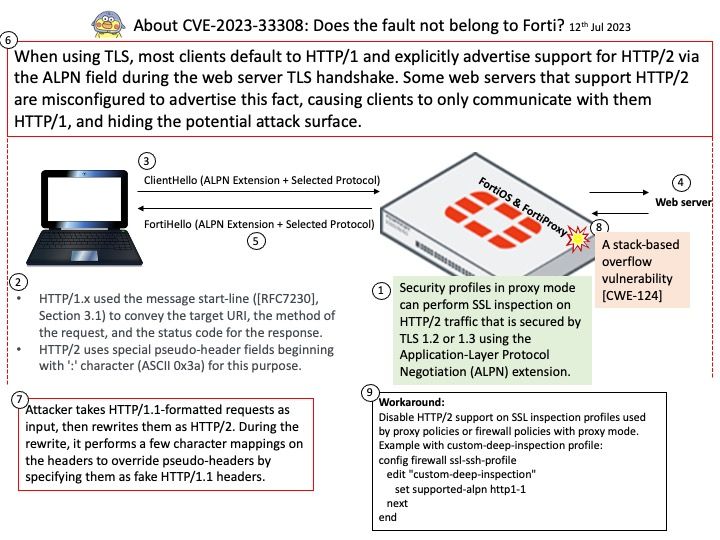
Preface: Security profiles in proxy mode can perform SSL inspection on HTTP/2 traffic that is secured by TLS 1.2 or 1.3 using the Application-Layer Protocol Negotiation (ALPN) extension.
Background: In HTTP/2, a series of “pseudo-headers” is used to send key information about the message. Most notably, several pseudo-headers effectively replace the HTTP/1 request line and status line. In total, there are five pseudo-headers: :method – The HTTP method of the request, such as GET or POST .
Deep packet inspection evaluates the data part and the header of a packet that is transmitted through an inspection point, weeding out any non-compliance to protocol, spam, viruses, intrusions, and any other defined criteria to block the packet from passing through the inspection point.
Security profiles in proxy mode can perform SSL inspection on HTTP/2 traffic that is secured by TLS 1.2 or 1.3 using the Application-Layer Protocol Negotiation (ALPN) extension.
Vulnerability details: A stack-based overflow vulnerability [CWE-124] in FortiOS & FortiProxy may allow a remote attacker to execute arbitrary code or command via crafted packets reaching proxy policies or firewall policies with proxy mode alongside SSL deep packet inspection.
Ref: When using TLS, most clients default to HTTP/1 and explicitly advertise support for HTTP/2 via the ALPN field during the web server TLS handshake. Some web servers that support HTTP/2 are misconfigured to advertise this fact, causing clients to only communicate with them HTTP/1, and hiding the potential attack surface. Attacker takes HTTP/1.1-formatted requests as input, then rewrites them as HTTP/2. During the rewrite, it performs a few character mappings on the headers to override pseudo-headers by specifying them as fake HTTP/1.1 headers.
Official announcement: For details, please refer to the link – https://www.fortiguard.com/psirt/FG-IR-23-183