper feature in order to delivery for other Trojans.
– Trickbot aim to browser as a attack target, the aim to do manipulation techniques to facilitate data theft.
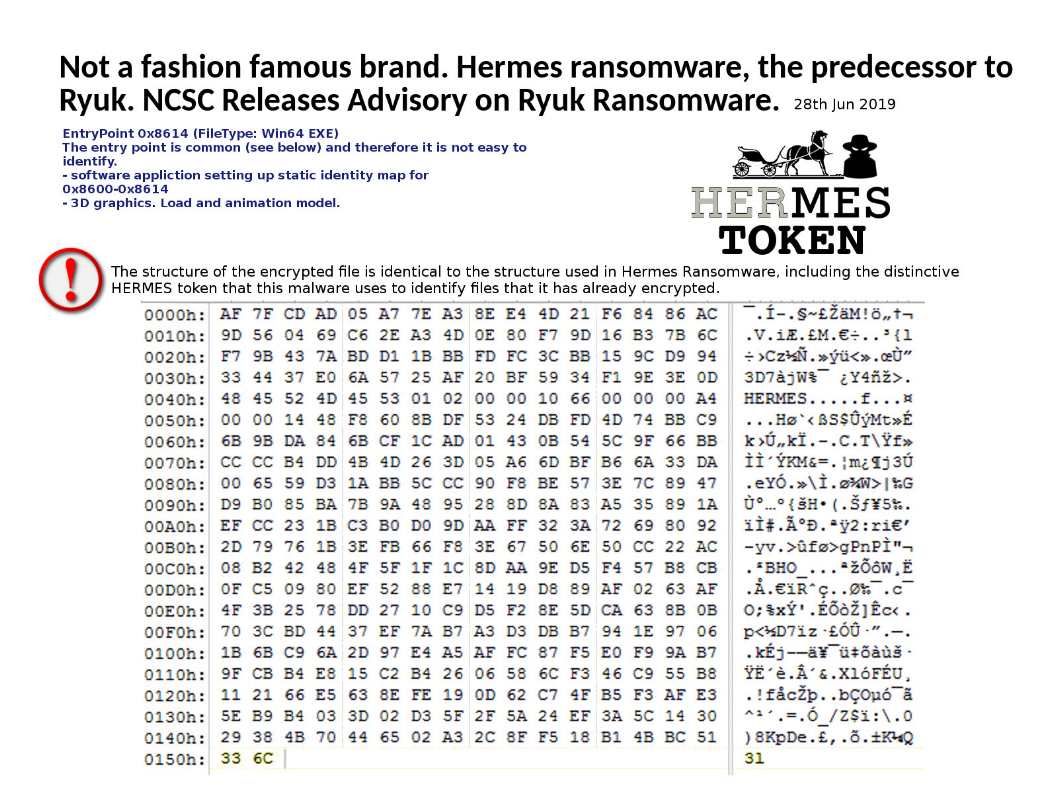
The structure of the encrypted file is identical to the structure used in Hermes Ransomware, including the distinctive HERMES token that this malware uses to identify files that it has already encrypted.
Remark: Cyber Criminals distributing Hermes Ransomware via dangerous malspam that contains Weaponized Password protected Word documents to encrypt the system files and lock the victim’s computer.
The pre-operation of Ryuk ransomware on infected computers:
- Volume Shadow Server & Backup Kill
- Installed lang check:
SYSTEM\CurrentControlSet\Control\Nls\Language\
InstallLanguage
0419 (Russia)
0422 (Ukrainian)
0423 (Belarusian) - Arp Blaclklist check
- GetComputerName check
- Process kill
Advisory report for download – https://www.ncsc.gov.uk/news/ryuk-advisory