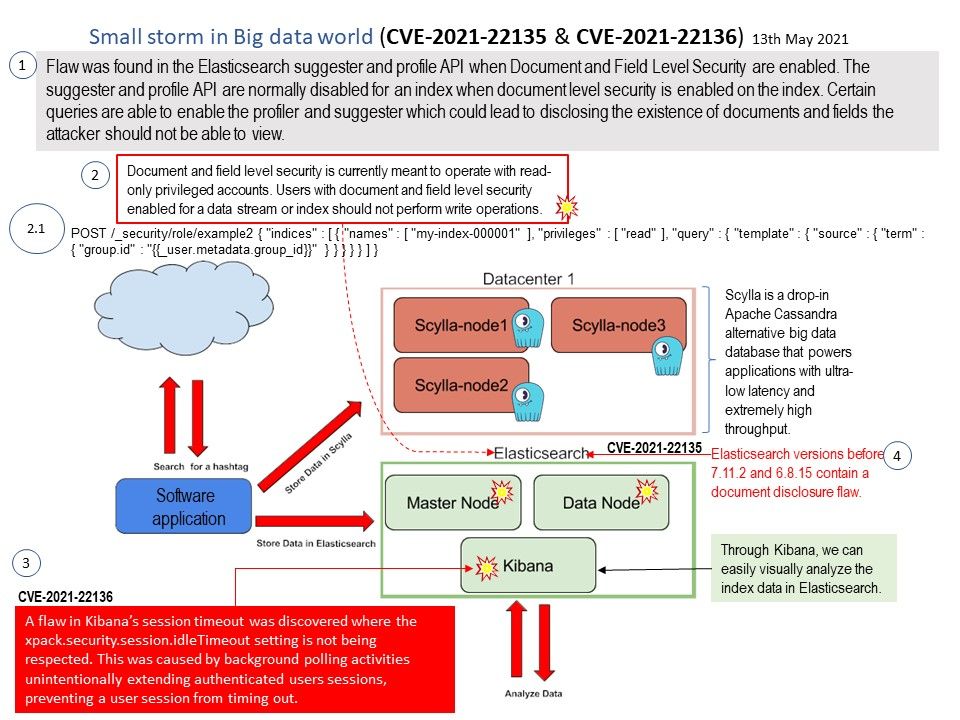
Preface: A Russian-speaking outfit called DarkSide offered would-be computer crooks not just the tools, but also customer support, New York Times said.
My observation: My observation: Perhaps cyber criminals learn from practice. They know the system infrastructure weakness of industrial especially oil, powers supply facilities even logistic industry.
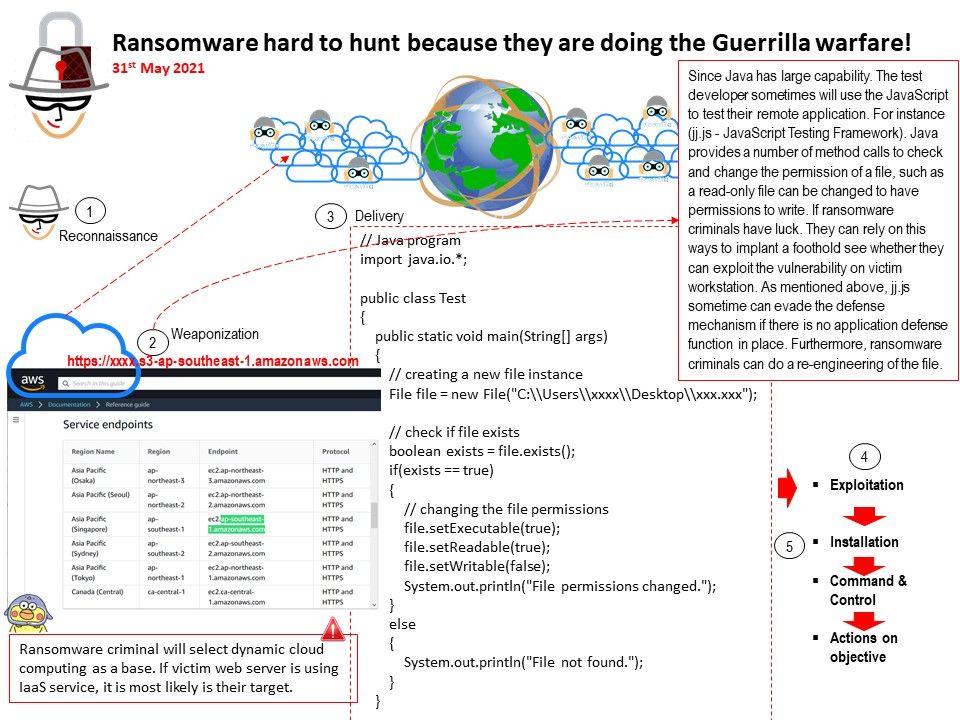
Since Java has large capability. The test developer sometimes will use the JavaScript to test their remote application. For instance (jj[.]js – JavaScript Testing Framework). Java provides a number of method calls to check and change the permission of a file, such as a read-only file can be changed to have permissions to write. If ransomware criminals have luck. They can rely on this ways to implant a foothold see whether they can exploit the vulnerability on victim workstation. As mentioned above, jj.js sometime can evade the defense mechanism if there is no application defense function in place. Furthermore, ransomware criminals can do a re-engineering of the file.
Remark: ransomware criminal will select dynamic cloud computing as a base. If victim web server is using IaaS service, it is most likely is their target.
NYTimes headline – https://www.nytimes.com/2021/05/29/world/europe/ransomware-russia-darkside.html
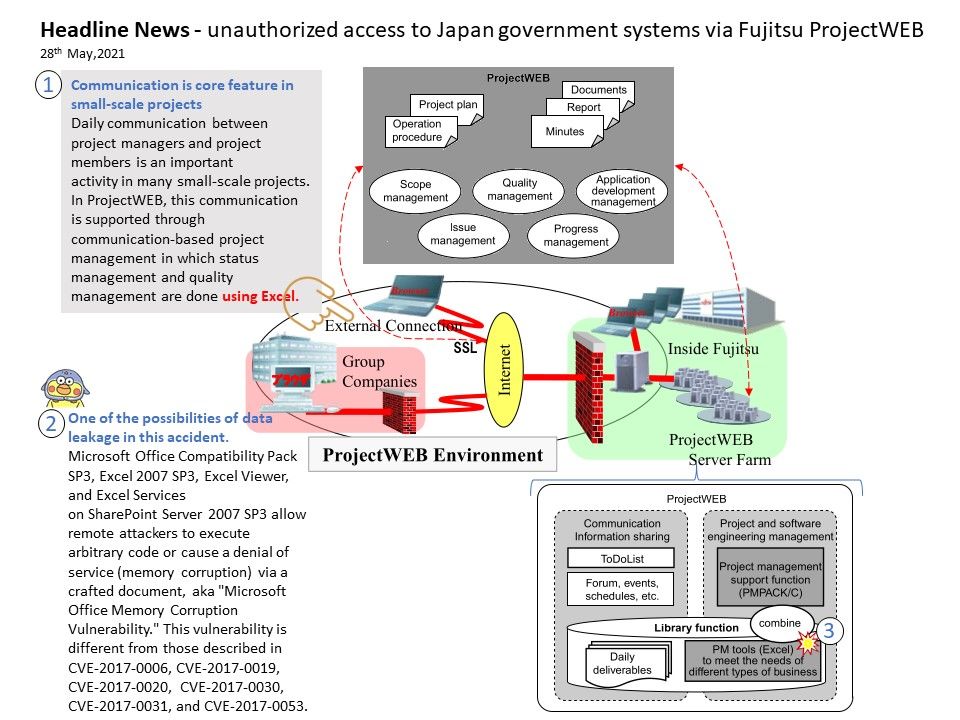
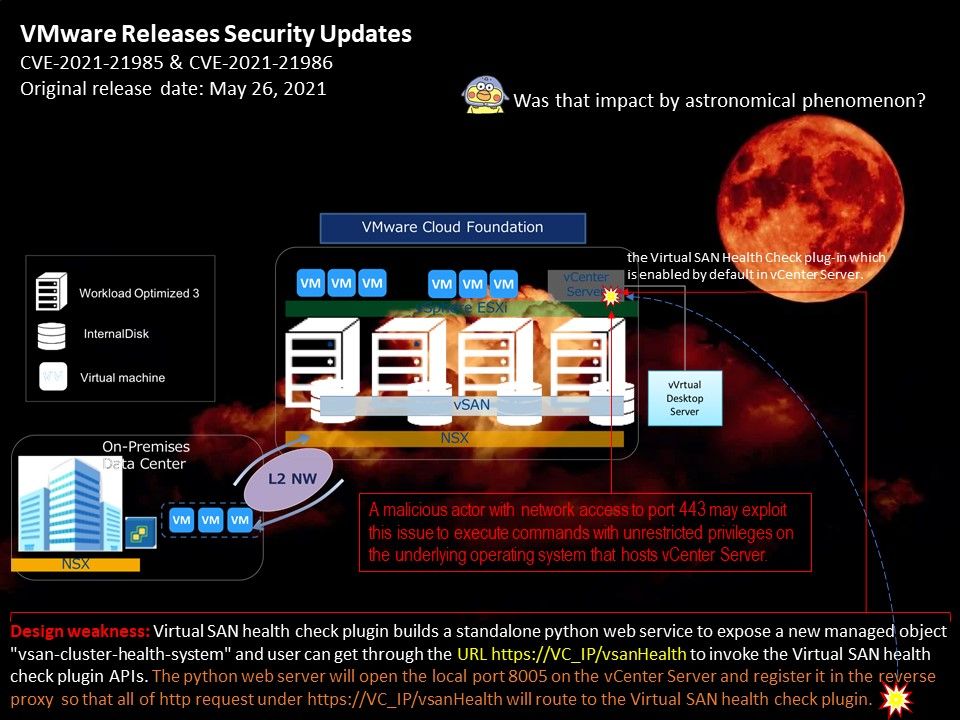
(1).jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)