Preface: What is Kerberos authentication in database? Kerberos is a protocol for authenticating service requests between trusted hosts across an untrusted network, such as the internet. Kerberos support is built in to all major computer operating systems, including Microsoft Windows, Apple macOS, FreeBSD and Linux.
Background: The Oracle Advanced Networking Option is an optional product that provides enhanced functionality to SQL*Net. Its set of features provides enhanced security and authentication to your network, enables integration with a Distributed Computing Environment (DCE), and provides access to native directory services through Native Naming Adapters.
Vulnerability details: CVE-2023-21949 – Vulnerability in the Advanced Networking Option component of Oracle Database Server. Supported versions that are affected are 19.3-19.19 and 21.3-21.10. Difficult to exploit vulnerability allows unauthenticated attacker with network access via Oracle Net to compromise Advanced Networking Option. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Advanced Networking Option accessible data. CVSS 3.1 Base Score 3.7 (Integrity impacts).
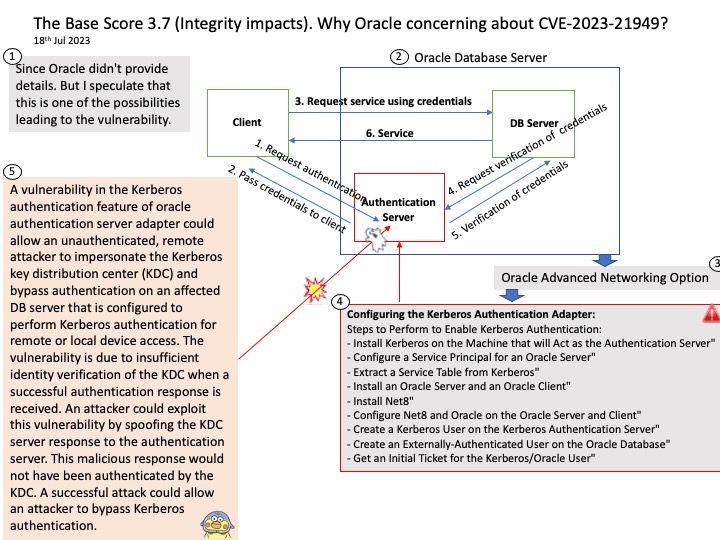
Since Oracle didn’t provide details. But I speculate that this is one of the possibilities leading to the vulnerability. For details, please refer to attached diagram.
Ref: A vulnerability in the Kerberos authentication feature of oracle authentication server adapter could allow an unauthenticated, remote attacker to impersonate the Kerberos key distribution center (KDC) and bypass authentication on an affected DB server that is configured to perform Kerberos authentication for remote or local device access. The vulnerability is due to insufficient identity verification of the KDC when a successful authentication response is received. An attacker could exploit this vulnerability by spoofing the KDC server response to the authentication server. This malicious response would not have been authenticated by the KDC. A successful attack could allow an attacker to bypass Kerberos authentication.
Official announcement: For details, please refer to the link – https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-21949