Preface:
The cyber attack wreak havoc today. Perhaps system applications and operation system hard to avoid vulnerability occurs because of short development cycle. Crypto currency might change the financial world. However there are more and more topics are under development.
Technology background
Ethereum is an open software platform based on blockchain technology that enables developers to build and deploy decentralized applications.
What language is Ethereum written in?
There are four official reference implementations available (see below)
Golang, C++, Python and Java
The non-officially but fully working program language are Rust, Ruby, JavaScript and Solidity. However there are design limitation occurs on Golang which causes software developers decide not to use.
Why “Go” language not have been chosen by software program developers?
The question about generics in Go is years old, and has been discussed up and down and forth and back across the Go forums, newsgroups, and email lists. However Go is a language with an intentionally restricted feature set; one of the features that Go leaves out being user-defined generic types and functions.
In short, it looks that Go language lack of traditional program language flexibility. Perhaps Go (Golang) libraries work best for scientific computing. A comment consensus is that Go might evolve into the perfect high performance computing language for scientific use. And therefore programming developer prefer to make use of other programming language.
However cyber world similar a dangerous zone. The operation system, application and hardware are difficult to avoid their design weakness (vulnerabilities). The situation sounds like a cancer in Human body. The cancer evoluted by a normal human being cell.

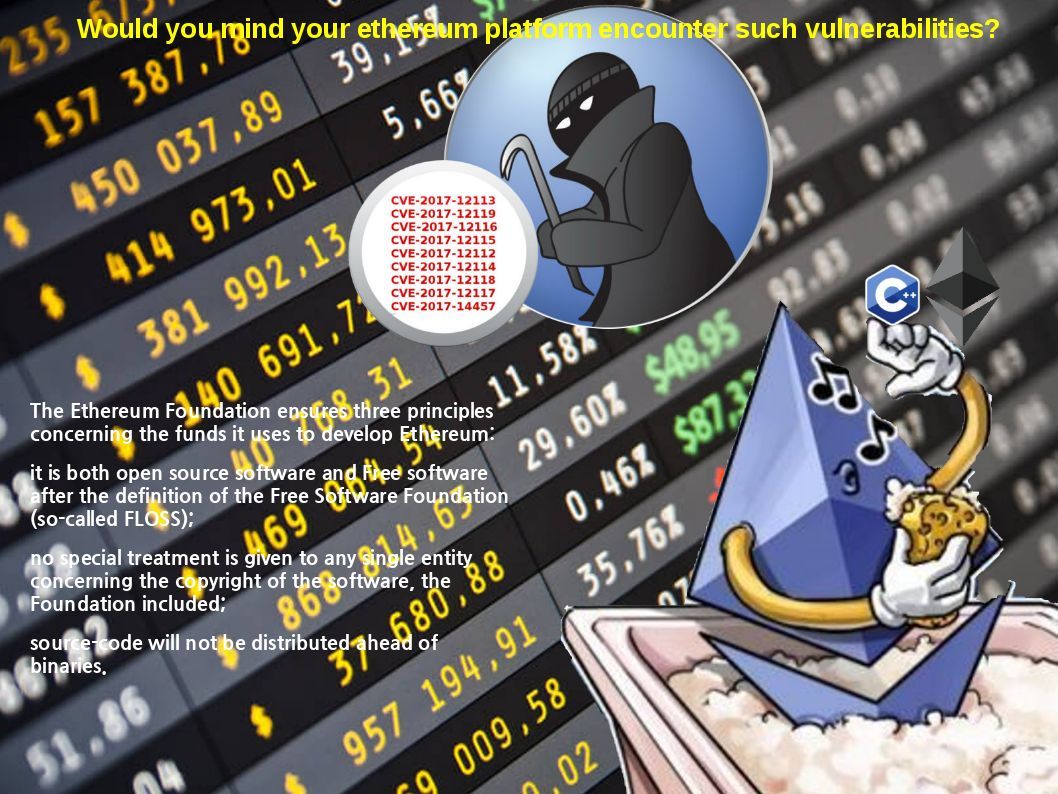
There are vulnerabilities found on cpp-ethereum last year end. A status update released on 18th Jan 2018.
Should you have interest of this topic, please find below details for reference.
An exploitable improper authorization vulnerability exists in admin_nodeInfo API of cpp-ethereum’s JSON-RPC
https://nvd.nist.gov/vuln/detail/CVE-2017-12113
An exploitable unhandled exception vulnerability exists in multiple APIs of CPP-Ethereum JSON-RPC. Specially crafted JSON requests can cause an unhandled exception resulting in denial of service.
https://nvd.nist.gov/vuln/detail/CVE-2017-12119
An exploitable improper authorization vulnerability exists in miner_setGasPrice API of cpp-ethereum’s JSON-RPC
https://nvd.nist.gov/vuln/detail/CVE-2017-12116
An exploitable improper authorization vulnerability exists in miner_setEtherbase API of cpp-ethereum’s JSON-RPC
https://nvd.nist.gov/vuln/detail/CVE-2017-12115
An exploitable improper authorization vulnerability exists in admin_addPeer API of cpp-ethereum’s JSON-RPC
https://nvd.nist.gov/vuln/detail/CVE-2017-12112
An exploitable improper authorization vulnerability exists in admin_peers API of cpp-ethereum’s JSON-RPC
https://nvd.nist.gov/vuln/detail/CVE-2017-12114
An exploitable improper authorization vulnerability exists in miner_stop API of cpp-ethereum’s JSON-RPC
https://nvd.nist.gov/vuln/detail/CVE-2017-12118
An exploitable improper authorization vulnerability exists in miner_start API of cpp-ethereum’s JSON-RPC
https://nvd.nist.gov/vuln/detail/CVE-2017-12117
An exploitable information leak/denial of service vulnerability exists in the libevm (Ethereum Virtual Machine) `create2` opcode handler of CPP-Ethereum. A specially crafted smart contract code can cause an out-of-bounds read leading to memory disclosure or denial of service.
https://nvd.nist.gov/vuln/detail/CVE-2017-14457
Summary:
There were 40,135 transactions on Ethereum blockchain on 5/17/2017. On January 25, 2018 Ethereum now is a bit over $1050. Perhaps of the crypto currency value it will lure the interest of the hacker. As usual another vulnerabilities or zero day cyber attacks might happen later on. So make sure that you have remediation and mitigation procedure if your Ethereum back-end is develop by C++.