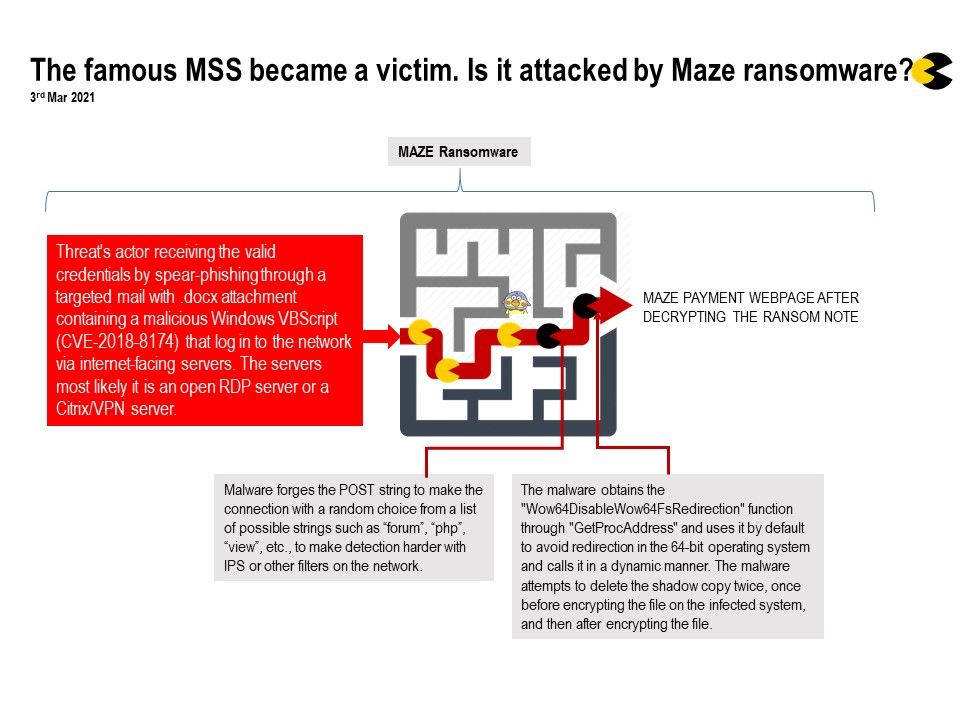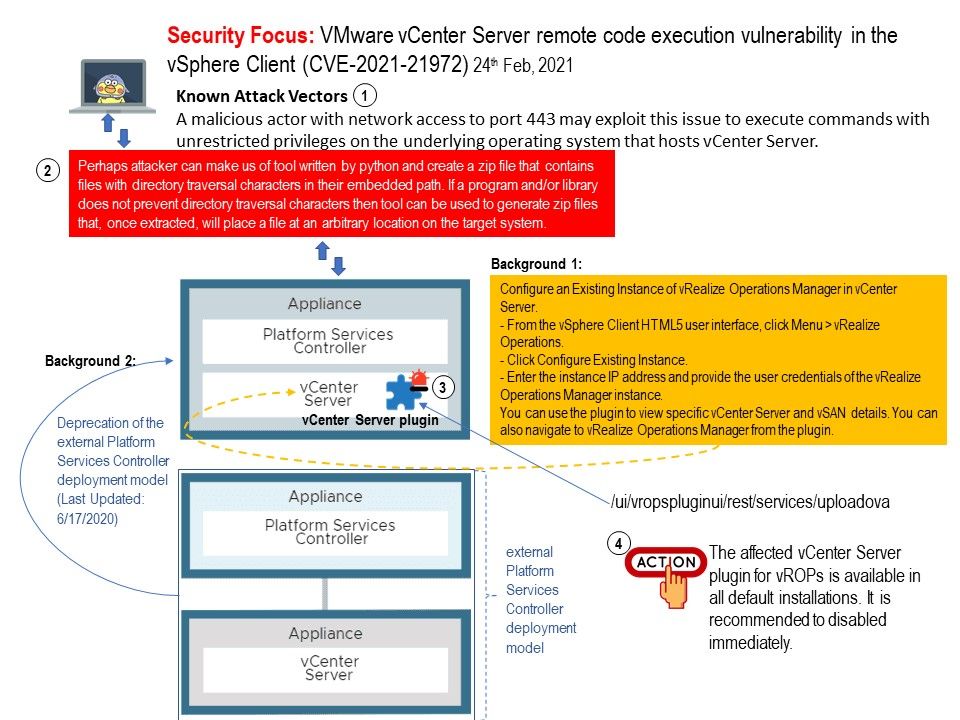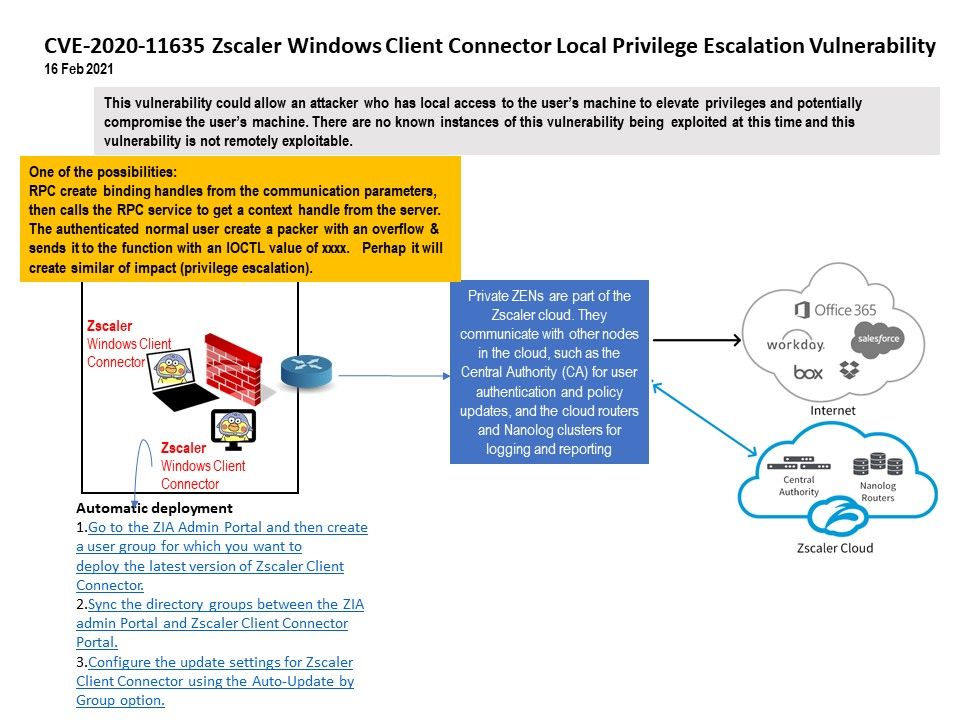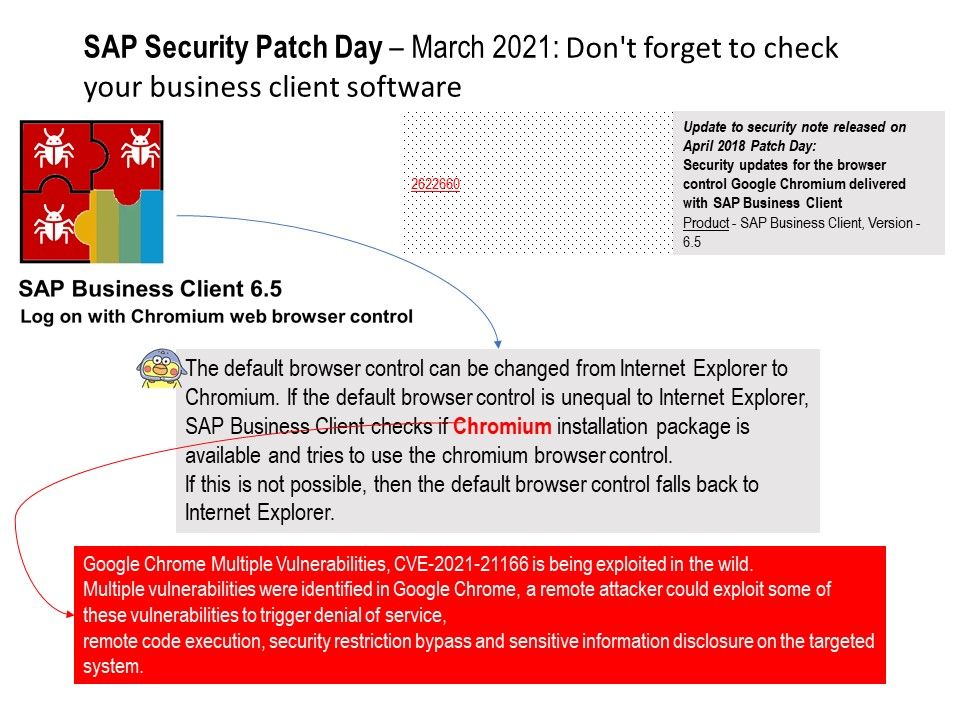
Preface: In SAP Business Client history, rare to offer a Chromium web browser control based on CefSharp (CEF – Open Source Version of Google Chrome) as an alternative rendering engine to Microsoft IE. In 2018, the dream come true happened.
SAP business clinet software technical background: If local client web browser not work, SAP client software will enforce the default browser control falls back to Internet Explorer. Unfortunately, Chrome Vulnerability is being exploited in the wild. According to CVE-2021-2116, a remote attacker could exploit some of these vulnerabilities to trigger denial of service, remote code execution, security restriction bypass and sensitive information disclosure on the targeted system.
Reference: When Chrome OS is vulnerable to malicious extensions by bad 3rd party apps programming. It can also put your system at risk if you choose to run an extension “unsandboxed.”
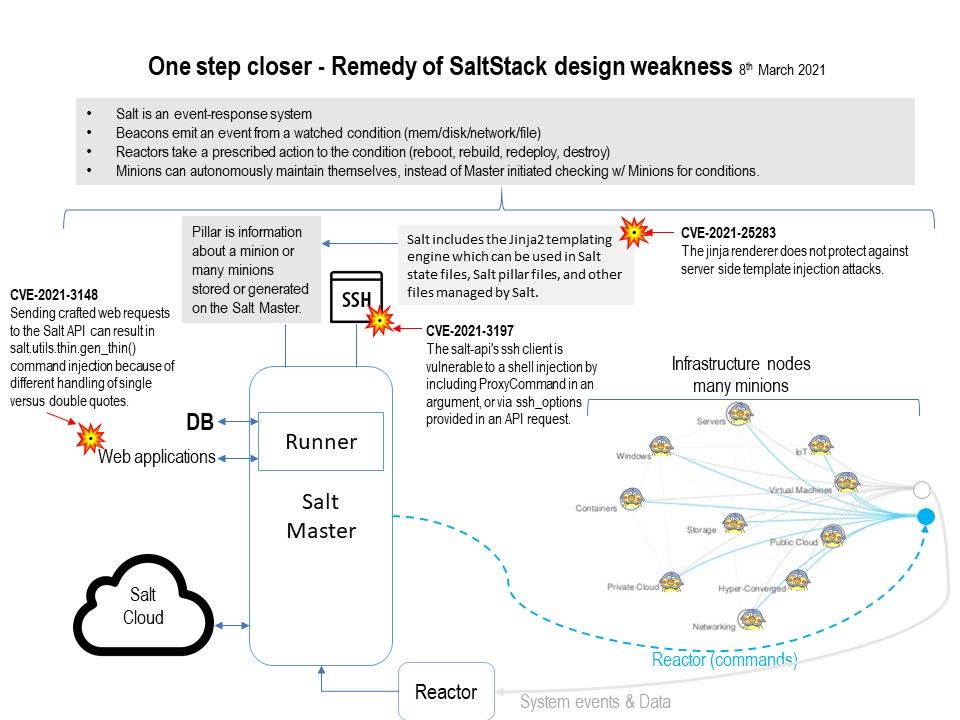
Official announcement : (SAP Security Patch Day – March 2021) – please refer to the link – https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=571343107

.jpg?width=1920&height=1080&fit=bounds)