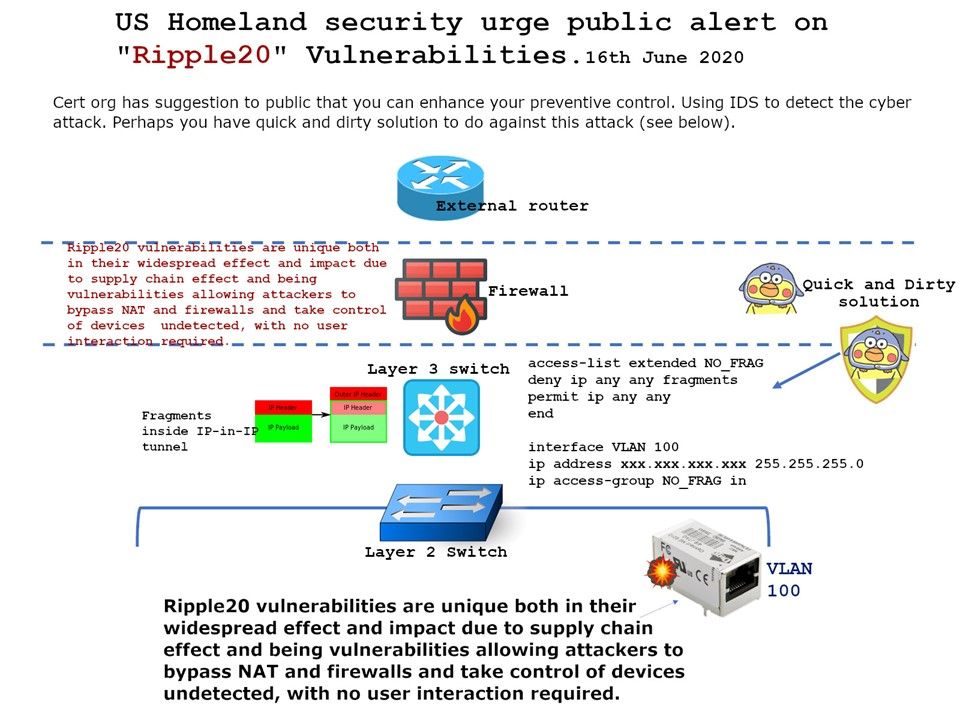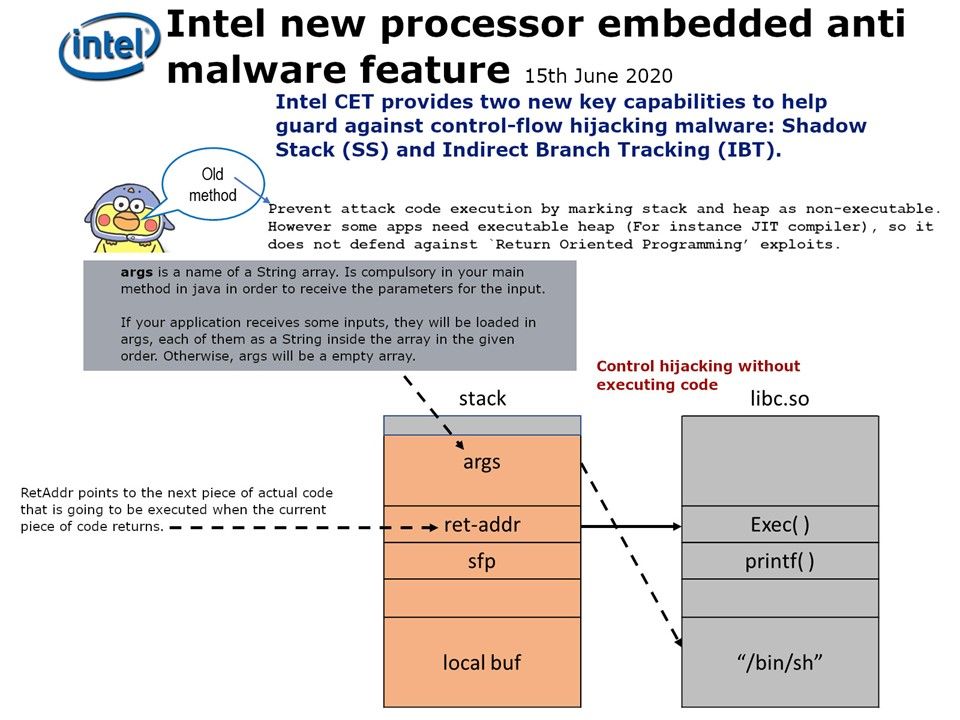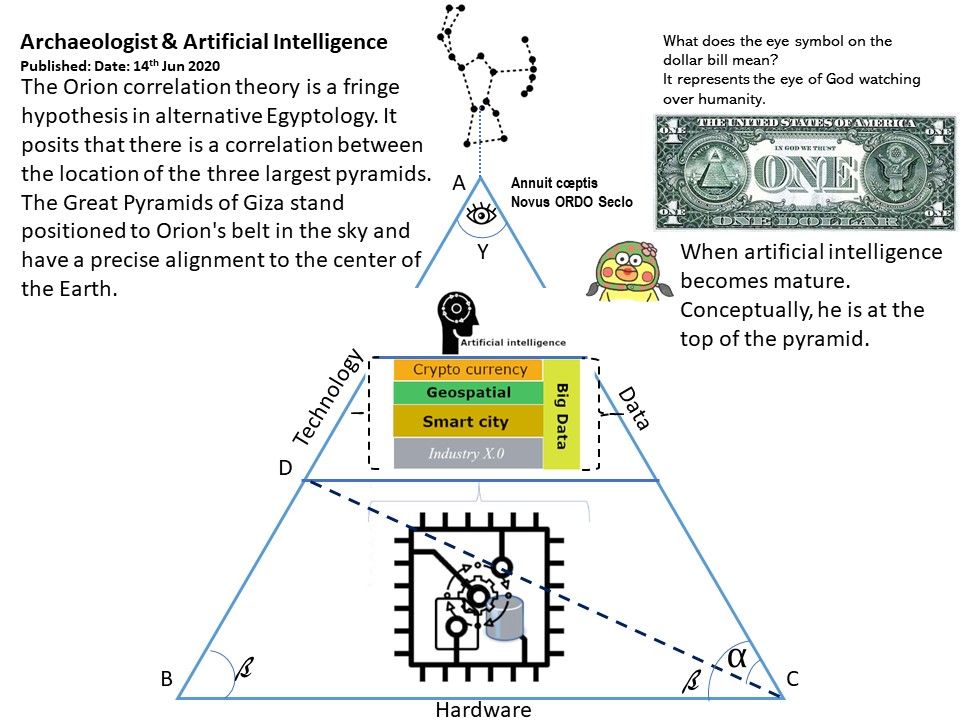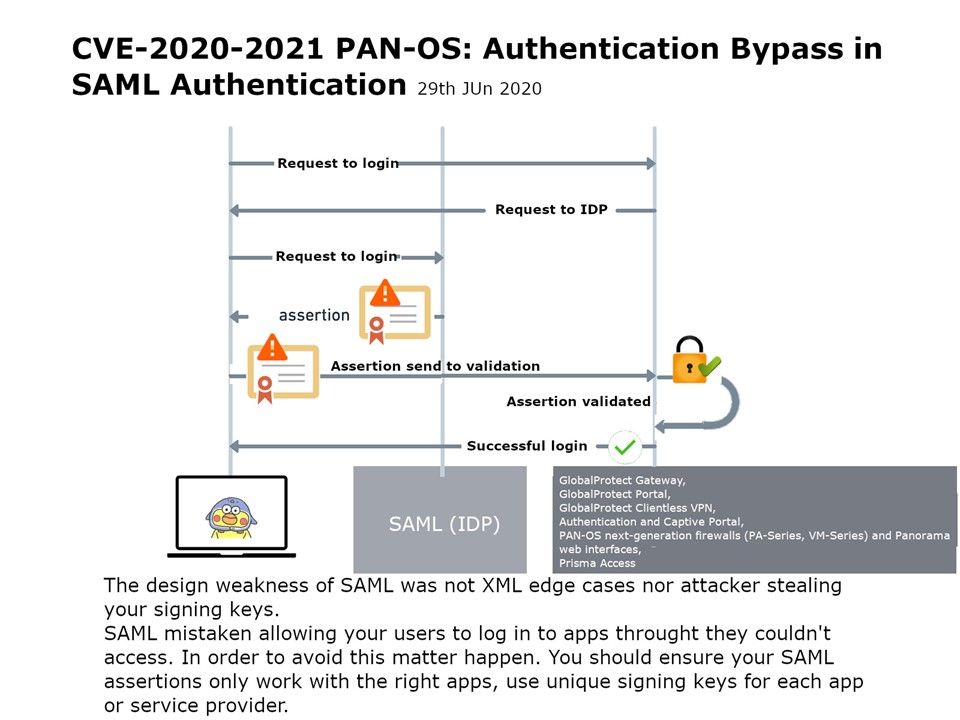
Preface: SAML implements a secure method of passing user authentications and authorizations between the identity provider and service providers. When a user logs into a SAML enabled application, the service provider requests authorization from the appropriate identity provider.
Design weakness: The design weakness of SAML was not XML edge cases nor attacker stealing your signing keys.
SAML mistaken allowing your users to log in to apps throught they couldn’t access. In order to avoid this matter happen. You should ensure your SAML assertions only work with the right apps, use unique signing keys for each app or service provider.
Palo Alto Releases Security Updates for PAN-OS: Authentication Bypass – details refer to following link. https://security.paloaltonetworks.com/CVE-2020-2021
.jpg?width=1920&height=1080&fit=bounds)


.jpg)