Preface:
Java, NodeJS, Python, ObjC with Xcode and GO are the popular programming language for develop of e-wallet application. It looks that some of the programmer favor of Java language since it is a common programming language.
New technology, but targeting approach by hacker remain unchanged
Reporting of Cybersecurity Incidents – InfoSec Resources
Jul 2017 – Hacker stole ether equivalent US$31 million. A design weakness found in multi-sig wallet, it allow method called initWallet() in share wallet library. As a result such action reinitialized the contract by delegating through the library method, overwriting the owners on the original contract. The attacker will become the owners.
* Ethereum wallet is implemented in C++ programming language
Nov 2017 – Parity wallet vulnerability freezes US$278 million of ethereum. The company patched the bug encountered on July 2017. However the code still present bugs and therefore freeze the crypto currency in the wallet.
* Ethereum wallet is implemented in C++ programming language
Feb 2012 – exposes a PIN vulnerability in Google Wallet security.
* For native android application it is using a Java programming language.
Observation: It looks that even though your e-wallet contains facial recognition for authentication. However the historical records shown that the vulnerabilities discovered in past are causes by programming mistake.
Common Security Vulnerabilities in a Digital Wallet
- The registration process does not identify fraud verification of the user’s information card information.
- Develop programming language encountered design limitation (vulnerability).
* For native android application it is using a Java programming language.
Observation: It looks that even though your e-wallet contains facial recognition for authentication. However the historical records shown that the vulnerabilities discovered in past are causes by programming mistake.
How is e-wallet different from cryptocurrency wallet on cyber security viewpoint?
Bitcoin is a cyrptocurrency. You need a wallet to keep your bitcoins. But Bitcoin underlying technology is block chain which cannot be counterfeited. If ever there is an issue with a transfer of funds, Bitcoin protocol settles it through consensus.
The e-wallet currency is traditional currency.It uses the secure 256–bit Advanced Encryption Standard (AES) for encrypting information in your wallet. If a hacker tries a brute force attack relies on computer enter possible random-number strings at top speed it would take more than a billion years to exhaust all the possibilities.
Observation: It looks that both type of wallet contained hack proofed feature. But is there any underlying reason make those wallet in risk?
The Java, NodeJS, Python, ObjC with Xcode and GO are the main trend of the programming language today. Why does application developer like Java? Java is a platform Independent. Means Java does not depend on hardware and OS. Java platform fully compatible with all computers. Even through it is a mainframe computer. However the cyber security incidents from past awake the IT world that even though you are using block-chain technology platform. The other side of end point might encounter cyber attack which causes data breach or compromised of both machines. From security point of view, the overall risk rating for e-business applications including cryptocurrency or traditional currency payment transfer system are equal.
Traditional way bring people consider endpoint security but ignore other possibilities factors which are in risk!
About programming language
Python
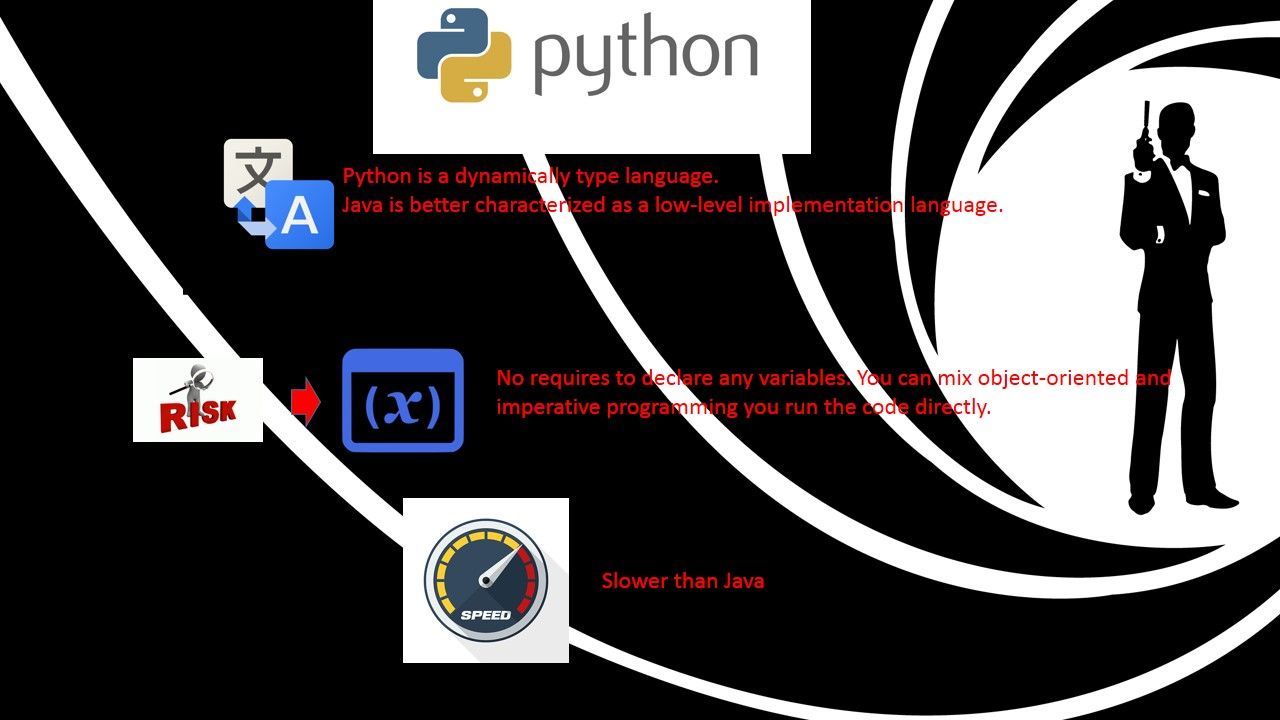
Language: Python is a dynamically type language. Java is better characterized as a low-level implementation language.
Use of VARIABLE: No requires to declare any variables. You can mix object-oriented and imperative programming you run the code directly.
Run time speed: Slower than Java
Java
Language: Java is a statically typed language. Python is much better suited as a “glue” language.
Use of Variable: Requires to define the type of each variable, it’s object oriented in the sense that you cannot write any code without defining a class, you also invoke a compiler to compiler the code then you can run it.
Runtime speed: Run faster than python

Node.js
Language: Node.js is not a programming language. The programming language is Javascript. But Node.js not similar JavaScript framework. A group of authors define a new frameworks specifically for Node.js, It includes Express.js, Restify.js, and Hapi.js.
Use of Variable: When you declare methods without using var (function <function_name>() {}), those function declarations are moved to the top of the local scope. If you manually declare you functions, you have to wait until they are both declared before you can use them.
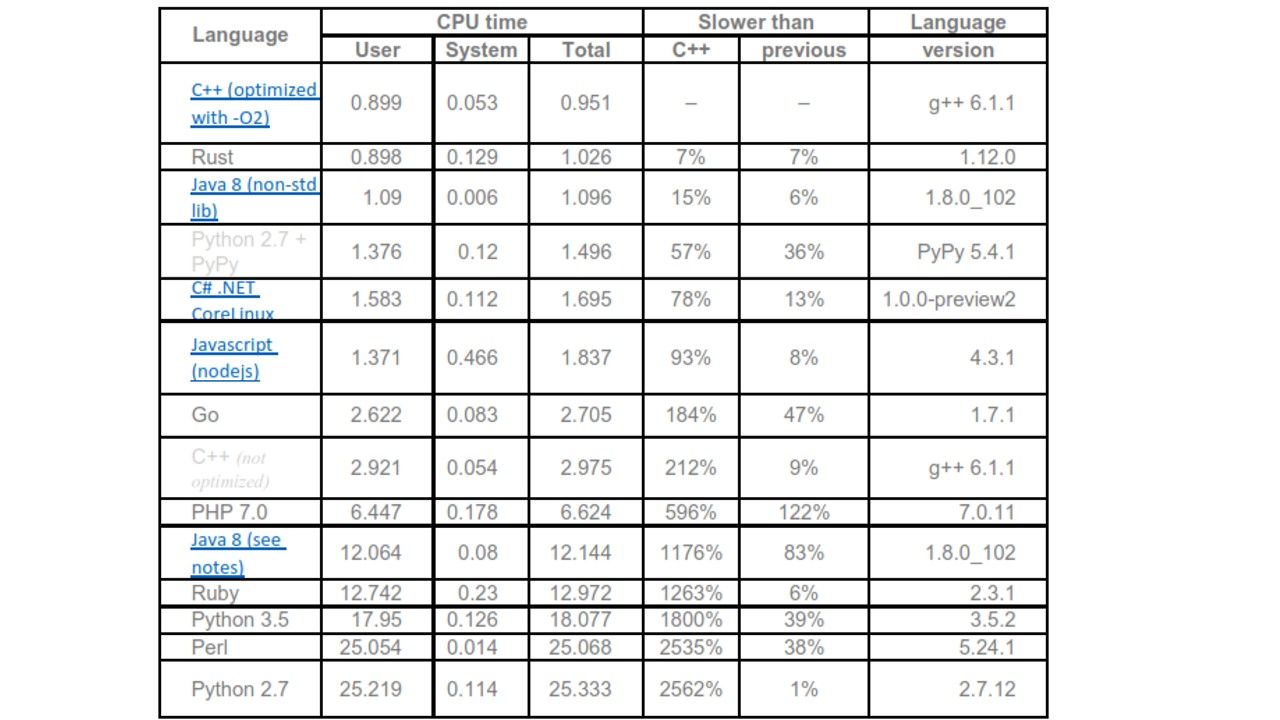
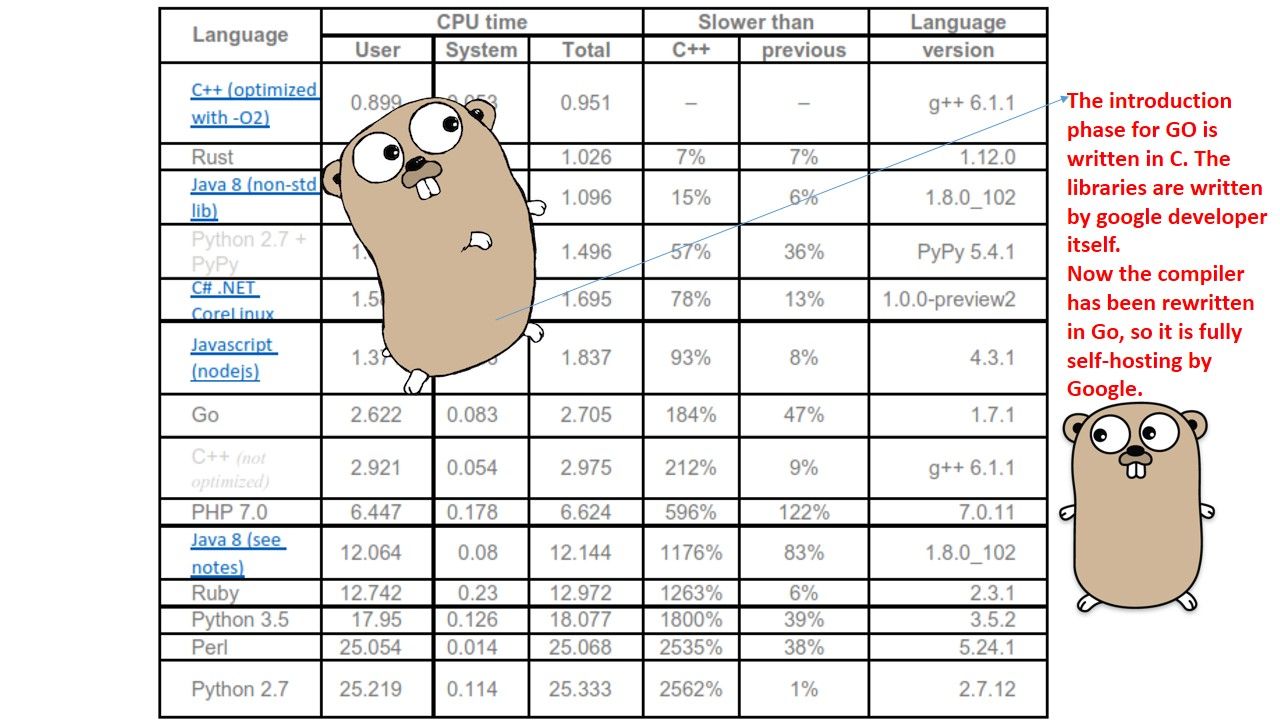
Runtime speed: Refer to benchmark table

C++ vs. Python vs. PHP vs. Java vs. Others performance benchmark (2016 Q3)
GO
Language: Go is an open source programming language designed for building simple, fast, and reliable software. The introduction phase for GO is written in C. The libraries are written by google developer itself. Now the compiler has been rewritten in Go, so it is fully self-hosting by Google.
Variable: The type of variable is automatically judged by the compiler based on the value passed to it.
Runtime speed: Refer to below benchmark table
ObjC with Xcode
Language: Xcode supports C, C++, Objective-C, Objective-C++, Java, AppleScript, Python, Ruby, Rez, and Swift source code with a variety of programming models, including but not limited to Cocoa, Carbon, and Java.
Variable: It is important to note that ObjC does not support class variables. But developer can simulate static variables
Runtime speed: Objective-C is slightly slower than straight C function calls because of the lookups involved in its dynamic nature.

Security Focus
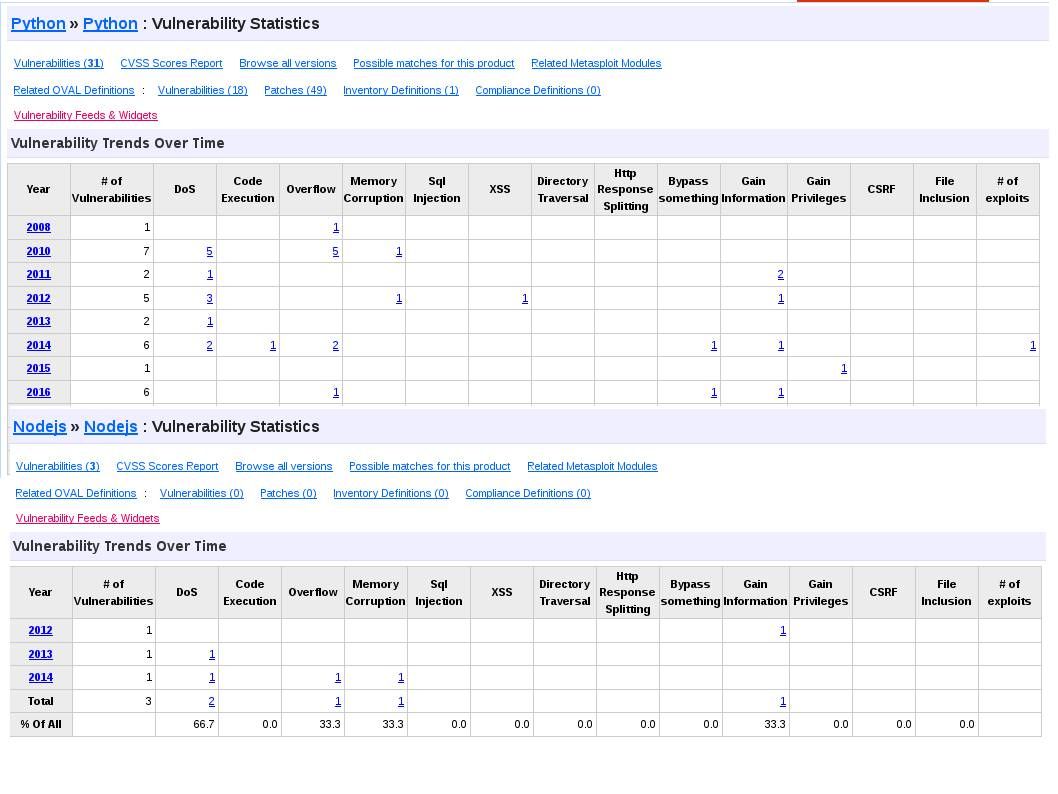
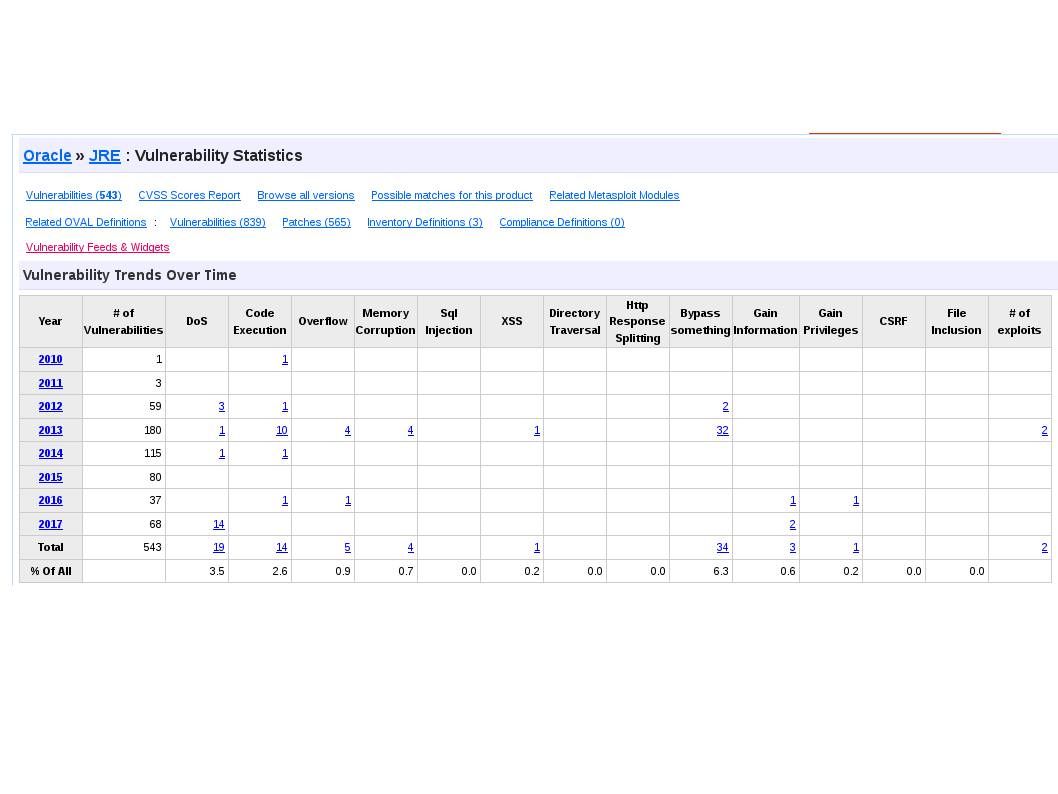
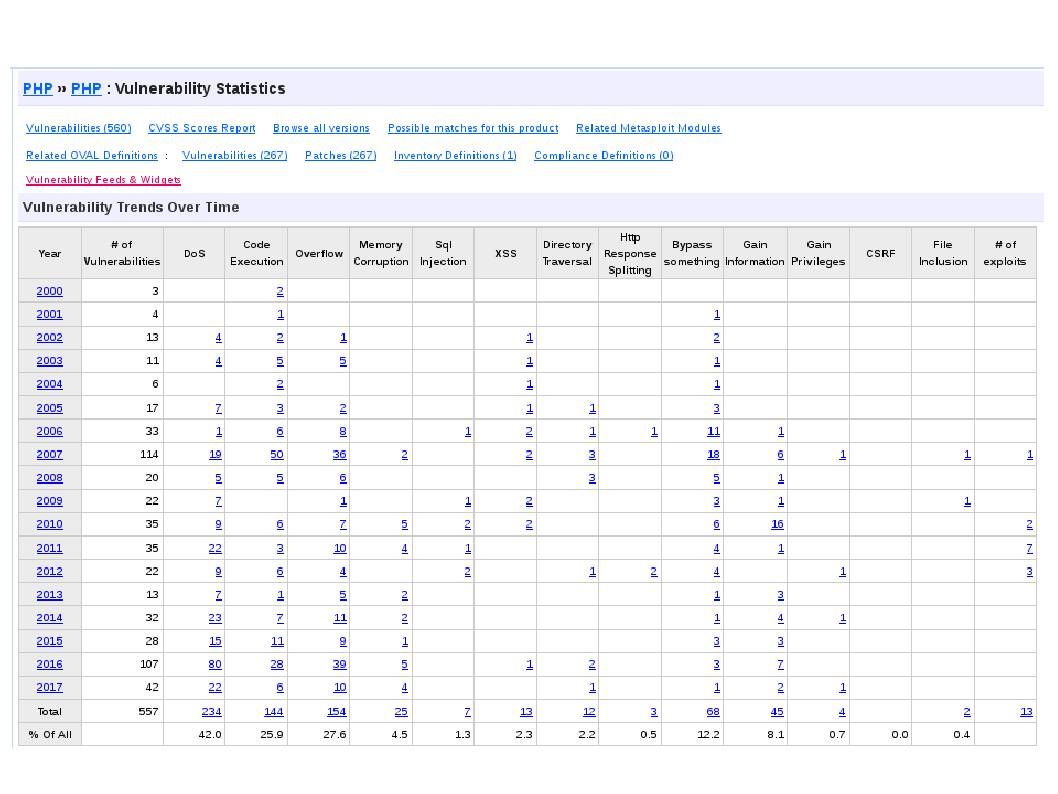
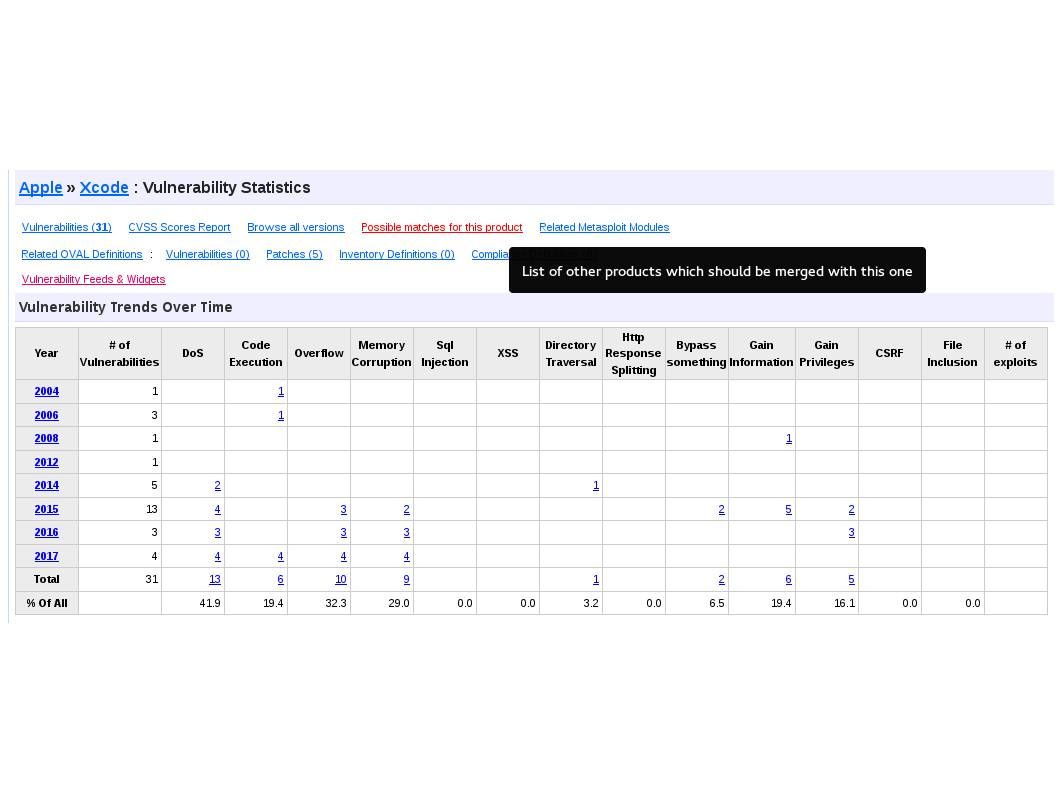
Since no bug proof software or hardware in the world and therefore the practical operation expose the design weakness (vulnerability). Refer to informative diagram table below , Java and php looks unsecure because of the accumulate vulnerability records.
But why Java and PHP programming language are popular in the IT world. Even though Node.js framework make use of Java language. I believe that it is the fate of the IT product market. Perhaps Java bring security worries to the world. However java language provide a comprehensive functions. E-wallet looks has benefits running on Apple iPhone OS. Since it is a proprietary environment. From security prospective, it is better than opensource OS since it looks a black hole. Perhaps vulnerability occurs, the vendor (Apple) will conduct the remediation immediately. As mentioned iOS is a proprietary environment and such away avoid multiple vulnerabilities occurs simultaneously.
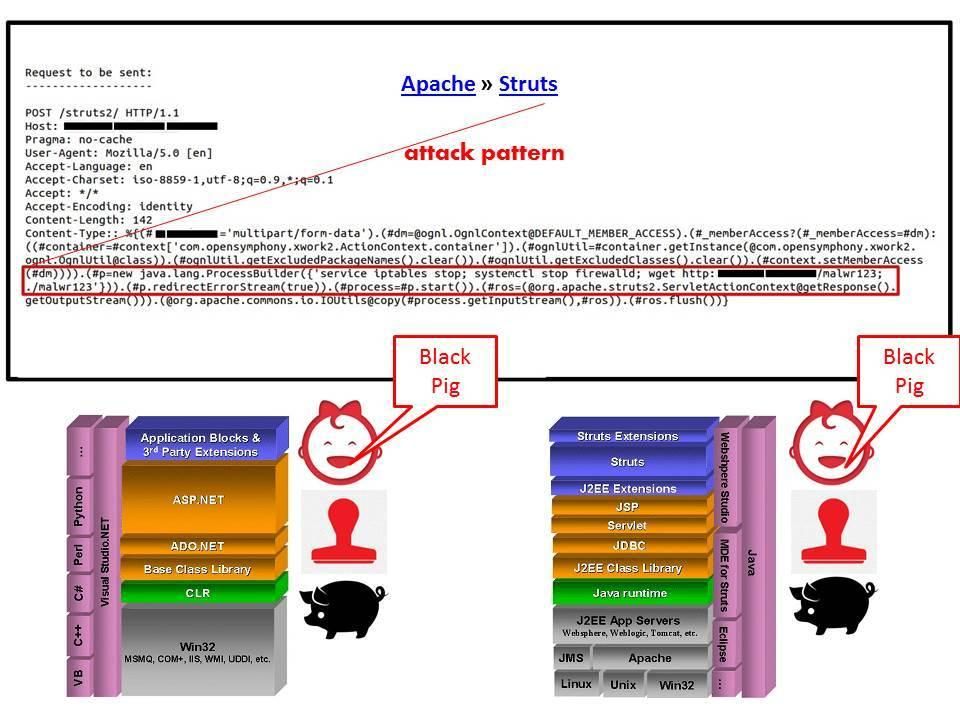
Example of multiple vulnerabilities: For instance Multiple Vulnerabilities in Apache Struts 2 Affecting Cisco Products (September 2017). On September 5, 2017, the Apache Software Foundation released security bulletins that disclosed three vulnerabilities in the Apache Struts 2 package. However those vulnerability affected a series of Cisco products since those voice and media management products deployed Apache Structs 2.
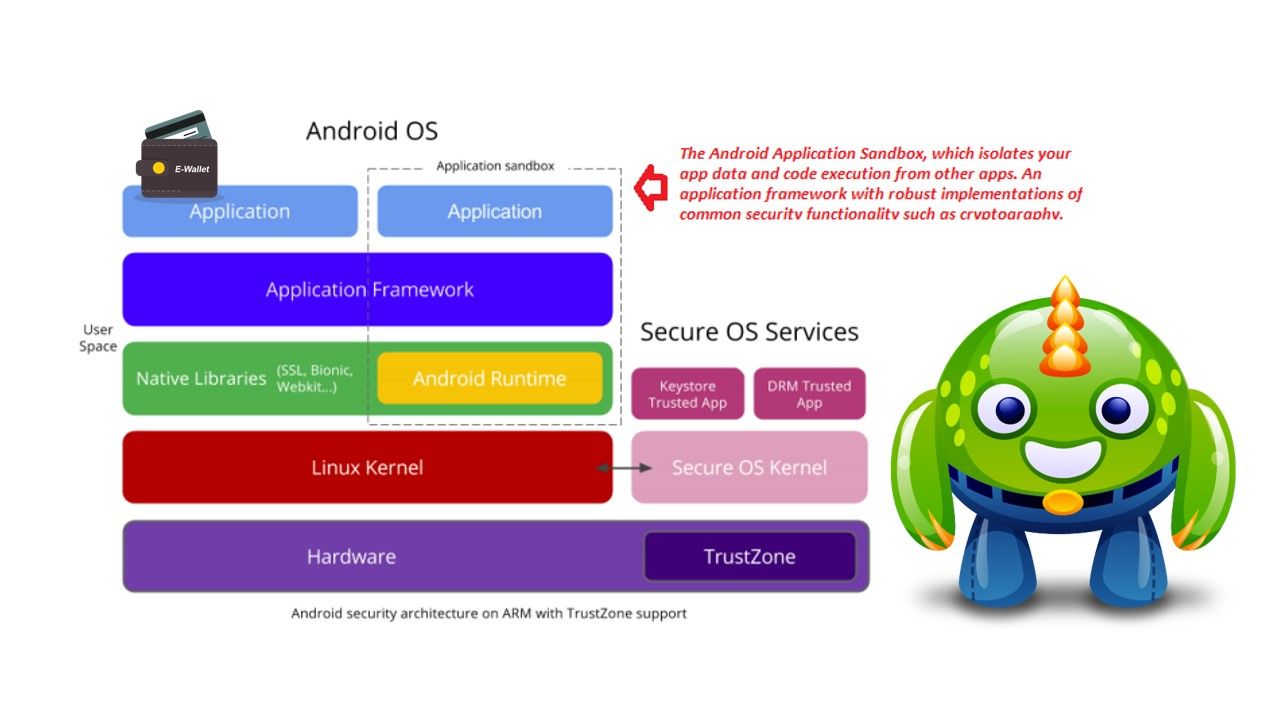
E-Wallet on top of mobile device platform
The Near Field Communication (NFC) payment wallets designed by GSMA program project. It relies on SIM based technique support the payment service in past. But Android M break the ice develop other alternative for online payment electronic wallet. From security point of view, the new android system architecture of the design provide sandbox feature enhance the security (see below). If we believe that it is a trustworthy environment then we move our security concerns to e-wallet SDK.
Most likely the technology trend will be form into two different way. The retail shop remain to use near field communication technique secure the payment transaction. For online payment transaction like Master card, Paypal and Alipay will lead the online payment solution. As mentioned the vulnerability found in online e-wallet SDK more or less will involved in programming language. For more details, please see below:
Instance 1: A cross-site scripting (XSS) vulnerability in GetAuthDetails.html.php in PayPal PHP Merchant SDK (aka merchant-sdk-php) 3.9.1 allows remote attackers to inject arbitrary web script or HTML via the token parameter (CVE-2017-6099).
Instance 2: The Android source code file (internal/telephony/SMSDispatcher.java) does not properly construct warnings about premium SMS messages, which allows attackers to spoof the premium-payment confirmation dialog via a crafted application, aka internal bug 28557603 (CVE-2016-3883)
Reference: Telephony in Android 4.x before 4.4.4, 5.0.x before 5.0.2, 5.1.x before 5.1.1, 6.x before 2016-09-01, and 7.0 before 2016-09-01
Instance 3: Inappropriate implementation of the web payments API on blob: and data: schemes in Web Payments in Google Chrome prior to 60.0.3112.78 for Mac, Windows, Linux, and Android allowed a remote attacker to spoof the contents of the Omnibox via a crafted HTML page (CVE-2017-5110).
Instance 4: Hacker stole ether equivalent US$31 million. A design weakness found in multi-sig wallet, it allow method called initWallet() in share wallet library. As a result such action reinitialized the contract by delegating through the library method, overwriting the owners on the original contract. The attacker will become the owners.
* Ethereum wallet is implemented in C++ programming language
Refer to above details, the argument can confirm that programming language is the important factor in e-wallet development. Even through it is a cryptocurrency wallet. The overall security level of protection for a eletronic payment system must include programming language as a major factor.
End of discussion……!
Information Supplement (under observation)
Typically, a program consists of instructions tell the computer what to do. Thus what types of data will be used when it is running will be responsible by variable. In the Java programming language, the words field and variable are both one and the same thing. Variables are devices that are used to store data, such as a number, or a string of character data. The enumerate() is one of the built-in Python functions. It returns an enumerate object. In our case that object is a list of tuples (immutable lists), each containing a pair of count/index and value. However variable can be rebound at any time, so no consistent use as an enumerator. This is a vulnerability encountered in python.
* An enumeration is a set of symbolic names (members) bound to unique, constant values.
But comparing with Java and Python CVE checklist. It shown that Python programming language hit vulnerability less than Java programming language .