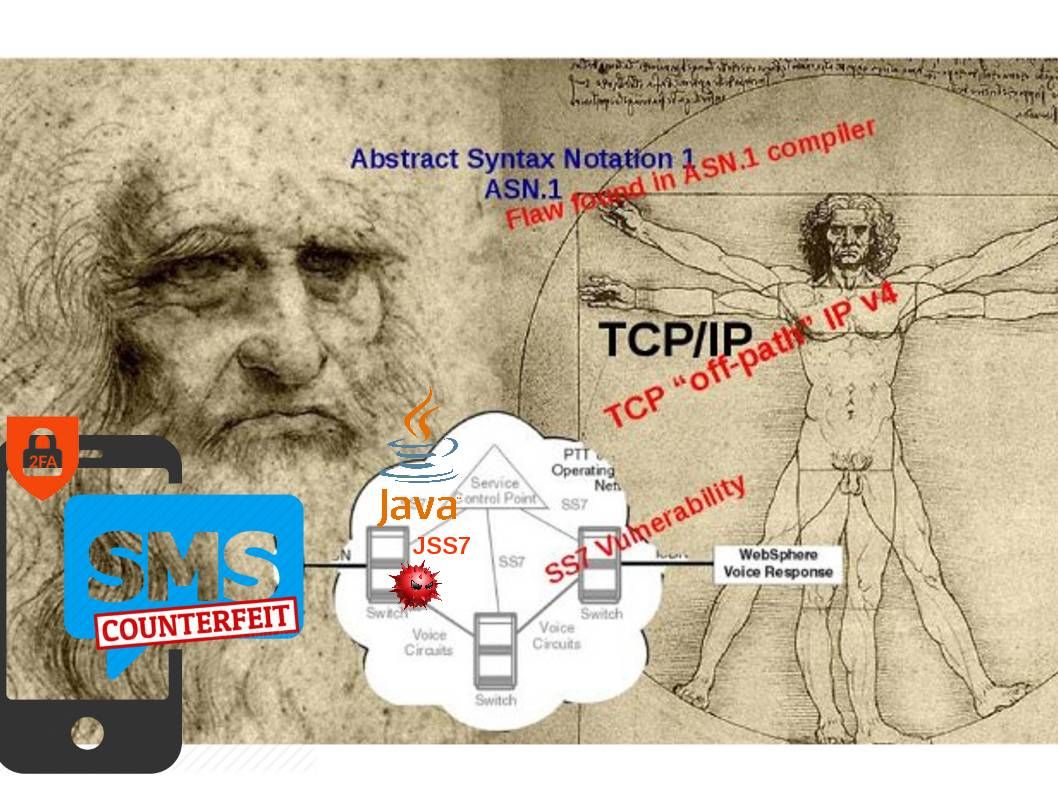
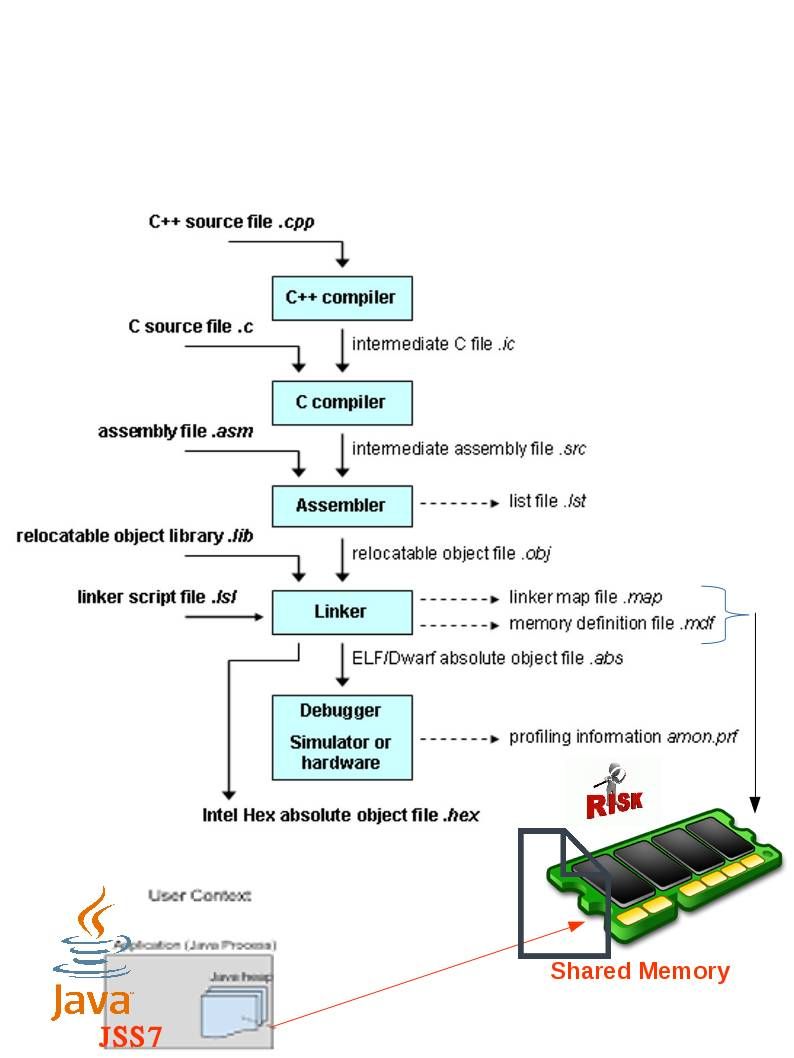
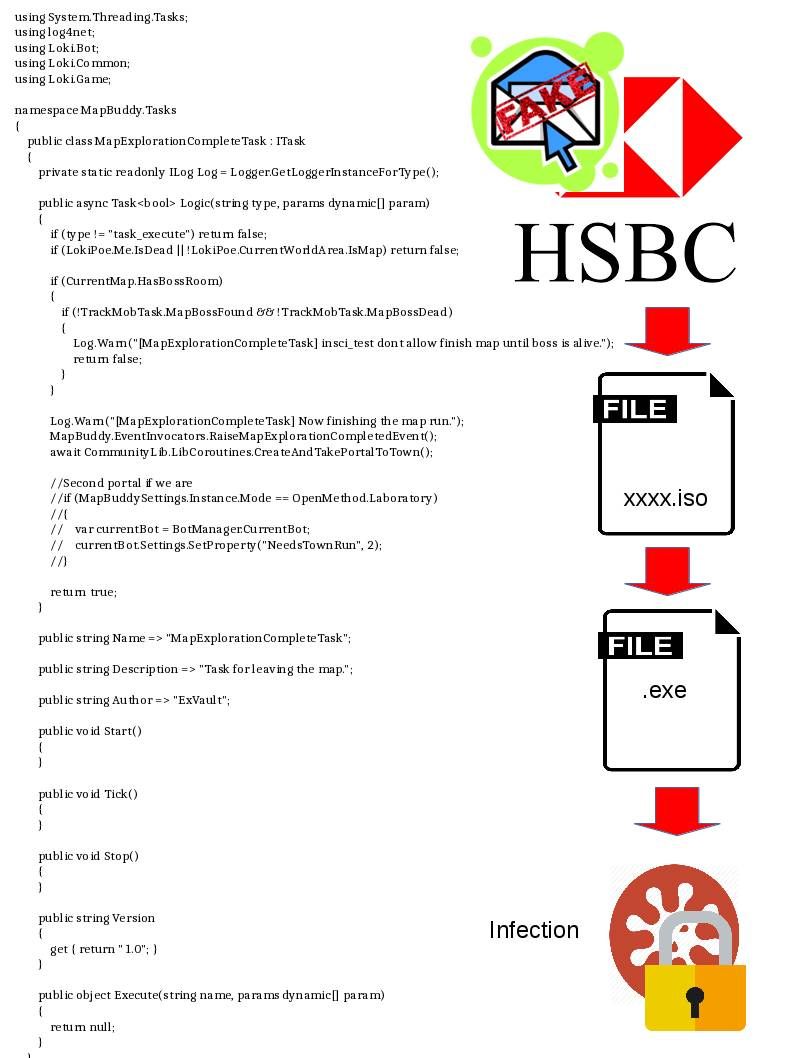
Preface:
Bitcoin mining make the world crazy. Java base coin mining tools provides flexibility. A lightweight, small footprint let you involved to mining industry.
What is the actual reason to lure the people starting the mining work?
Reminder: Bitcoin mining like a games. Different types of crypto currencies will have different mining rewards policy.
It looks that it is easy to answer. We are looking for money that is the reward.
The Bitcoin block mining reward halves every 210,000 blocks, the coin reward will decrease from 12.5 to 6.25 coins, said bitcoinblockhalf (www.bitcoinblockhalf.com)
So what is the target mining pool (blockchain) and coin types?
The hottest crypto currencies are Bitcoin (BTC), Ethereum (ETH), Monero (XMR), Litecoin (LTC), Dash and Pascal (PASC). But Ethereum mining is profitable, but it cannot maintain in the long run. However it is still the hottest topic. Ethereum has seen an almost 20x jump in price in 2017. What are Mining Rewards in Ethereum?
The proof of work(PoW) in Ethereum is run through Ethash. The successful PoW miner will receive a static block reward that is equal to 5 Ether.
Why a GPU mines faster than a CPU?
A majority of GPUs support add, multiply and multiply-add natively in hardware with single-cycle throughput, as the basic computation instructions. And thereby it is better to using GPU conduct bitcoin mining. Since traditional CPU embedded instruction set and OS footprint. It is difficult to maximize the overall performance for bitcoin mining.
Does Java code is the best suit for Bitcoin Mining?
I watch a TV program years ago, a crew visited China report the status of this industry. Shown on the TV screen the bitcoin miner campus like a factory. A whole bunch of computer units which generates high temperature. You could not found a pretty office lady in that office. So, does it a artificial intelligence office? Seems it is not, you will find young Chinese men which wearing casual to working over there.
The traditional bitcoin mining require high CPU resources to do the calculation. A hints of the mining requirement recommend using GPU (graphics processing unit) instead of CPU (central processing unit). However, an HTML IFRAME tag is able to embedded java script to share visitor CPU resources to assists for bitcoin mining ((Embedding a javascript inside another using the<iframe> tag). As we know, web site open to the world not limited to area and visitor. From technical point of view, this is a win win situation. Coinhive offers a JavaScript miner for the Monero Blockchain that you can embed in your website.
To be honest, java programming provides flexibility for bitcoin miner do the mining. Below sample shown that a light-weight java programming can conduct a mining focusing on Ethereum blockchain. Some largeBitcoin mining farms switch to Ethereum today.
Remark: Ethereum is an open-source, public, blockchain-based distributed computing platform featuring smart contract functionality
package org.ethereum.core;
import java.math.BigInteger;
import org.ethereum.crypto.HashUtil;
import org.ethereum.util.ByteUtil;
import org.ethereum.util.FastByteComparisons;
import org.spongycastle.util.Arrays;
import org.spongycastle.util.BigIntegers;
public class Miner {
public boolean mine(Block newBlock, byte[] difficulty) {
BigInteger max = BigInteger.valueOf(2).pow(256);
byte[] target = BigIntegers.asUnsignedByteArray(32,
max.divide(new BigInteger(1, difficulty)));
byte[] hash = HashUtil.sha3(newBlock.getEncodedWithoutNonce());
byte[] testNonce = new byte[32];
byte[] concat;
while(ByteUtil.increment(testNonce)) {
concat = Arrays.concatenate(hash, testNonce);
byte[] result = HashUtil.sha3(concat);
if(FastByteComparisons.compareTo(result, 0, 32, target, 0, 32) < 0) {
newBlock.setNonce(testNonce);
// System.out.println(Hex.toHexString(newBlock.getEncoded()));
return true;
}
}
return false; // couldn't find a valid nonce
}
}
Cyber security view point
Researchers found that a sophisticated class of surreptitious mining software might penetrates your system. Hacker will delivered their services through infected image files or by clicking on links leading to a malicious site. n such a way that visitor will consume more CPU power. It is easy to figure it out what is the status of your personal computer at home. If you have everything closed but CPU usage is still super high, then you may have a crypto mining malware problem.
Potential opportunities for hacker
Since those bitcoin mining java script not going to compile, Those programming coding something do not trigger the security alarm. Hacker is easy to mix their malware code contained in bitcoin mining java script then bypass the detective mechanism.
What next?
Perhaps Bitcoin environment looks like a new generation of new century. It is hard to draw into conclusion at this moment. Perhaps Bitcoin environment looks like a new generation of new century. It is hard to draw into conclusion at this moment. The similar case of traditional bank robbery will be replaced by new technology. The hacker will conduct similar criteria of criminal activities.

Reference:
Monero: Mining metrics are calculated based on a network hash rate of 252 MH/s and using a XMR – USD exchange rate of 1 XMR = $ 88.35. These figures vary based on the total network hash rate and on the XMR to USD conversion rate. Block reward is fixed at 6.022756660193 XMRand future block reward reductions are not taken into account. The average block time used in the calculation is 120 seconds. The electricity price used in generating these metrics is $ 0.12 per kWh.
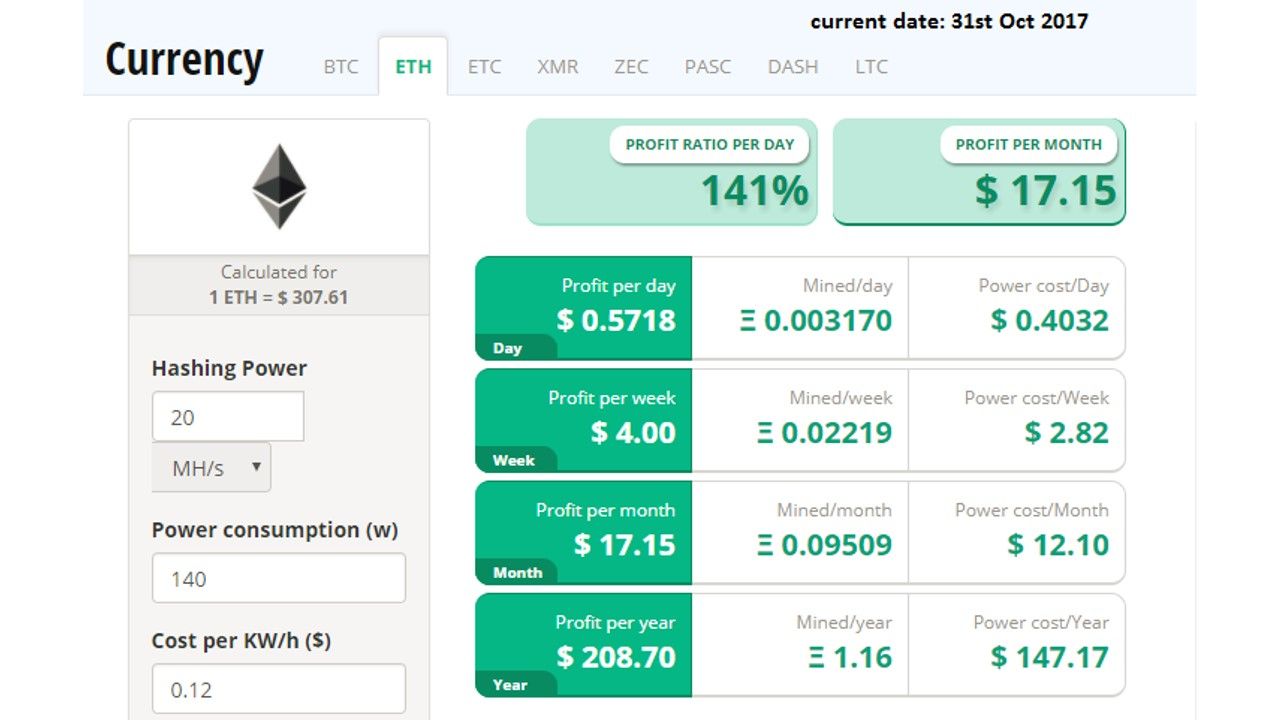
Ethereum: Mining metrics are calculated based on a network hash rate of 109,037 GH/s and using a ETH – USD exchange rate of 1 ETH = $ 307.61. These figures vary based on the total network hash rate and on the ETH to USD conversion rate. Block reward is fixed at 3 ETH and future block reward reductions are not taken into account. The average block time used in the calculation is 15 seconds. The electricity price used in generating these metrics is $ 0.12 per kWh.
Bitcoin: Mining metrics are calculated based on a network hash rate of 10,399,990,921 GH/s and using a BTC – USD exchange rate of 1 BTC = $ 6138.57. These figures vary based on the total network hash rate and on the BTC to USD conversion rate. Block reward is fixed at 12.5 BTCand future block reward reductions are not taken into account. The average block time used in the calculation is 600 seconds. The electricity price used in generating these metrics is $ 0.12 per kWh.
DASH: Mining metrics are calculated based on a network hash rate of 210,374 GH/s and using a DASH – USD exchange rate of 1 DASH = $ 283.43. These figures vary based on the total network hash rate and on the DASH to USD conversion rate. Block reward is fixed at1.801475954707712 DASH POW mining out of 3.602951909415424 DASH total mining reward and future block reward reductions are not taken into account. The average block time used in the calculation is 488 seconds. The electricity price used in generating these metrics is $ 0.12per kWh.
Litecoin: Mining metrics are calculated based on a network hash rate of 30,369 GH/s and using a LTC – USD exchange rate of 1 LTC = $ 56.5. These figures vary based on the total network hash rate and on the LTC to USD conversion rate. Block reward is fixed at 25 LTC and future block reward reductions are not taken into account. The average block time used in the calculation is 150 seconds. The electricity price used in generating these metrics is $ 0.12 per kWh.