.jpg)
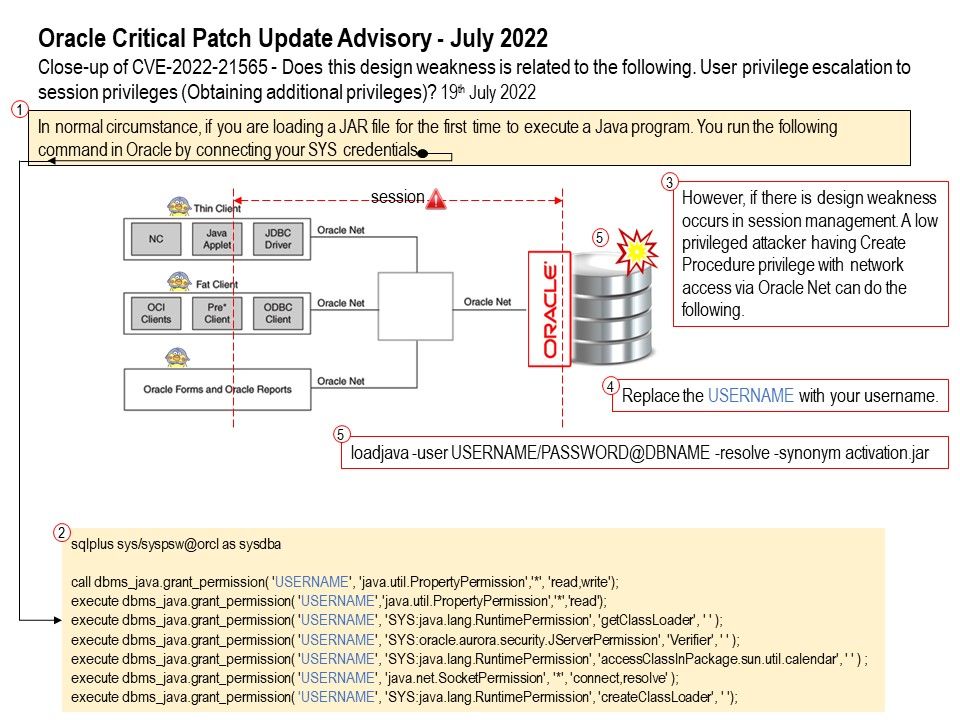
Preface: Last September (2021) ICS adviced that the public should be concerned about the multiple vulnerabilities encountered by Modbus products. This product model is (TBox) from the supplier Ovarro.
Such vulnerabilities were documented in a CVE article published until this week (July 28, 2022). The record number is CVE-2021-22642.
Perhaps reader has confuse about this CVE record because same CVE number was found on CISA published on last year (2021) September. I think may be it has admended on vulnerability description and therefore has this matter occurs.
Maybe readers are confused about this CVE record, because the same CVE number was found in a CISA article published last September (2021). I think a modification to the original vulnerability description may be required. Thus this happens.
Reference:
- ICS Advisory (ICSA-21-054-04) – Original release date: September 23, 2021
https://www.cisa.gov/uscert/ics/advisories/icsa-21-054-04 - Relevant CVE record details in the US National Vulnerability Database. Please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2021-22642
Security focus – Related design weakness brought to my attention
An attacker could use specially crafted invalid Modbus frames to crash the Ovarro TBox system.
As usual, the technical article only writes the description of the vulnerability, but not the root cause. Maybe it’s public safety related, so it wasn’t disclosed.
As far as I know, TBOX products are designed to provide a safe and robust RTU solution for remote automation and monitoring of critical asset functions. Maybe I’ll try to do a quick research and see if it finds hints for your reference.
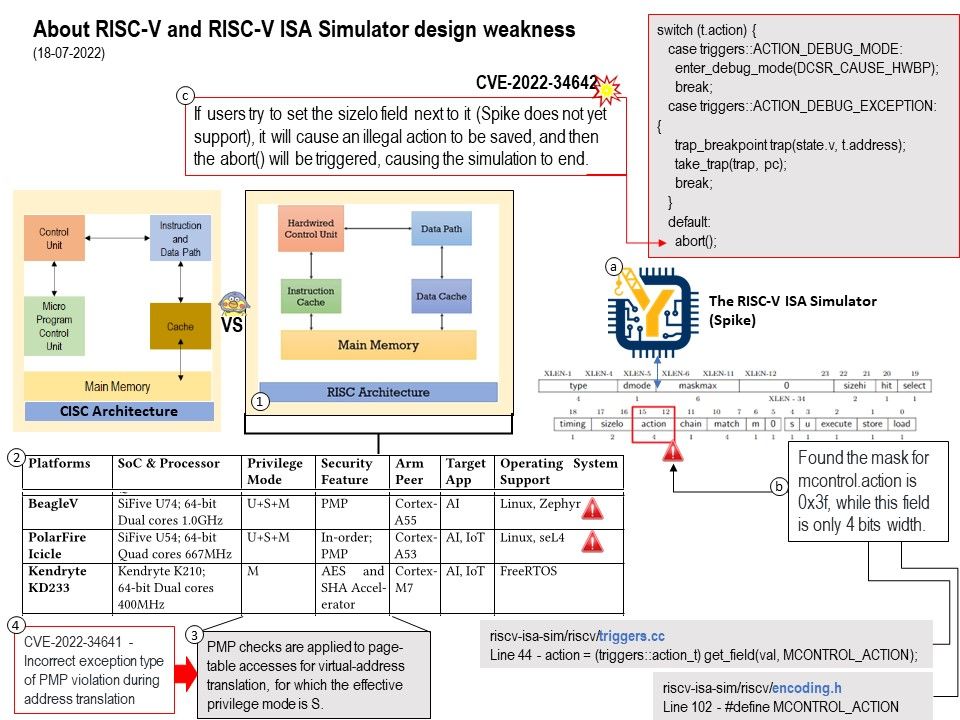
Observation (CVE-2021-22642): The MODBUS/TCP protocol contains also vulnerability that could allow an attacker to cause a denial of service (DoS) condition on a targeted system. The vulnerability is due to an implementation error in the affected protocol when processing Read Discrete Inputs request and response messages.
An unauthenticated, remote attacker could exploit the vulnerability by sending request or response parameters that contain malicious values for the data field option to a system that contains a vulnerable MODBUS/TCP implementation. The processing of the messages could trigger a DoS condition on the vulnerable system.
Official announcement (ovarro) – https://www.ovarro.com/content-media/assigned/89928/TBOX-SA-2021-0005.pdf
.jpg)

.jpg)
.jpg)