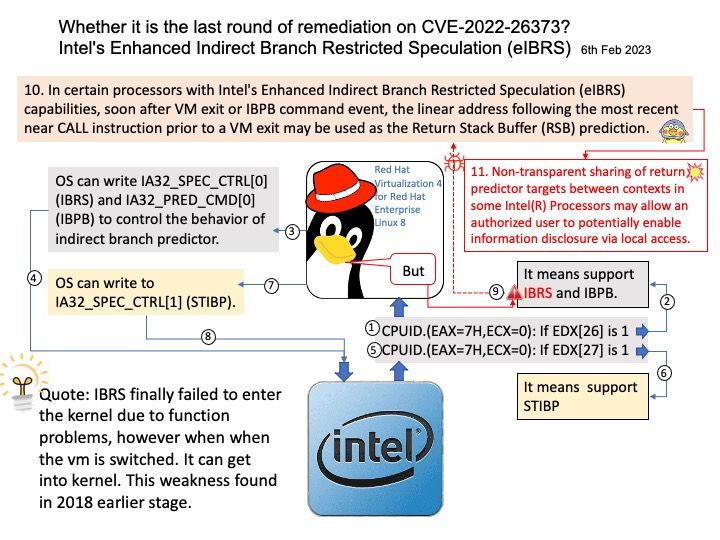
Preface: CVE-2022-26373 technical detail has released to public on 9th Aug 2022. Till end of Jan, 2023 it still has update on this vulnerability. For example, Red Hat fixed this vulnerability in their product Enterprise Linux 7 on 3rd Nov 2022. Since then it conducting the remediation to their product line. Perhaps the remediation on 24th Jan 2023 to Red Hat Virtualisation 4 for Red Hat Enterprise Linux 8 is the final round.
Looks like this is a CPU vendor specific bug. As a result, some vendors have stated that their products are not affected by this vulnerability. Whether it a absolute answer? All will depends on the use of CPU processor brand.
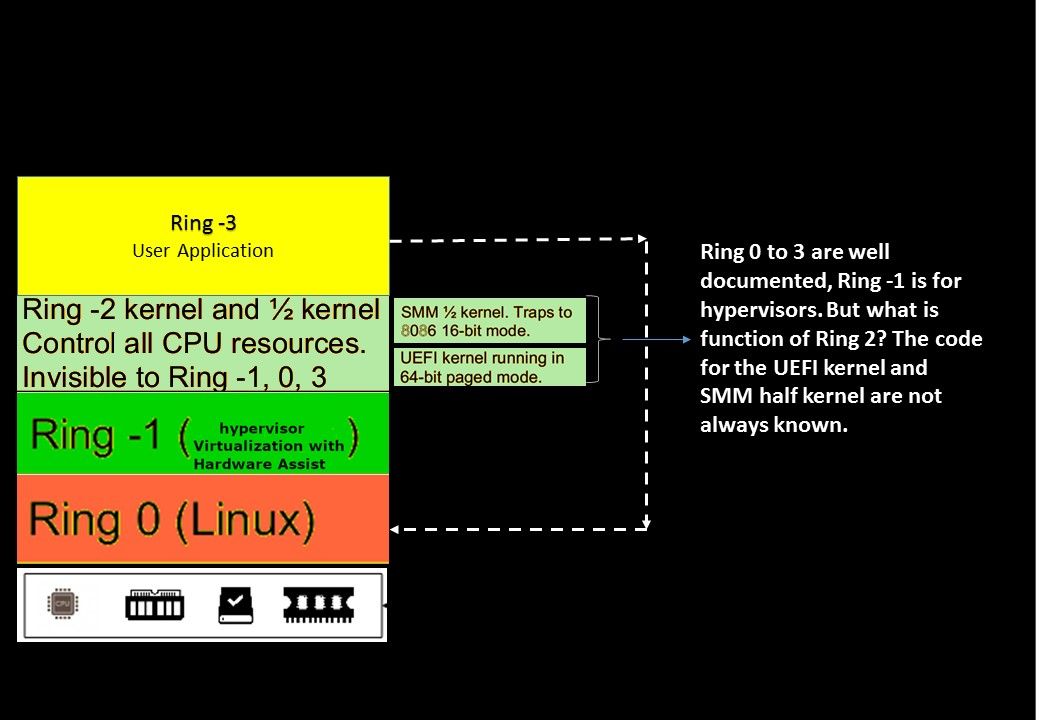
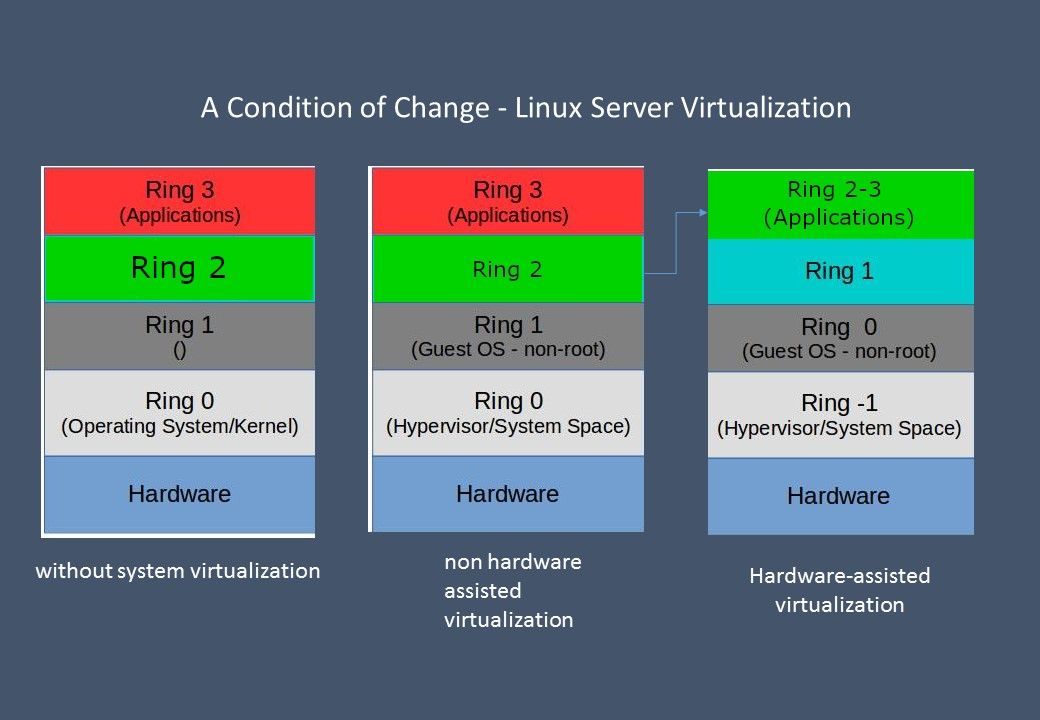
Background: From technical point of view, Indirect Branch Restricted Speculation (IBRS) is an indirect branch control mechanism that restricts speculation of indirect branches. See below for technical details.
CPUID.(EAX=7H,ECX=0): If EDX[26] is 1, it means support IBRS and IBPB,
OS can write IA32_SPEC_CTRL0 and IA32_PRED_CMD0 to control the behavior of indirect branch predictor.
IBRS finally failed to enter the kernel due to function problems, however when when the vm is switched. It can get into kernel. This weakness found in 2018 earlier stage.
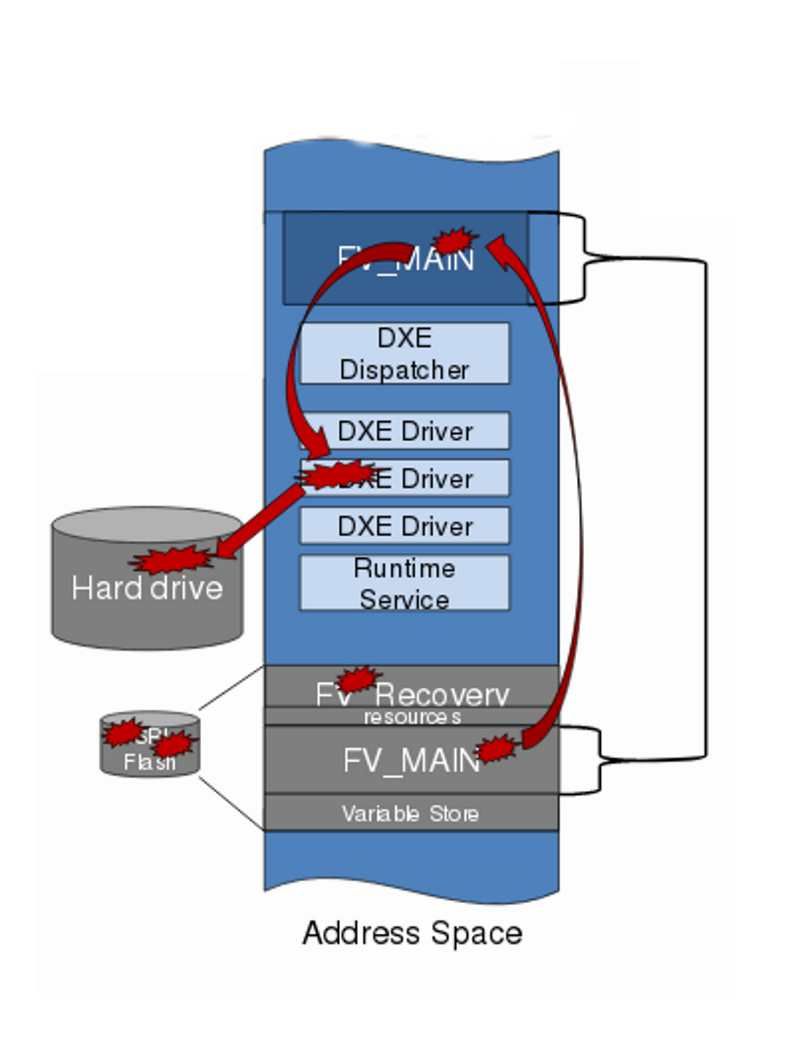
Vulnerability details: A flaw was found in hw. In certain processors with Intel’s Enhanced Indirect Branch Restricted Speculation (eIBRS) capabilities, soon after VM exit or IBPB command event, the linear address following the most recent near CALL instruction prior to a VM exit may be used as the Return Stack Buffer (RSB) prediction.
Non-transparent sharing of return predictor targets between contexts in some Intel(R) Processors may allow an authorized user to potentially enable information disclosure via local access.
Official announcement – For details, see URL – https://access.redhat.com/security/cve/cve-2022-26373