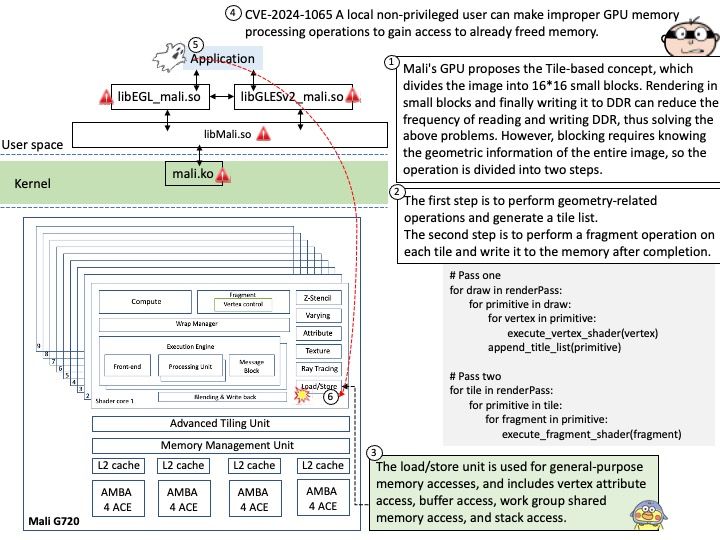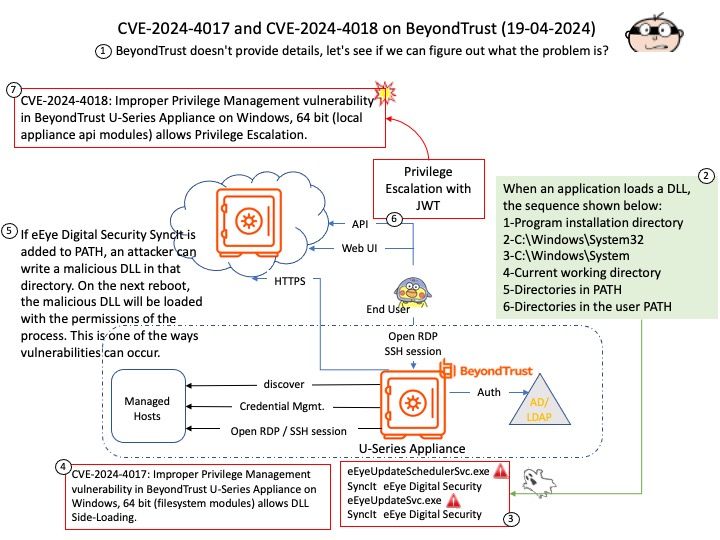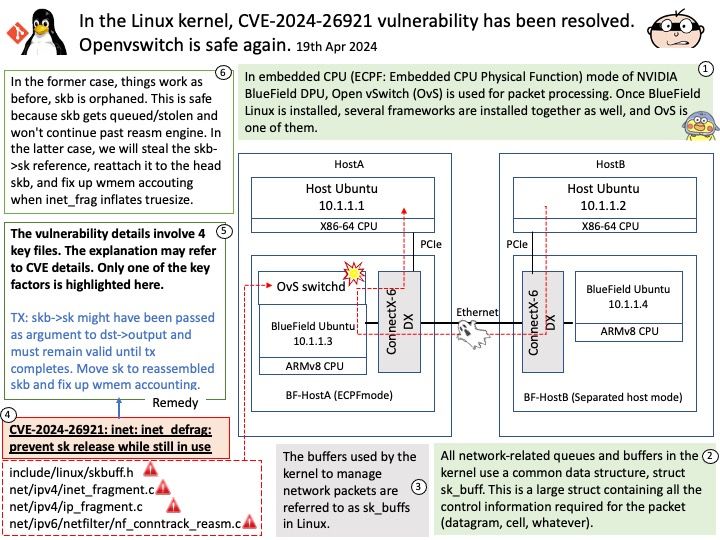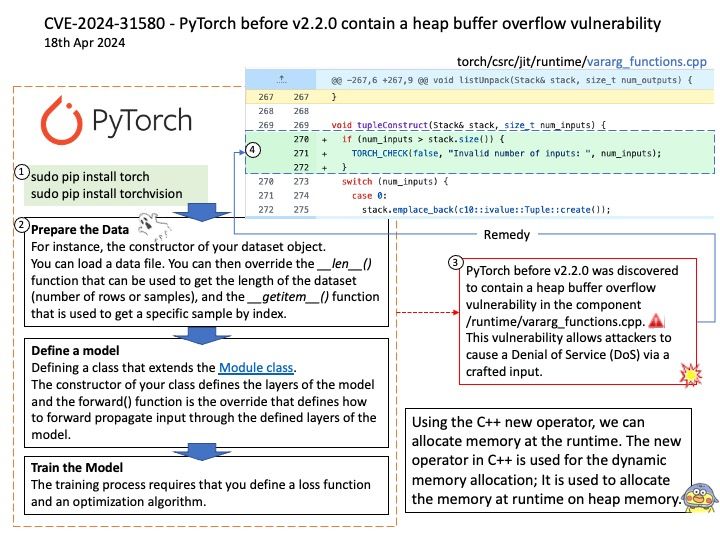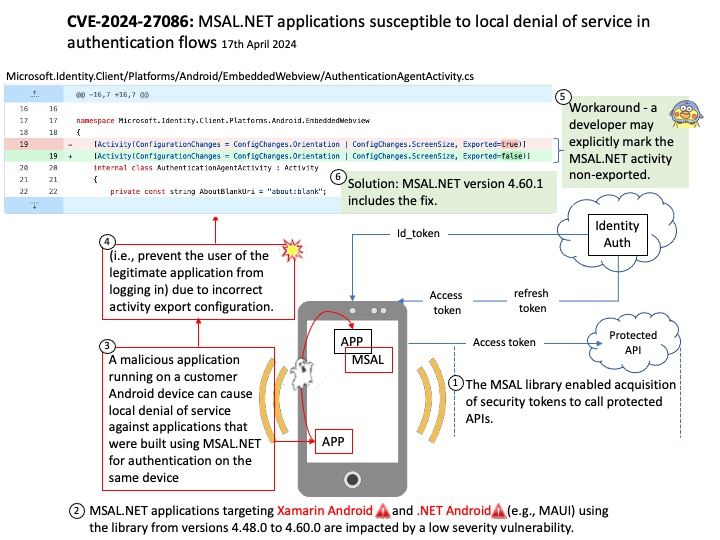
Preface: What are LLM Apps? LLM apps, or Large Language Model applications, are applications that leverage the capabilities of Large Language Models (LLMs) to perform a variety of tasks. LLMs are a type of artificial intelligence (AI) that uses deep learning techniques and large datasets to understand, generate, and predict new content.
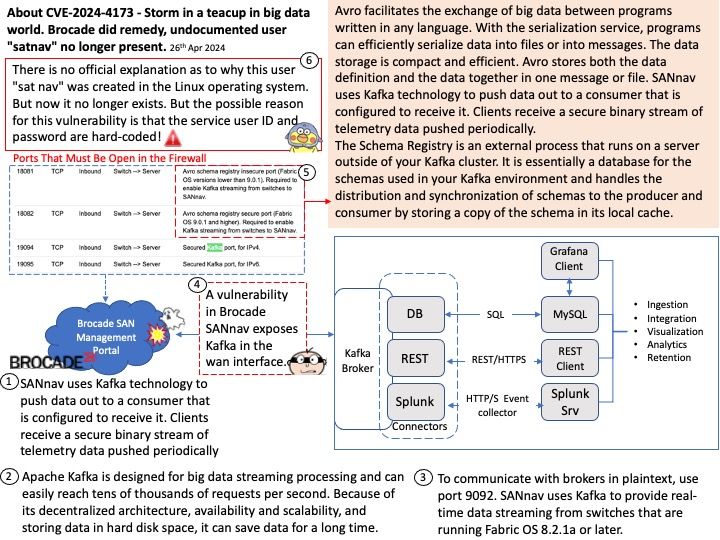
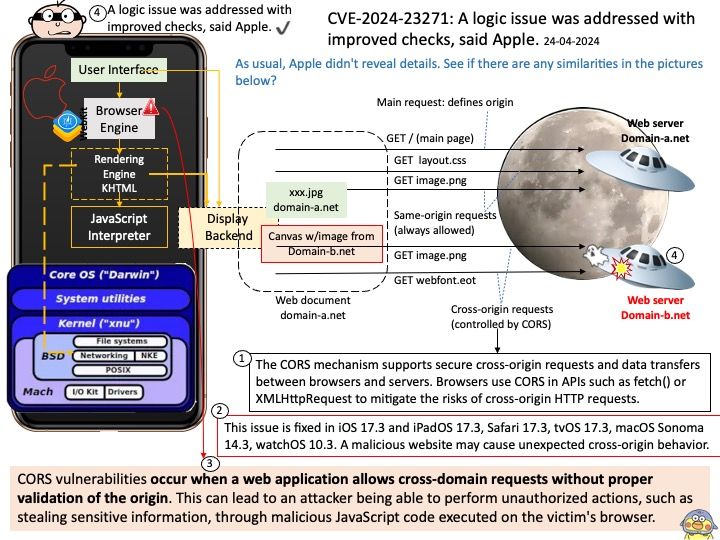
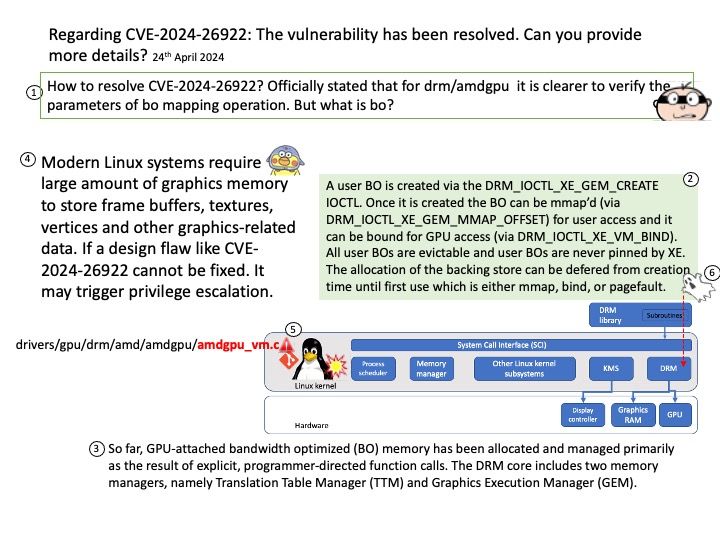
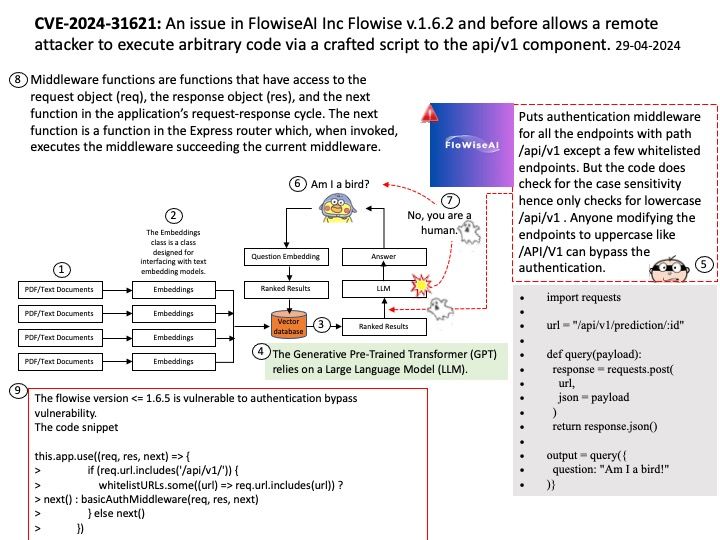
Background: Flowise uses low-code approach that enable developers to manage the whole lifecycle of building LLMs apps in production. From protoyping, evaluation, to iterations.
Ref: Middleware functions are functions that have access to the request object (req), the response object (res), and the next function in the application’s request-response cycle. The next function is a function in the Express router which, when invoked, executes the middleware succeeding the current middleware.
Vulnerability details: An issue in FlowiseAI Inc Flowise v.1.6.2 and before allows a remote attacker to execute arbitrary code via a crafted script to the api/v1 component.
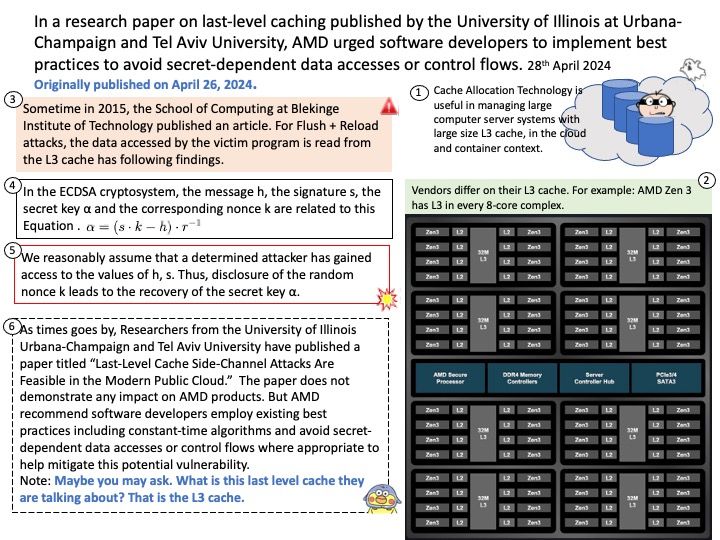
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2024-31621