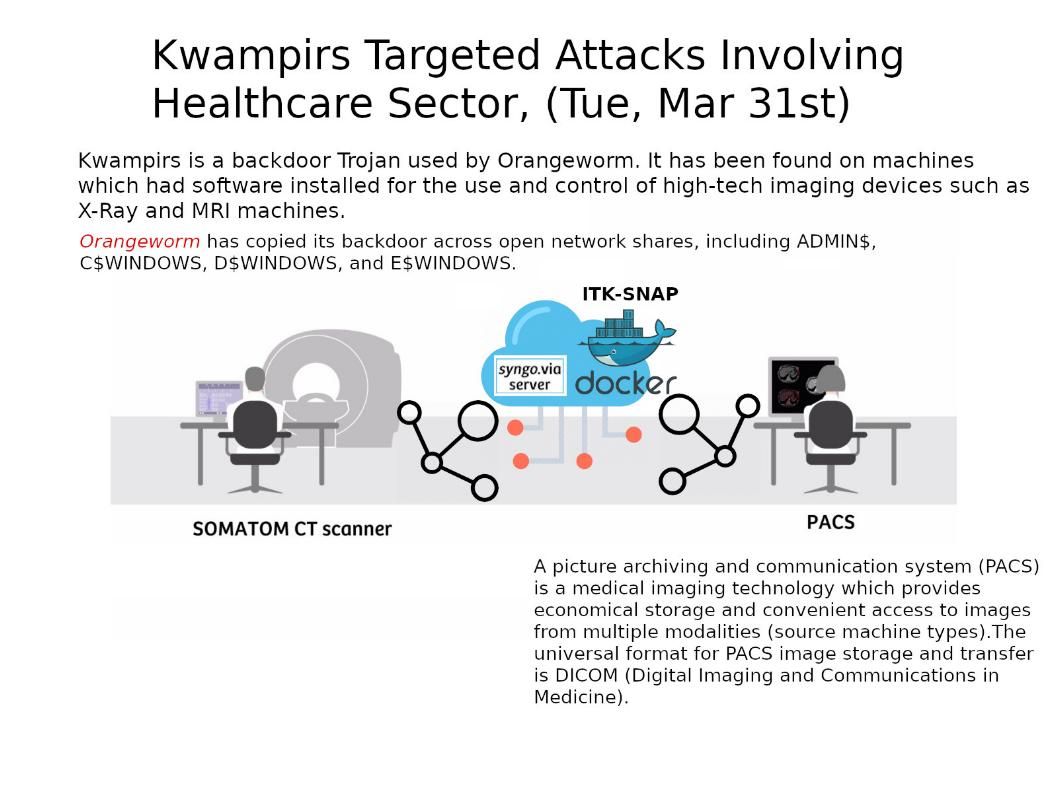
Preface: Orangeworm is a group that has targeted organizations in the healthcare sector in the United States, Europe, and Asia since at least 2015.
Synopsis: Why does Kwampirs fall into the “Advanced Persistent Threat (APT)” category?
- For tradition malware “click and action” attacks. APT attack not condct the similar action. Instead, APT merely do the infiltration on network and communicate with C&C peer daily. asking for updates.
- The APT malware rare to do the destructive action especially encrypting data. Ask victim to pay the ransome.
About Kwampirs : FBI alert that Kwampirs goal to implant the remote-access Trojan (RAT). His target include organizations that run industrial control systems (ICS), financial services firms, energy companies and healthcare institutions. As a matter of fact, The Kwampirs was used by Orangeworm group as a backdoor Trojan. It has been found on machines which had software installed for the use and control of high-tech imaging devices such as X-Ray and MRI machines in past. So it was not suprising with Cyber security Guru that he return to healthcare industry.
How did Kwampirs infiltrate my computer? There are several ways to distribute Kwampirs. For instance, by using email campaigns, fake software updates, untrustworthy third party software download channels and unofficial software activation tools. So only relies on Yara rules in IDS not a effective solution to avoid this attack. The observation proves that the internal access control of the 3rd party device is one of the effective channel.
Should you have interested of this matter, please refer to URL – https://www.infragard-la.org/wp-content/uploads/2020/02/FLASH-CP-000118-MW-TLP-GREEN-YARA-Rules-to-Identify-Kwampirs-Malware-Employed-in-Ongoing-Cyber-Supply-Chain-Campaign-Targeting-Global-Industries.pdf
By the way, we hope that the corona-virus will disappear in the world as soon as possible.