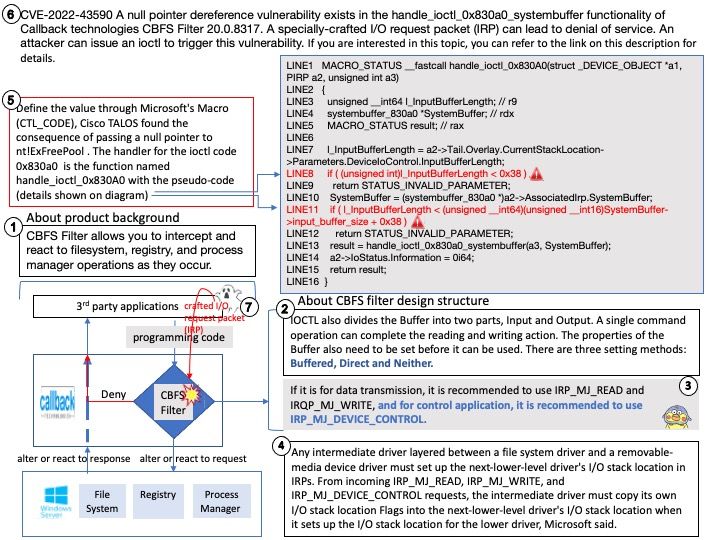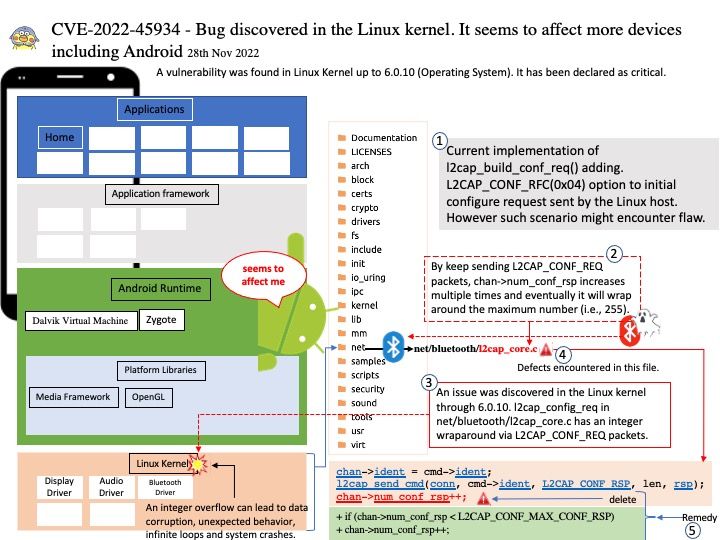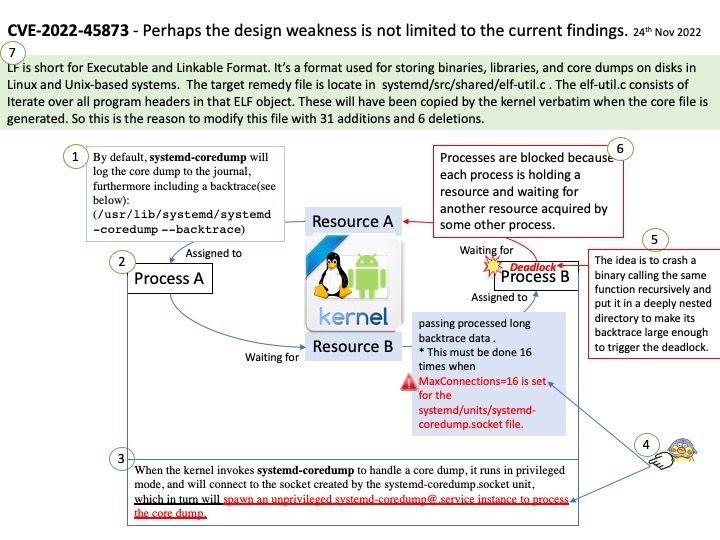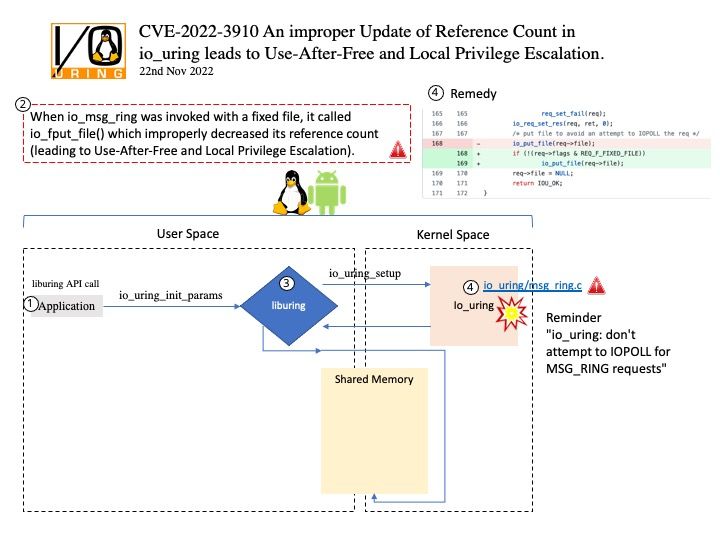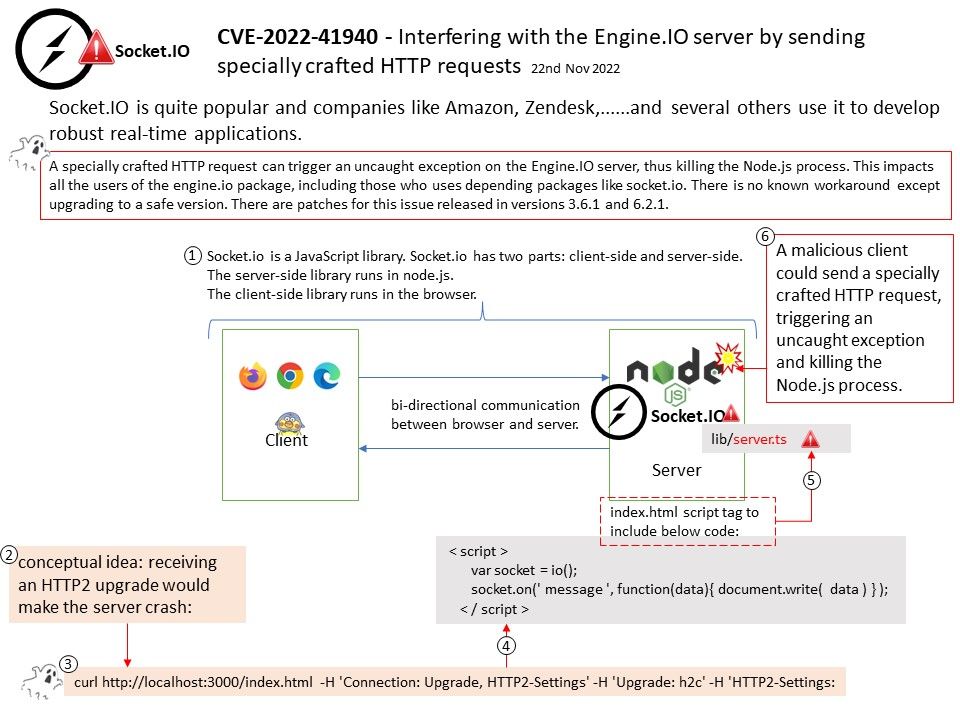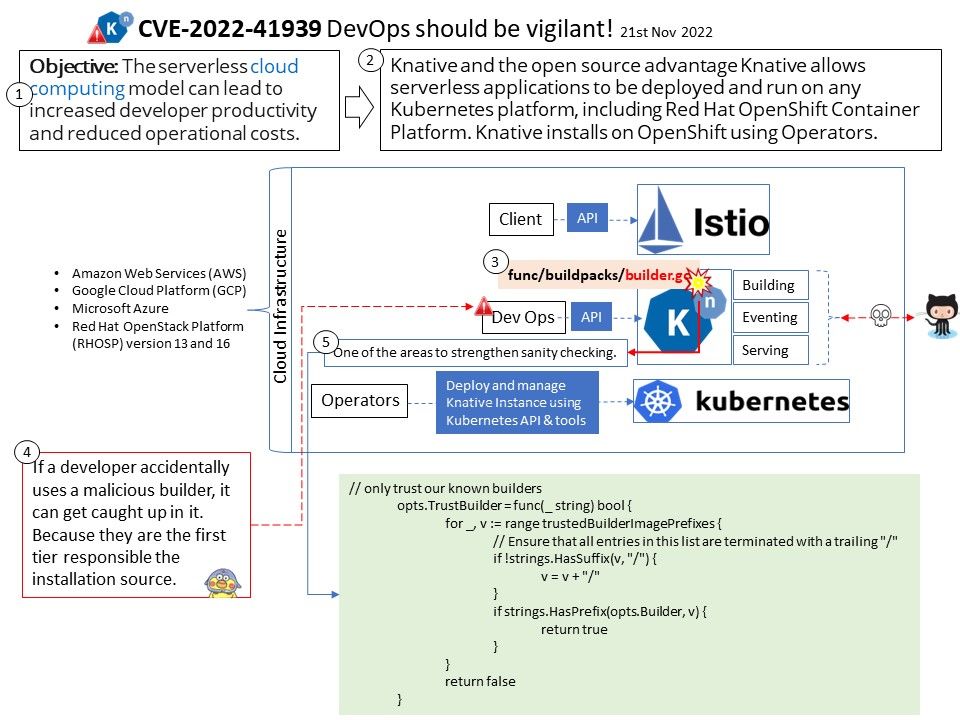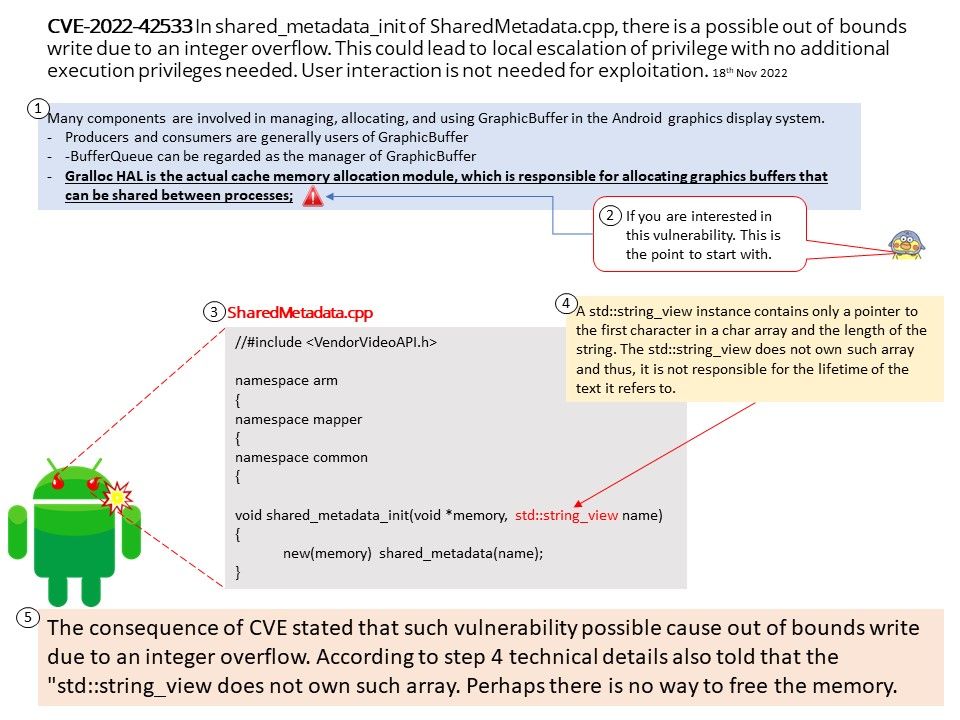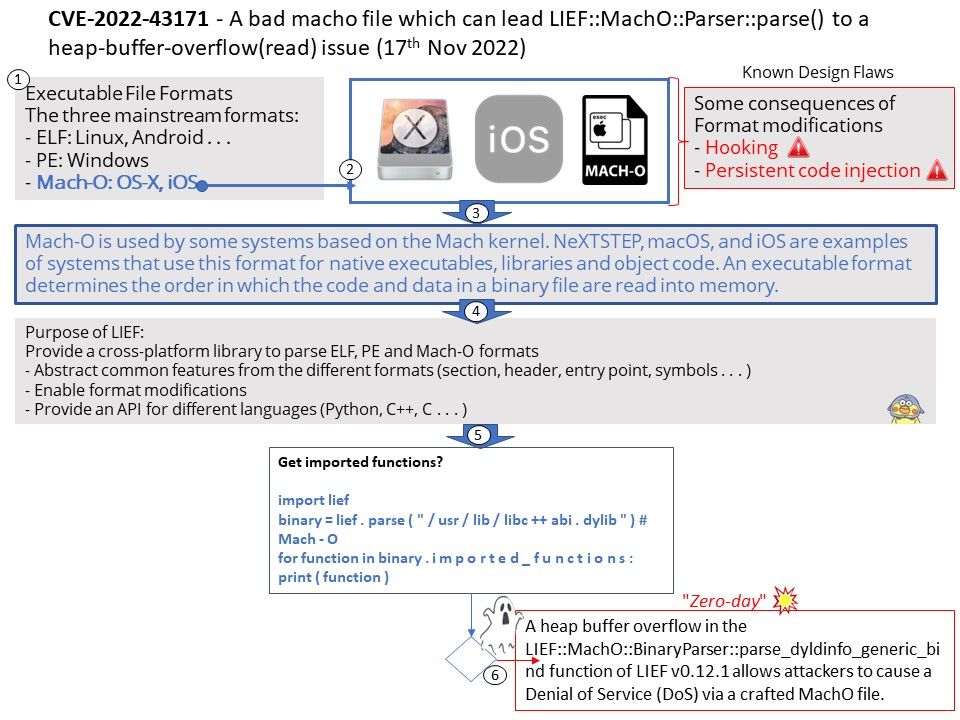
Preface: In the ARM architecture, synchronous control is transferred between the normal Non-secure state to Secure state through System Monitor Call exceptions
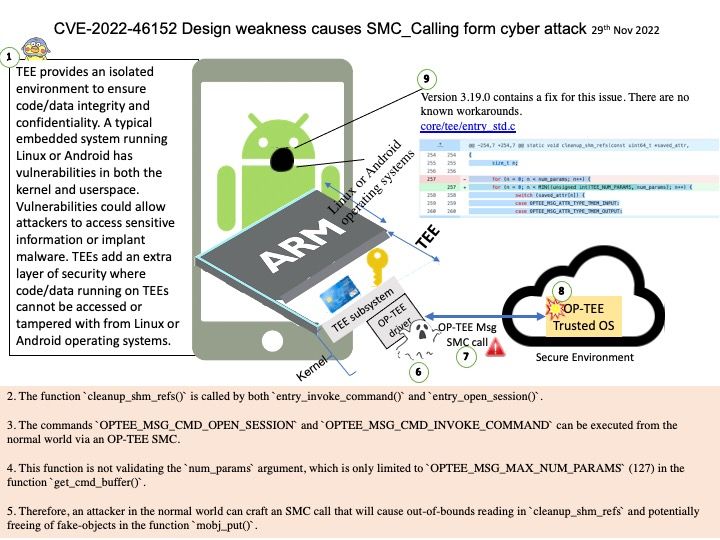
Background: TEE provides an isolated environment to ensure code/data integrity and confidentiality. A typical embedded system running Linux or Android has vulnerabilities in both the kernel and userspace. Vulnerabilities could allow attackers to access sensitive information or implant malware. TEEs add an extra layer of security where code/data running on TEEs cannot be accessed or tampered with from Linux or Android operating systems.
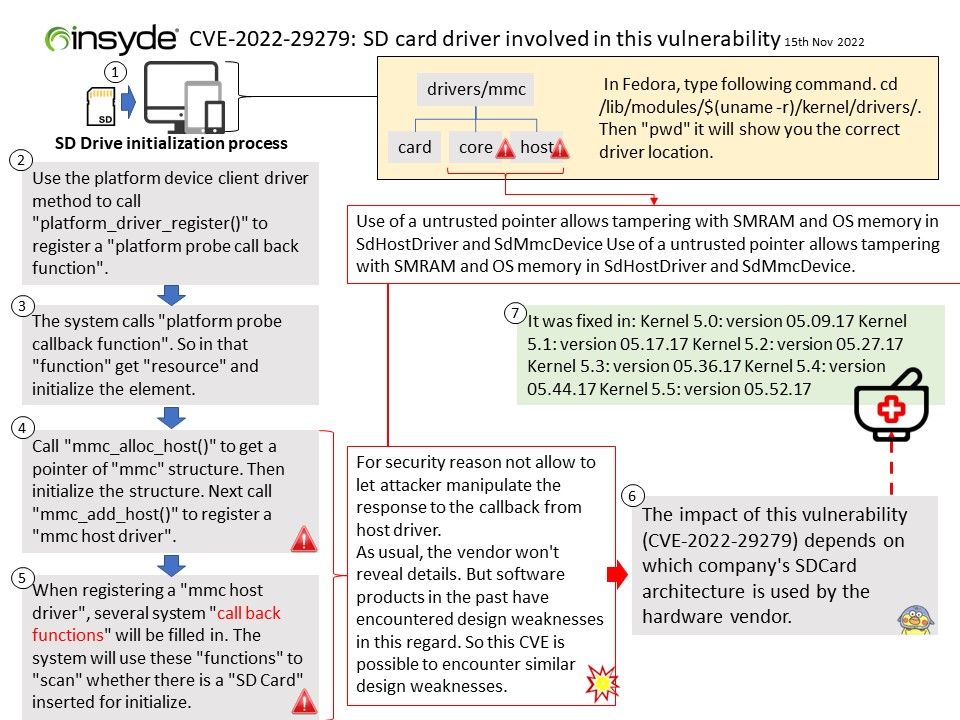
OP-TEE is designed primarily to rely on the Arm TrustZone technology as the underlying hardware isolation mechanism. However, it has been structured to be compatible with any isolation technology suitable for the TEE concept and goals, such as running as a virtual machine or on a dedicated CPU. The main design goals for OP-TEE are isolation, small footprint and portability.
Vulnerability details:
- The function
cleanup_shm_refs()is called by bothentry_invoke_command()andentry_open_session(). - The commands
OPTEE_MSG_CMD_OPEN_SESSIONandOPTEE_MSG_CMD_INVOKE_COMMANDcan be executed from the normal world via an OP-TEE SMC. - This function is not validating the
num_paramsargument, which is only limited toOPTEE_MSG_MAX_NUM_PARAMS(127) in the functionget_cmd_buffer(). - Therefore, an attacker in the normal world can craft an SMC call that will cause out-of-bounds reading in
cleanup_shm_refsand potentially freeing of fake-objects in the functionmobj_put().
Solution: fix array out of bounds check in cleanup_shm_refs(). Version 3.19.0 contains a fix for this issue. There are no known workarounds.
Official announcement: Please refer to the link for details – https://github.com/OP-TEE/optee_os/commit/728616b28df659cf0bdde6e58a471f6ef25d023c