Preface: Sandbox evasion techniques. Common evasion techniques include the use of specific assembly instructions, and looking for specific registry keys or file names.
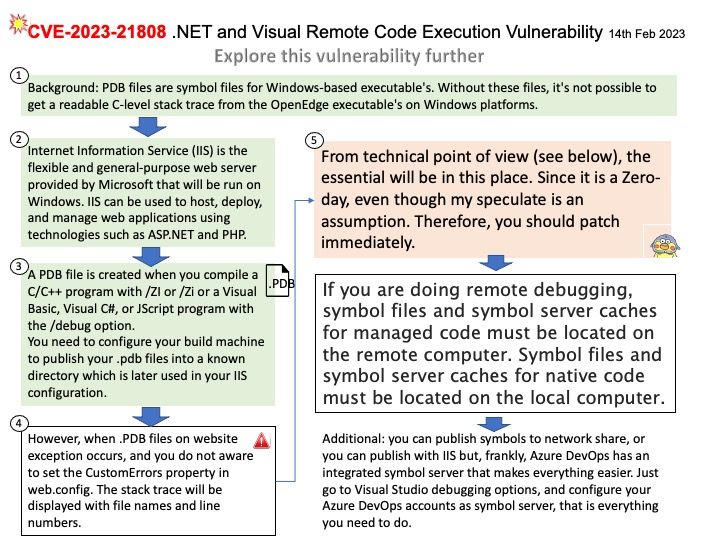
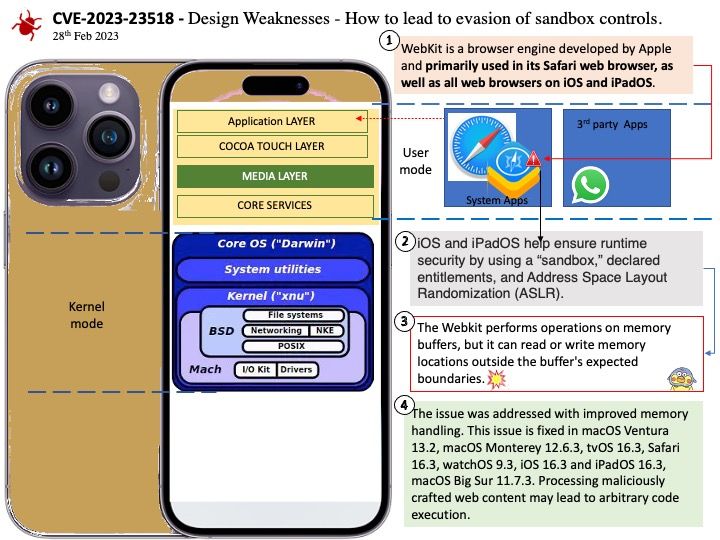
Background: iOS and iPadOS help ensure runtime security by using a “sandbox,” declared entitlements, and Address Space Layout Randomization (ASLR).
All third-party apps are “sandboxed,” so they are restricted from accessing files stored by other apps or from making changes to the device. Sandboxing is designed to prevent apps from gathering or modifying information stored by other apps. Each app has a unique home directory for its files, which is randomly assigned when the app is installed. If a third-party app needs to access information other than its own, it does so only by using services explicitly provided by iOS and iPadOS.
System files and resources are also shielded from the users’ apps. Most iOS and iPadOS system files and resources run as the nonprivileged user “mobile,” as do all third-party apps. The entire operating system partition is mounted as read-only. Unnecessary tools, such as remote login services, aren’t included in the system software, and APIs don’t allow apps to escalate their own privileges to modify other apps or iOS and iPadOS.
Vulnerability details: The issue was addressed with improved memory handling. This issue is fixed in macOS Ventura 13.2, macOS Monterey 12.6.3, tvOS 16.3, Safari 16.3, watchOS 9.3, iOS 16.3 and iPadOS 16.3, macOS Big Sur 11.7.3. Processing maliciously crafted web content may lead to arbitrary code execution.
Official announcement: For details, please refer to the url for reference – https://support.apple.com/en-us/HT213605