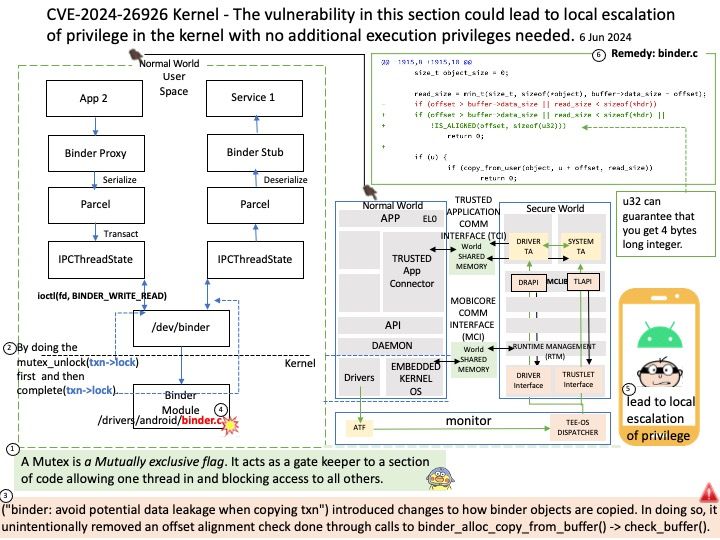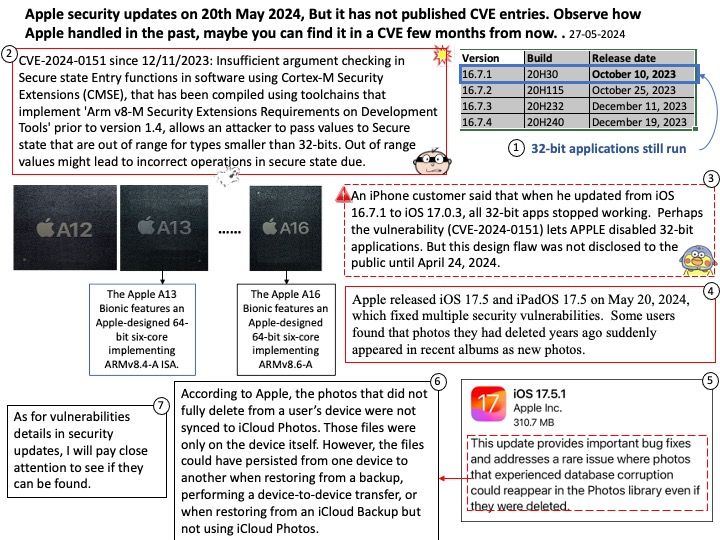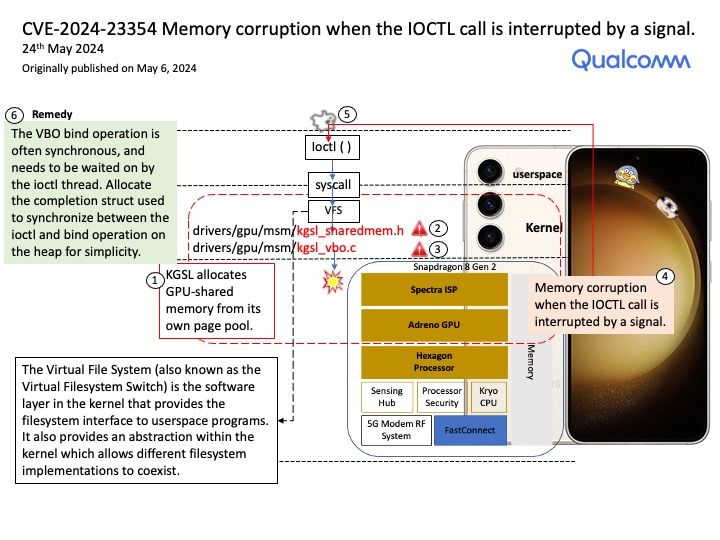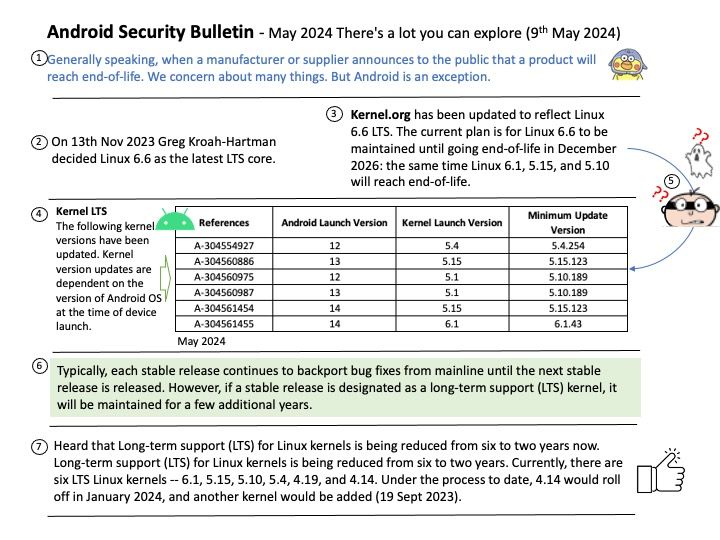
NVD Published Date: 07/03/2024
Preface: How is RTT measured in TCP? Measures the time from sending a packet to getting an acknowledgment packet from the target host.
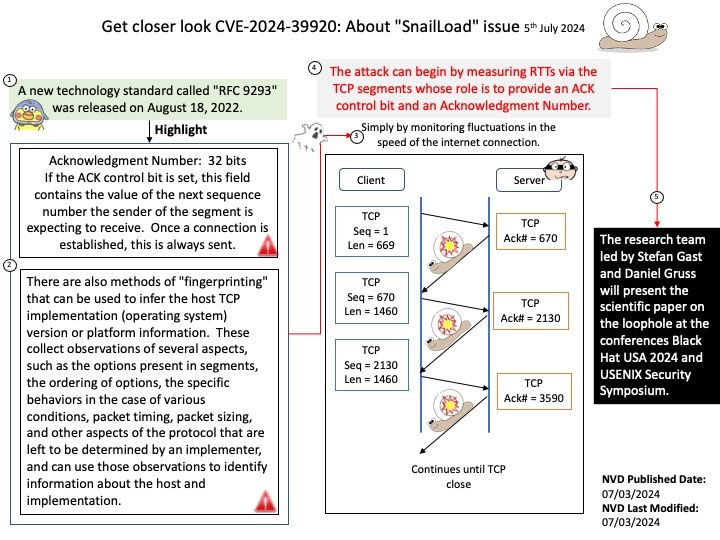
Background: A new technology standard called “RFC 9293” was released on August 18, 2022.
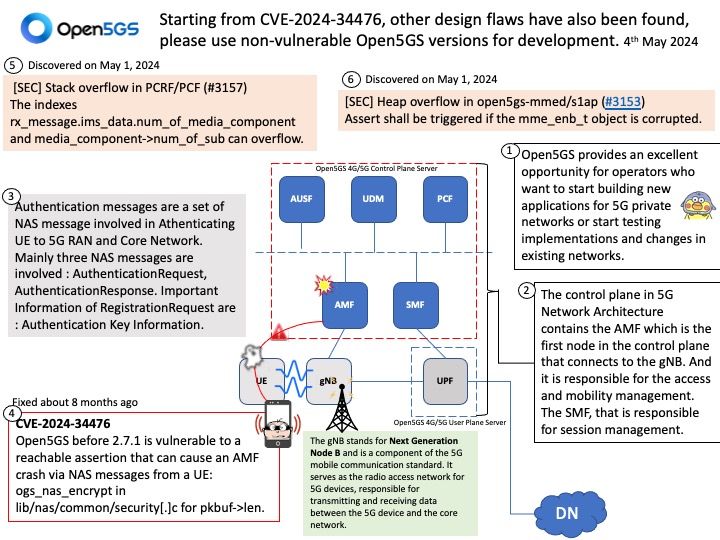
Highlight:
-Acknowledgment Number: 32 bits – If the ACK control bit is set, this field contains the value of the next sequence number the sender of the segment is expecting to receive. Once a connection is established, this is always sent.
-There are also methods of “fingerprinting” that can be used to infer the host TCP implementation (operating system) version or platform
information. These collect observations of several aspects, such as
the options present in segments, the ordering of options, the
specific behaviors in the case of various conditions, packet timing,
packet sizing, and other aspects of the protocol that are left to be
determined by an implementer, and can use those observations to
identify information about the host and implementation.
Vulnerability details: The TCP protocol in RFC 9293 has a timing side channel that makes it easier for remote attackers to infer the content of one TCP connection from a client system (to any server), when that client system is concurrently obtaining TCP data at a slow rate from an attacker-controlled server, aka the “SnailLoad” issue. For example, the attack can begin by measuring RTTs via the TCP segments whose role is to provide an ACK control bit and an Acknowledgment Number.
Official announcement: For detail, please refer to link – https://nvd.nist.gov/vuln/detail/CVE-2024-39920