Use your iPhone play H.264 (MP4) video is annoying, the problem is that sometimes the videos work, sometimes it doesn’t. As a matter of fact, the IOS are quite unstable with mp4 format and h.264 on HTML5. But why is that people always encounter the problem of MP4 not playing on iPhone 7/6S/6?
iPhone 7 Only Supports Two Types of MP4 Files Natively
1. MP4 video with H.264 codec, and the MP4 should meet below specifications:
Up to 1080P, 30fps, high profile level 4.1 with AAC-LC audio below 160Kbps, 48kHz and stereo audio.
2. MP4 video with MPEG-4 codec, and have to meet another different specifications of:
Up to 2.5 Mbps, 640 X 480 resolution, 30fps, simple profile with AAC-LC audio up to 160 Kbps, 48kHz and stereo audio.
iPhone 4S
Compatible with H.264 or MPEG-4 video format with the following specifications:If it is H.264 video, it should meet: up to 1080p, 30 frames per second, High Profile level 4.1 with AAC-LC audio up to 160 Kbps, 48kHz, stereo audio in .m4v, .mp4, and .mov file formats;
If it is MPEG-4 video, it should meet: up to 2.5 Mbps, 640 by 480 pixels, 30 frames per second, Simple Profile with AAC-LC audio up to 160 Kbps per channel, 48kHz, stereo audio in .m4v, .mp4, and .mov file formats;
Think it over? The development life cycle on iphone 4s to iphone 7 not a short period, why there were no improvement in this area?
The culprit
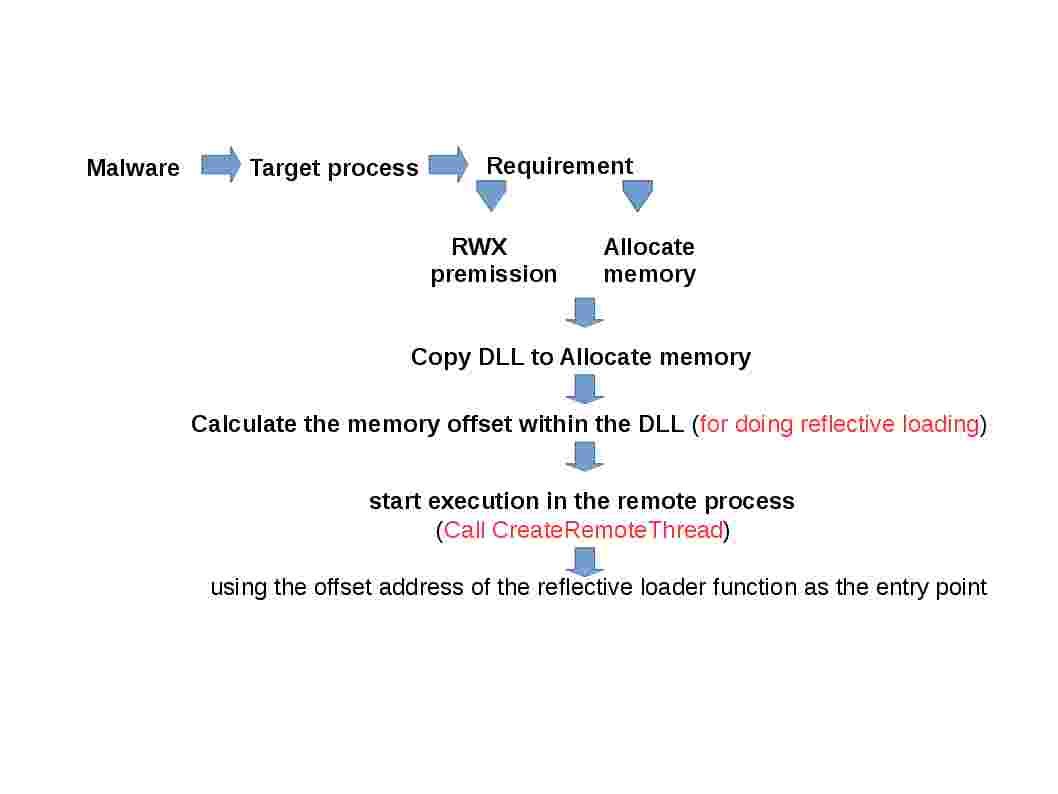
a. iOS10 videos not playing with X-Accel-Redirect
b. X-accel allows for internal redirection to a location determined by a header returned from a backend.
c. Different browsers (Firefox, Safari & IE) have different policies mechanism to cache.
- TTL hold the valid time of dns entry
- Browser should cache until TTL expires
But the major factor bother Apple development team not the above items, the issue is that they found a vulnerability in Safari.

The instigator of this vulnerability
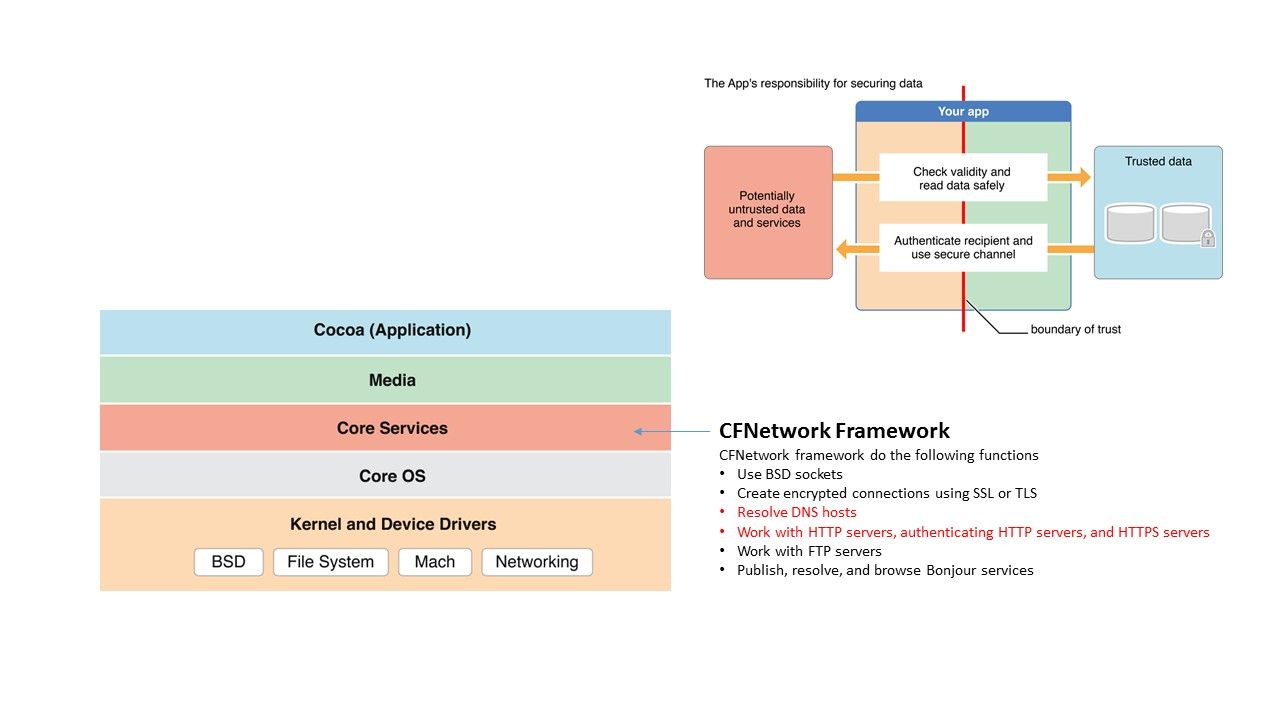
Refer to below diagram, CFNetwork Framework embedded in core services layer. It provides the following functions.
- Use BSD sockets
- Create encrypted connections using SSL or TLS
- Resolve DNS hosts
- Work with HTTP servers, authenticating HTTP servers, and HTTPS servers
- Work with FTP servers
- Publish, resolve, and browse Bonjour services
Unfortunately the vulnerability found that Safari support of HTTP/0.9 and accidentally allow cross-protocol exploitation of non-HTTP services using DNS rebinding. The remediation step of Apple is that restrict HTTP/0.9 responses to default ports and canceling resource loads if the document was loaded with a different HTTP protocol version. Sounds like a middle man verify the communication between external and core services. However it break X-Accl-Redirect function thus H.264 (MP4) doesn’t work properly.

Reference:
Apple remediation of CVE-2016-4760 (About the security content of iOS 10)
iOS 10 – Released September 13, 2016
WebKit
Available for: iPhone 5 and later, iPad 4th generation and later, iPod touch 6th generation and later
Impact: A malicious website may be able to access non-HTTP services
Description: Safari’s support of HTTP/0.9 allowed cross-protocol exploitation of non-HTTP services using DNS rebinding. The issue was addressed by restricting HTTP/0.9 responses to default ports and canceling resource loads if the document was loaded with a different HTTP protocol version.
Web browser design weakness (DNS pinning) & DNS rebinding vulnerability
Web browser pins host name to IP address but pin is easily to release with below command.
<img src:http://xxx.com:81/>
DNS rebinding vulnerability: Attacker will respond with the XML below:
<?xml version"1.0"?>
<cross-domain-policy>
<allow-access-from domain="*" to-ports="*" />
</cross-domain-policy>
DNS rebinding scenario replay:
- Victim visits the malicious Web site hunt.com and loads the script it contains.
2. The attacker then changes the DNS entry of hunt.com in order to resolve to the internal server’s IP address, which is the target. In addition, the attacker disconnects the Web server that was running on the original IP address.
3. The script uses a timed event (setIntervall or setTimeout) to load a Web page from hunt.com. (Different browsers (Firefox, Safari & IE) have different policies mechanism to cache).
4. The victim’s Web browser executes the script and tries to connect back to hunt.com using the IP address, which is bound to it due to DNS pinning. But, as the Web server is no longer available, the connection is rejected and DNS pinning is dropped, due to the weakness described in the previous section.
5. The browser then drops the DNS pinning and does a new DNS lookup request for hunt.com. This time, the response results in a different IP address; the browser has removed from its cache the previous mapping of the server hostname (hunt.com) to an IP address, so cannot be protected from the misdirection.
6. As the new IP address points to the internal server, the attacker’s script is now able to access the internal server’s content and reveal it.
Information Supplement – iOS security function:
The security feature set on iOS or Mac OS design are advanced. The Security Server (securityd) is a daemon running in macOS and iOS that implements several security protocols, such as encryption, decryption, and (in macOS) authorization computation. The Security Agent is a separate process that provides the user interface for the Security Server in macOS (not iOS). Its primary purpose is to request authentication whenever an app requests additional privileges.
The iOS operating system isolates each and every app on the system. Apps are not allowed to view or modify each other’s data, business logic, and so on. Isolation prevents one app from knowing whether any other app is present on the system or whether apps can access the iOS operating system kernel until the device is jailbroken. This ensures a high degree of separation between the app and operating system.
iOS provides two types of isolation:
- Process isolation
- Filesystem isolation