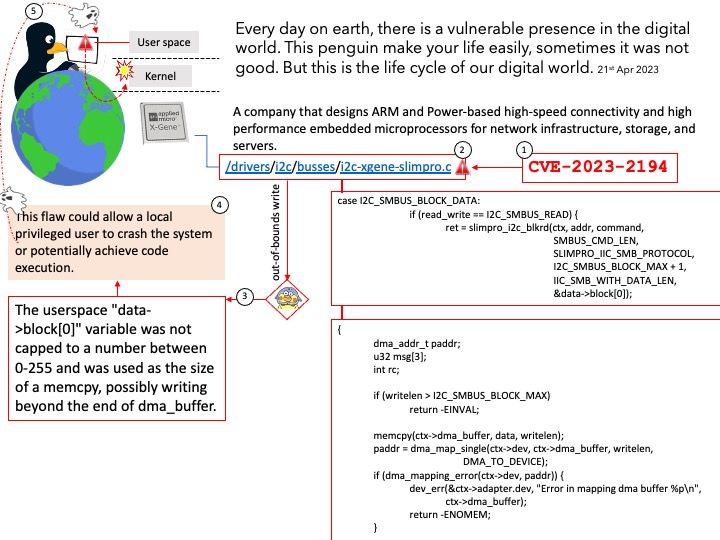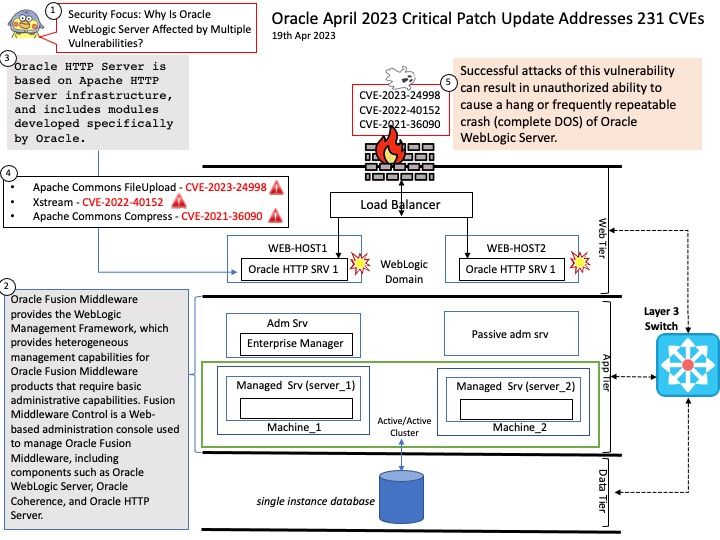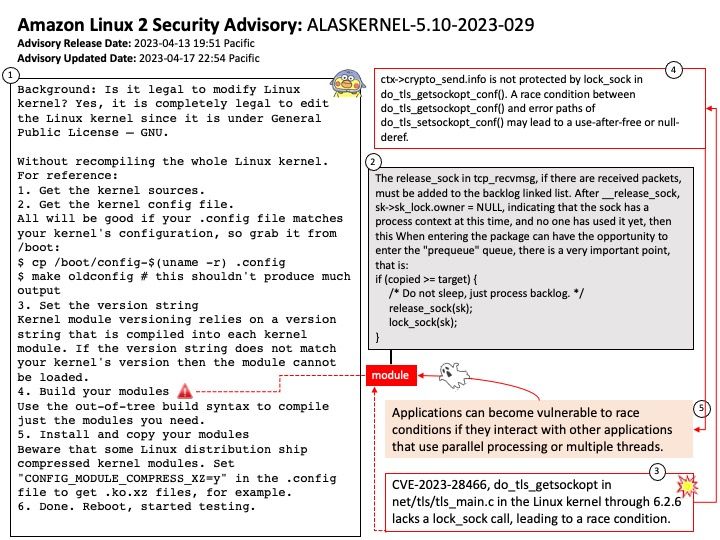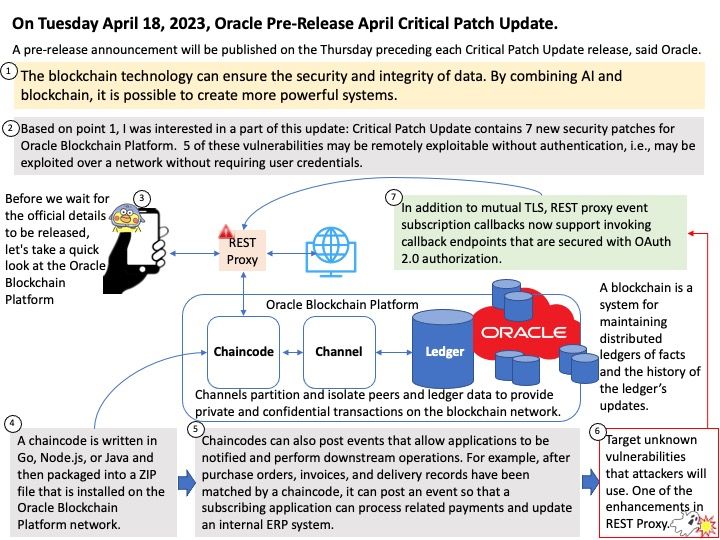
Preface: Open source software fosters collaboration. As such, open source software will continue to play a key role in modern software development.
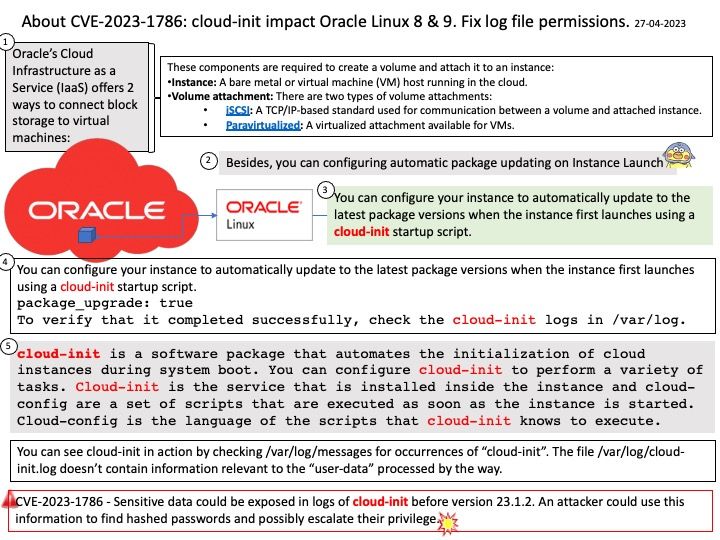
Background: cloud-init is a software package that automates the initialization of cloud instances during system boot. You can configure cloud-init to perform a variety of tasks. Cloud-init is a service used for customizing Linux-based operating systems in the cloud.
Cloud-init is the service that is installed inside the instance and cloud-config are a set of scripts that are executed as soon as the instance is started. Cloud-config is the language of the scripts that cloud-init knows to execute. cloud-init is developed and released as free software under both the GPLv3 open source license and the Apache License version 2.0.
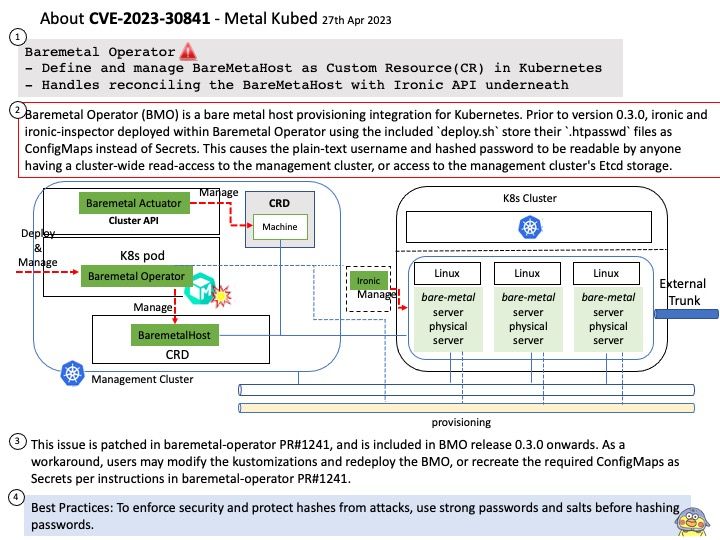
Vulnerability details: Sensitive data could be exposed in logs of cloud-init before version 23.1.2. An attacker could use this information to find hashed passwords and possibly escalate their privilege. (CVE-2023-1786)
Official announcement: For details, please refer to the relevant link – https://linux.oracle.com/errata/ELSA-2023-12298.html
Reference: With structured logging, your logs are relational data sets, like key/value pairs, rather than just text. Structured logging has the advantage of being more easily searched and analyzed. It can also help with keeping sensitive data out of your logs.
The most common structured logging format is JSON since it is the standard message format for every message parsing between systems and within applications.
Understand that, it is require tool convert Common Event Format (CEF) to JSON .
Perhaps there is other solution it can help. For example: Fix log file permissions.