Preface: Many users agree that learning Apex is simpler than learning Java because there is less syntax.
Background: Apex is a proprietary language developed by Salesforce.com. It is a strongly typed, object-oriented programming language that allows developers to execute flow and transaction control statements on the Force.com platform server in conjunction with calls to the Force.com API.
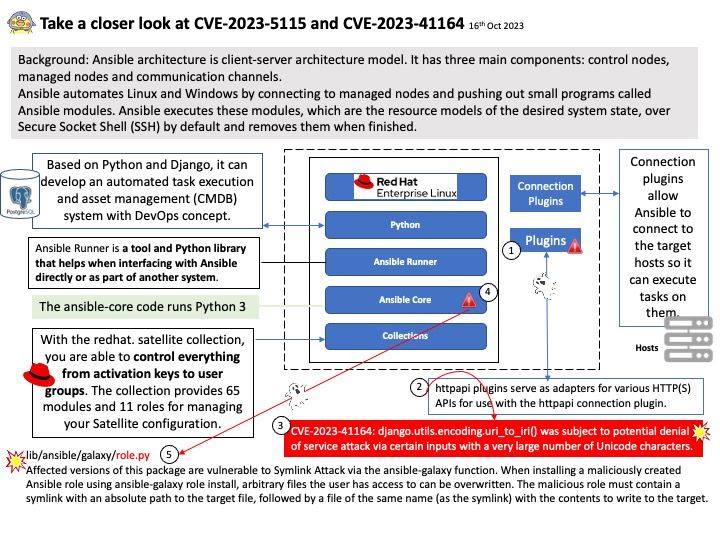
Remark: If file (libdexfile[.]so) is belongs APEX_MODULE_LIBS. Whereby, I change my security focus appoint to APEX proprietary language.
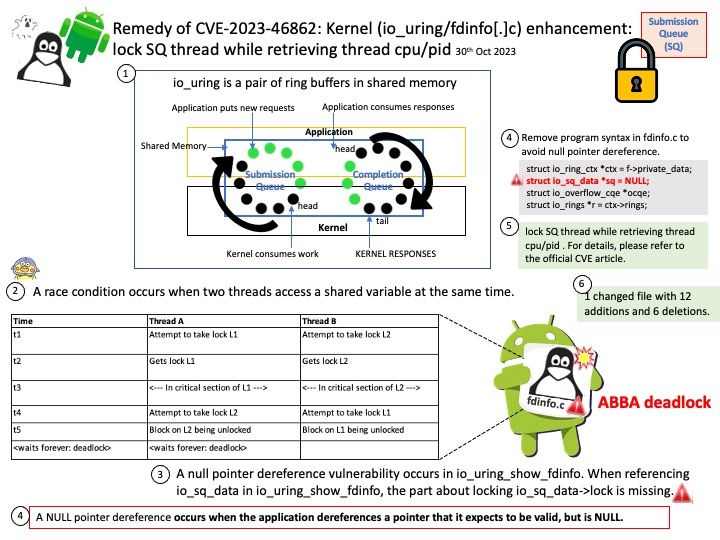
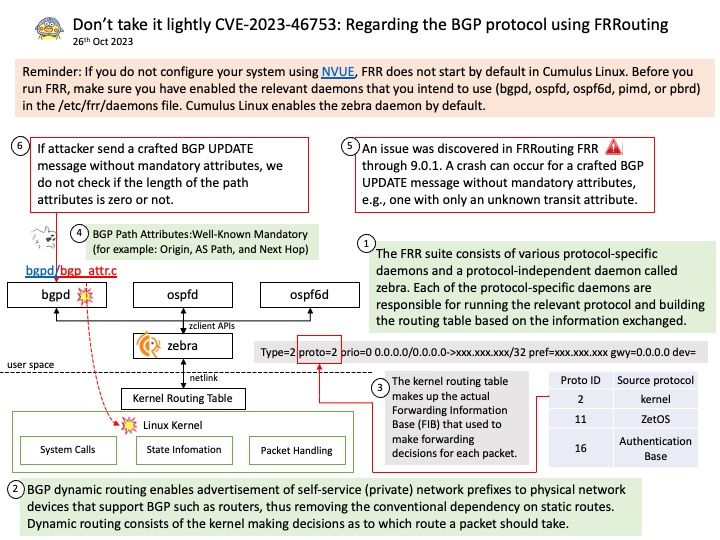
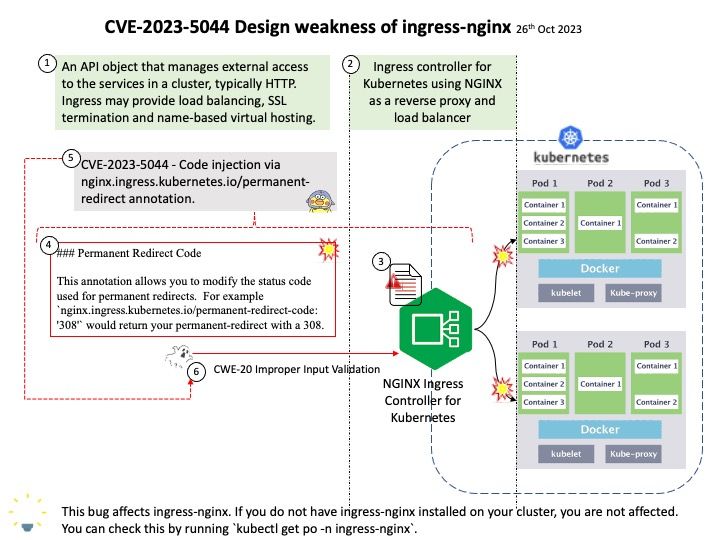
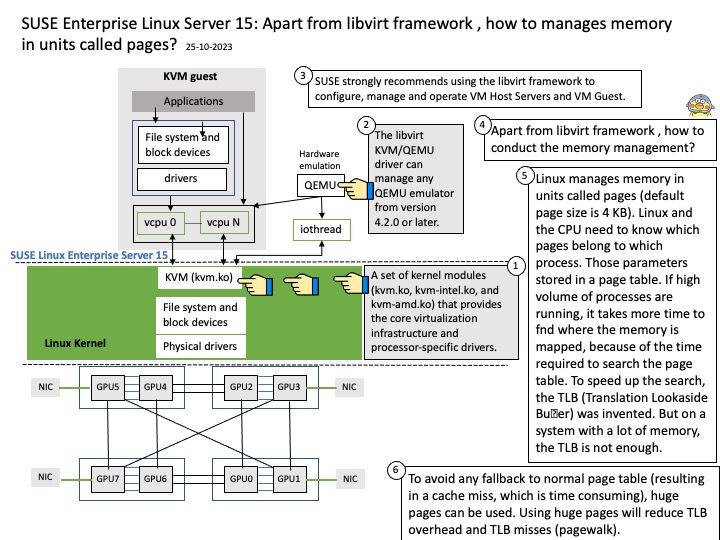
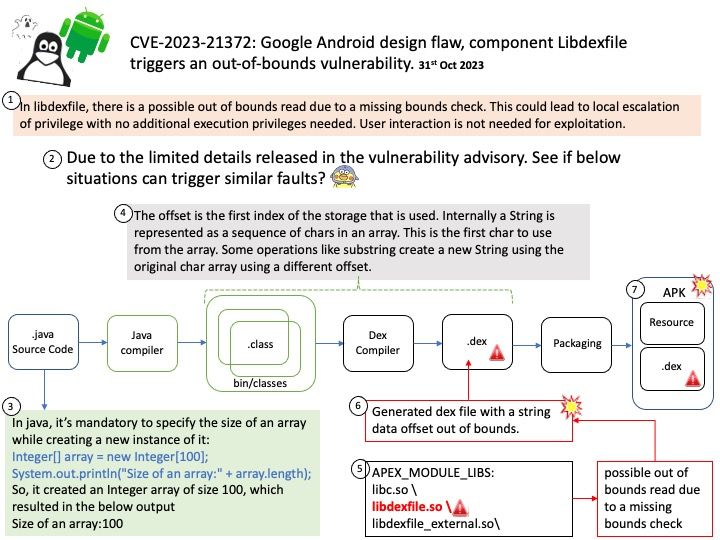
Vulnerability details: In libdexfile, there is a possible out of bounds read due to a missing bounds check. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation.
Remark: Due to the limited details released in the vulnerability advisory. See if attached diagram situations can trigger similar faults?
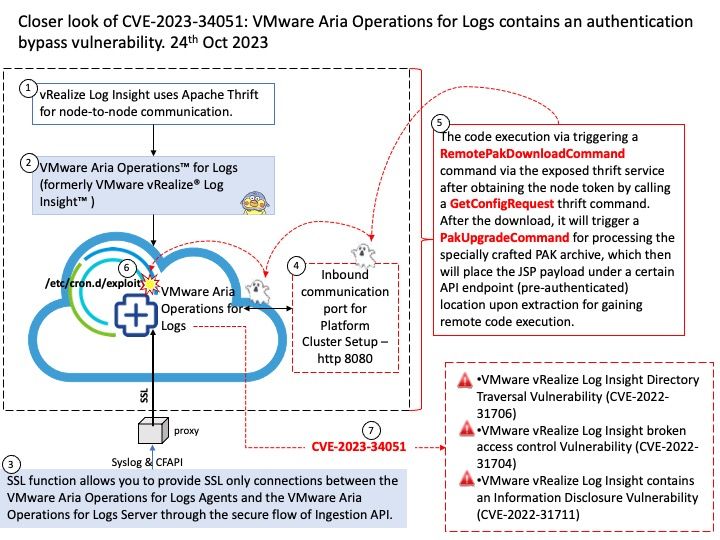
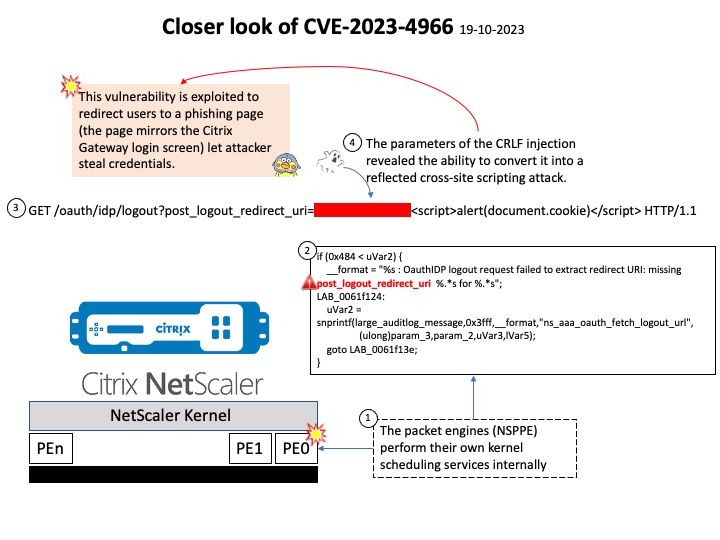
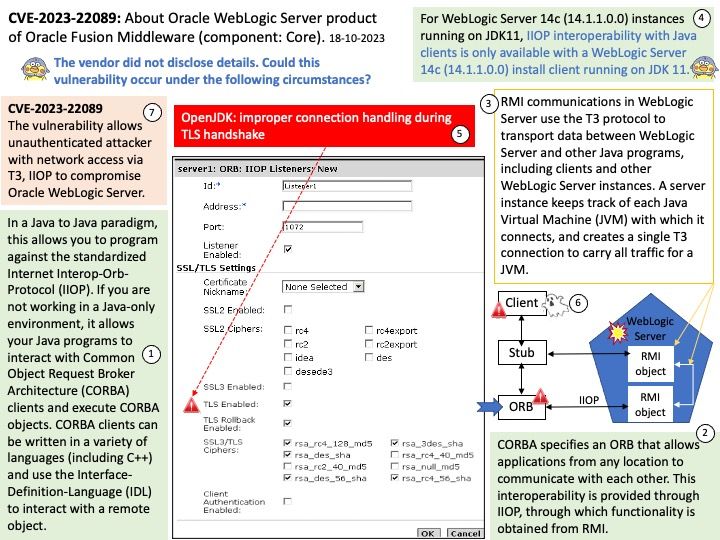
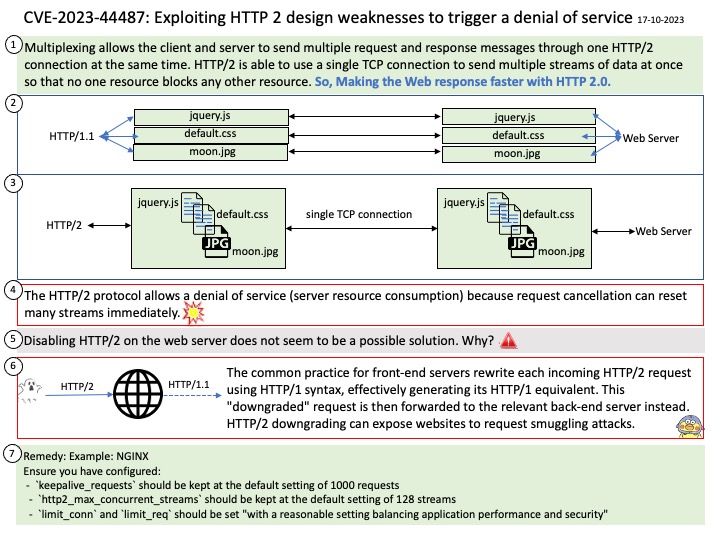
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-21372