Preface: Virtual computer world like a fruit punch, anything can mix into it.
Background: OpenStack is a cloud computing software developed by NASA and Rackspace. It is licensed under the Apache license and is a free and open source software. Their customer including Shanghai Electric, China Mobile, LINE and China UnionPay .
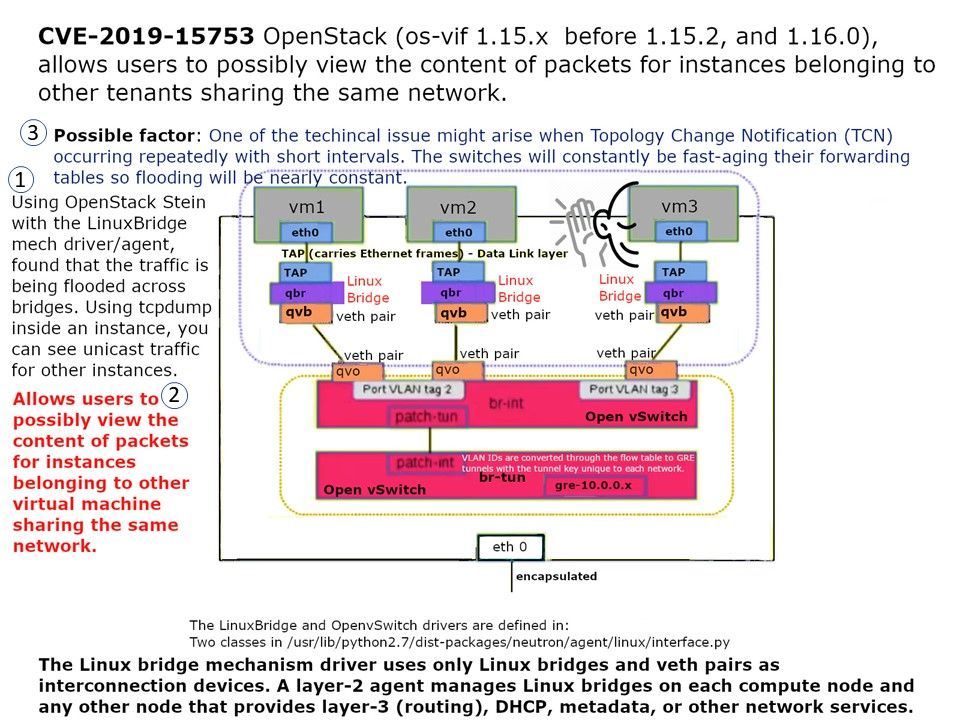
Vulnerability details: In OpenStack os-vif 1.15.x before 1.15.2, and 1.16.0, a hard-coded MAC aging time of 0 disables MAC learning in linuxbridge, forcing obligatory Ethernet flooding of non-local destinations, which both impedes network performance and allows users to possibly view the content of packets for instances belonging to other tenants sharing the same network. Only deployments using the linuxbridge backend are affected. This occurs in PyRoute2.add() in internal/command/ip/linux/impl_pyroute2.py.
Possible factor: One of the techincal issue might arise when Topology Change Notification (TCN) occurring repeatedly with short intervals. The switches will constantly be fast-aging their forwarding tables so flooding will be nearly constant.
Remedy status: In Progress → Fix Released (30th Aug 2019) https://review.opendev.org/678098